Print from OPT1 to LAN printer
-
Yes.. I never said anything about putting block rules below your any.. Block rules would need to be above a rule that allows any..
-
@johnpoz said in Print from OPT1 to LAN printer:
In your case the last rule would allow it, and no other rule above that would block it - so its allowed.
This is what confused me. I see that and think that because the any any is on the bottow, everything above it is ignored..
-
You didn't have any block rules - you only had allow rules!!
Dude... This is not difficult... Come up with your traffic pattern that you want to do something with.. Now walk down your rules top to bottom.. What rule triggers? On that traffic pattern - that is what happens... Once you hit a rule that matches, stop looking at any othe rules.
If you get to the bottm and and no rules match, then it would be blocked! Default Deny, if rule does not allow it.
-
Got it. So should the LAN have any blocking on it at all? Or just basically have the anti-lockout, and the allow any/any. (I am talking about my network only, where I want the LAN to be able to access anything on OPT1, and the internet..and anything on OPT1 to access the internet, but only the printer on LAN)
-
@5cub4f1y said in Print from OPT1 to LAN printer:
Got it. So should the LAN have any blocking on it at all? Or just basically have the anti-lockout, and the allow any/any
Depends - do you want to block your lan from doing anything? Here are my lan rules
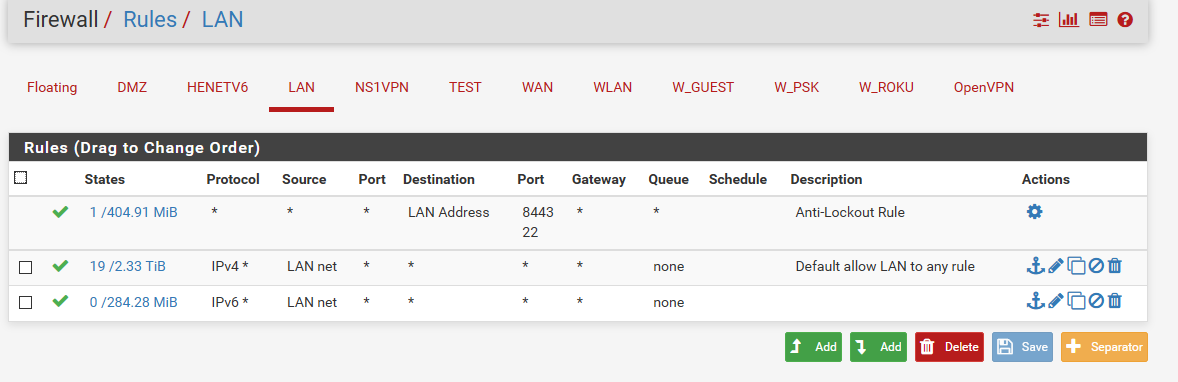
I split the IPv4 and IPv6 because sometimes I might block IPv6, etc.
-
No. Not that I can think of. Since I control all the devices on LAN (patch managment, security updates etc...) I am not as worried about vulnerabilities as I am with everything else on OPT1
-
If you have questions if your rules will do what you want.. Just come up with the example traffic pattern of what you want to do something with, and just walk down the rules to see what will happen.
-
@johnpoz Ah thank you. Thats what I now have.
-
@5cub4f1y said in Print from OPT1 to LAN printer:
@johnpoz Ah thank you. Thats what I now have.
Let's see, let's see!
-
LAN
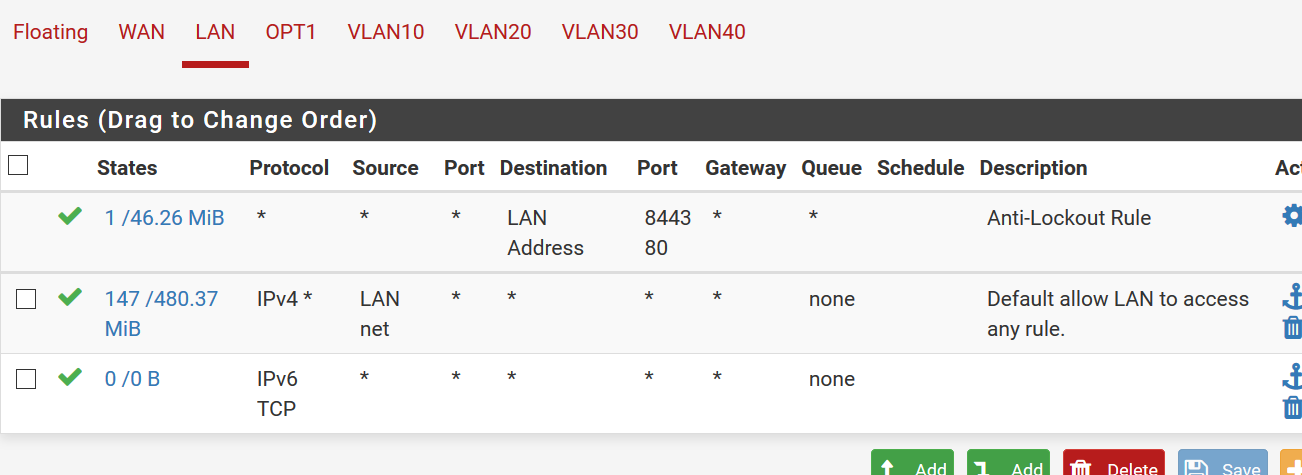
OPT1 I'm still figuring out, following the logic to see if these rules will do what I want them to do. Which is essentially NOT allowing OPT1 to access anything on LAN, except the printer. Still looks like this...
