OpenVPN peer-2-peer SSL/TLS not working
-
Hello,
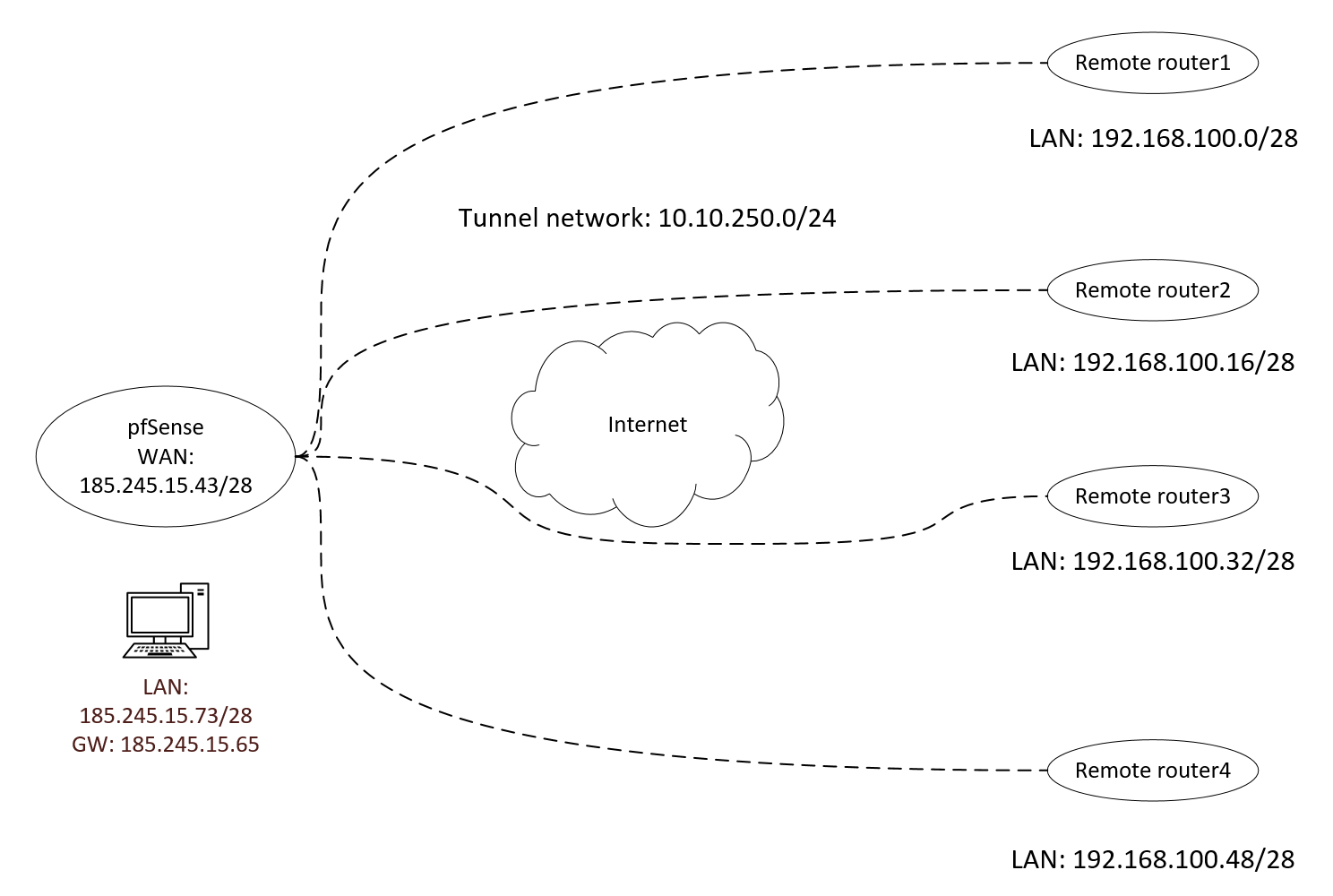
I'm setting up site to site ovpn connections to client's routers via SSL/TLS vpn way. I followed instructions but they are very coarse and unclear. I got tunnel interface address (10.10.250.1) and I can ping it from machine, but GW I get is DOWN and address assigned to it is not working. While defining VPN>OpenVPN>Clients I'm not sure do I have to assign one client for each location and add it's own interface (to get GW) or just one... In "Client specific override" I defined CN and remote network iroute. Since GW is marked down I cannot enter static routes (bring it up). Scheme is uploaded what I need to get connected. As mentioned, I can only ping interface of ovpn server from the PC and nothing else is coming up. I made new ovpn server, new certs and all from scratch again but result is the same. Someone please show how to configure this to work.
-
Not clear what you're trying to set up here at all.
@bbiketa said in OpenVPN peer-2-peer SSL/TLS not working:
I'm setting up site to site ovpn connections to client's routers via SSL/TLS vpn way
The drawing shows multiple sites.
Do you want a site to site to each remote routers? Or a site to multi-site?
Is pfSense the server or the client?@bbiketa said in OpenVPN peer-2-peer SSL/TLS not working:
I got tunnel interface address (10.10.250.1) and I can ping it from machine
Where? From which machine?
@bbiketa said in OpenVPN peer-2-peer SSL/TLS not working:
but GW I get is DOWN
Which one?
@bbiketa said in OpenVPN peer-2-peer SSL/TLS not working:
Since GW is marked down I cannot enter static routes
It's not recommended to add static routes for networks behind VPNs. The routing should be done by OpenVPN.
-
Well i need server that's on 185.245.15.73 to reach remote routers Lan networks and opposite. I don't need routers to communicate between each other. Customer's routers only support openvpn connections, no ipsec or similar. I was following the instructions here: https://docs.netgate.com/pfsense/en/latest/book/openvpn/site-to-site-example-configuration-ssl-tls.html
As much as i understood, peer-to-peer with shared key is only for single site to site.
Also i've never setup site to site over ovpn this way and it's quite confusing -
@viragomann
pfs is ovpn server yes. Remote routers are the clientsMachine i ping tunnel interface is the left one (server) on pic (185.245.15.73).
GW that's down gets automatically assigned IP 10.10.250.2 by pfs as soon as i add ovpn as interface and enable it
-
@bbiketa said in OpenVPN peer-2-peer SSL/TLS not working:
As much as i understood, peer-to-peer with shared key is only for single site to site.
Yes, it seems so. I've never tried, but to set up a site-to-multiple site you need to add client specific overrides for each client to configure the routing. To configure a CSO you need either a username or a certificates common name, which you are missing in a shared key set up.
If SSL/TLS setup is no option for you you would have to set up one OpenVPN server for each site-to-site connection, each listening on a different port.
-
@viragomann
Yeah, I've added client specific overrides as instructed. Should username and override have same name? I've set different name for user, but CN is the same as certs: for example i've set username: user1, but CN is client.user1 and in override is client.user1, should this create problems or it's ok? -
@bbiketa
That should be fine.
The override CN should match the cert CN.If you want to use the username in CSO you have to check "Username as Common Name" in the servers advanced settings.
-
@viragomann
hmm, ok,
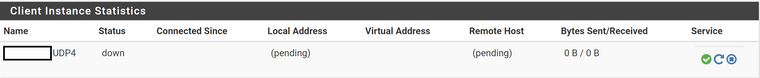
Also, when I enabled server's interface, it created GW too. Interface adress of ovpnserver is 10.10.250.1 and windows server machine can ping it. But what confuses me it also makes GW that's on 10.10.250.2 and it's down... I have no clue what this GW is for? Do I have to enable ovpn server's interface or so?It also creates this when I add "Client" under ovpn settings, it's constantly down. I entered everything as on the tutorial and chosen the correct cert with correct CN. Customer's router also doesn't work with TLS and I've disabled it (I know it's more insecure, but situation is how it is). Also when I add another client in "Client" with other cert it cannot even start the service for it.
-
@bbiketa said in OpenVPN peer-2-peer SSL/TLS not working:
Customer's router also doesn't work with TLS and I've disabled it (I know it's more insecure, but situation is how it is).
Can't believe that.
However, if so I'd set up a shared key site-to-site for each connection. So you would have to set up 4 OpenVPN servers, each listening on a unique port. -
@viragomann said in OpenVPN peer-2-peer SSL/TLS not working:
@bbiketa said in OpenVPN peer-2-peer SSL/TLS not working:
Customer's router also doesn't work with TLS and I've disabled it (I know it's more insecure, but situation is how it is).
Can't believe that.
However, if so I'd set up a shared key site-to-site for each connection. So you would have to set up 4 OpenVPN servers, each listening on a unique port.Well, I still don't know which kind of routers those are, but apparently they support .ovpn files too (they needed to enter all keys/certs seperately). In there I can setup TLS so I see no problem yeah.
BUT, yesterday I did make little step forward finally. I've setup server to push ifconfig and set it up to work in /30 mode of ip assigments. Now it assigns the same IP all the time and I can set it up as GW to specific network if needed, but I'll first test out if OVPN server is doing all the irouting properly where I specified remote networks in client specific override. I'm still unsure what does "Clients" part do there since I always have that tunell as down, as I posted in previous message and screenshot?
-
@bbiketa said in OpenVPN peer-2-peer SSL/TLS not working:
I'm still unsure what does "Clients" part do there since I always have that tunell as down, as I posted in previous message and screenshot?
I don't understand that screenshot. It shows a client instance status on pfSense, while you wrote you set up a server instance on pfSense and all clients are running on unknown router.
-
@viragomann So I basically need only client override settings for this right?
If i'm doing this with unknown clients that only indentify by cert (CN) (SSL/TLS) I just need P2P mode and Client Override Setting pointing to each remote network so that server knows where to route (iRoute)?
So... I don't need any static routes anywhere right, since only GW I can create is interface of server itself (10.10.250.1)? If I use persistent routes on windows machine, it ignores anything I write there and just goes by default route every time.I know this setting is confusing, but also this FW is setup so WAN is on differen public IP (different network subnet) and LAN is also public IP which is routed through FW (it's not NAT). On switch I have route that pointing to that LAN network through WAN interface. Maybe that's creating issues... I'm very unsure...