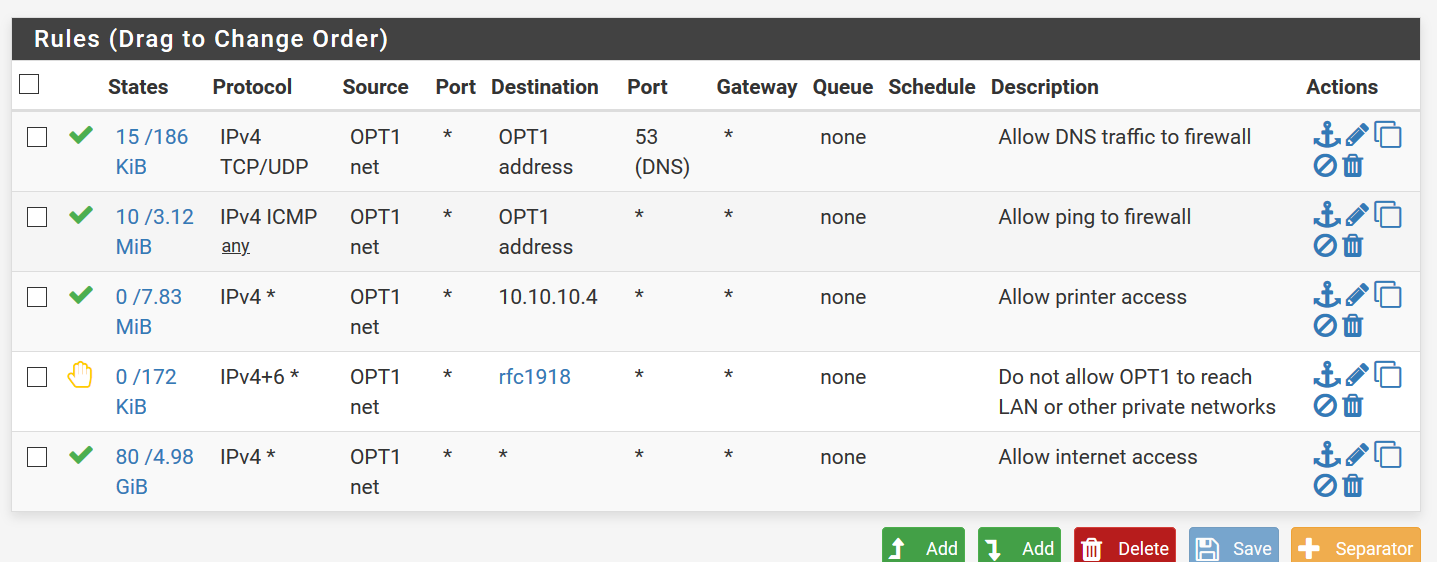
-
@5cub4f1y Yep, those rules look good. You might need a port number on rule number 3 on your OPT1 network, but probably not. Can you print something thru this rule, does it work?
Jeff
-
Yes the printer works from OPT1 hosts. I'm starting to wonder if having the printer on the LAN network makes the LAN network more vulnerable...might be easier to just put the printer on the OPT1 network since the LAN net can access anything there anyway?
-
@5cub4f1y Yeah, that's generally how to keep your "trusted" LAN network secure, don't let much of anything in like that. However, you are only allowing access to one IP address for one device, a printer, so it should be ok. Just keep the firmware on the printer up-to-date.
You're not like sitting next to North Korea or China, or Russia or anything, right? Somewhere with a whole lot of hacker/crackers? If not, and you trust most of your OPT1 hosts, you kinda can leave it the way you've got it right now - OPT1 access to the printer on LAN.
What I would make sure to do, however, is to put a REALLY good wifi password on your Orbi Mesh stuff. keep the firmware on it up-to-date. And maybe refresh/reset the password say every 2-3 months. Just to keep the bad guys out...
Jeff
-
@5cub4f1y said in Print from OPT1 to LAN printer:
I'm starting to wonder if having the printer on the LAN network makes the LAN network more vulnerable
Well the security question aside.. Sometimes it easier to just put the printer where its used most and how.. I have my printer on my wlan network, because it allows for the airprint to work.. And I can print from the lan without any issues, because don't use airprint from my wired lan network.
-
Great! Thank you guys! I'm understanding how this works a little better. I am learning networking and cybersecurity so I am wanting to eventually set this up so I can have a separate network/VLAN for a home lab, but that is later. Right now I just wanted to understand pfSense enough to not knock my wife off the internet...lol