VLAN on LAN vs on separate physical port
-
I have a 4 NIC Intel card in my pfSense box such that
- igb0 == WAN
- igb1 == LAN
- igb2 ==
- igb3 ==
- re0 ==
So I have at least 2 reliable ports available (discounting the Realtek onboard NIC)
I recently got myself a Cisco 3750X POE switch and wanted to set up VLANS for my cameras. I intend to have 2 cameras at the moment but want capability to increase to 4 at most. I also need WiFi access to this VLAN -- because I also intend to have a wireless video doorbell (house does not have existing wiring for doorbell). This VLAN will not have internet access. But it needs to be able to record video to my proxmox box (which runs a Shinobi container -- for camera access)
Once I set this up successfully, I also intend to create 2 or 3 more VLANs for:
- IOT VLAN
- Guest VLAN (with WiFi --- maybe no hardwired ports for Guests)
- MGMT VLAN (to move over my IPMI ports of my servers)
My questions are:
- Should I use igb1(LAN) as the parent interface when creating VLANs or the free physical port?
- What's the difference between using the LAN or a separate physical port as the parent interface?
- If I choose a separate physical port as the parent, I can at most create 2 VLANs -- Can I then create the 3rd & 4th VLAN based on LAN or any other VLAN (Camera & IOT)
For Wifi needs in these VLANs:
- Since I need WiFi for the Camera VLAN, will I need a separate Access Point that is connected to that VLAN or can my AP on the main LAN handle it?
- Eventually when I create my Guest VLAN -- will I need yet another separate Access Point to provide WiFi to that network (given that I don't want Guest VLAN devices to access my primary network)
Basically will I require a separate AP for every VLAN that needs WiFi?
Thanks for your help in advance !
-
@Inxsible You typically setup/move VLANs to their own physical network ports when the hosts on these VLANs are considered high traffic.
Chatty network devices like cameras, video streamers, NAS boxes, cloud backup stuff and servers are usually devices that behave like this.
So, unless you've got dozens upon dozens of guest devices all on and connected at the same time, or tons of traffic moving over your management VLAN, you can typically put these 2 and your LAN on the same physical port, VLAN separated, obviously. Make sure you have an access point and switching gear that supports VLANs.
IOT and cameras I would put on their own interface. If they're on their own interface, then you don't technically need to VLAN them, but you will need extra switching gear behind the scenes. So, to save some money and space, VLAN that stuff up on it's own port.
Jeff
-
@akuma1x said in VLAN on LAN vs on separate physical port:
@Inxsible You typically setup/move VLANs to their own physical network ports when the hosts on these VLANs are considered high traffic.
Thanks @akuma1x . That makes sense.
I will put IP Cams and IOT on their own ports and Guest and Mgmt based on LAN.
I will need to find an AP that supports multiple VLANs.
-
@Inxsible This one, right here:
https://www.amazon.com/Ubiquiti-Unifi-Ap-AC-Lite-inal%C3%A1mbrico/dp/B015PR20GY
All I have to do with this one, after initial setup, is to check it every once in a while for firmware updates. Otherwise, rock solid performance.
Jeff
-
@akuma1x
Thank you again. Unifi was on my list of APs to buy. I was just wondering if I need more than 1. I'll look into this one in terms of range etc.Since I have separate physical ports for my Cameras and IOT (as discussed above), what's the difference between creating a separate network on those ports (like a regular LAN2 for eg) -- vs creating a VLAN first using that port as parent and then assigning it?
Can I still isolate the regular network similar to the VLAN and vice-a-versa ?
-
@Inxsible You can isolate networks on different pfsense ports all day long. But, then you have to have separate switches to plug those interfaces into. To minimize the amount of switches you need to install, VLANs can work with a single smart/managed switch, all you have to do is program it properly.
Do you have any of that type of switch gear installed or on hand?
Jeff
-
@akuma1x said in VLAN on LAN vs on separate physical port:
Do you have any of that type of switch gear installed or on hand?
Yeah, I have a 48 port Cisco managed you switch so I'd have to VLAN the cameras because I use that switch for my main network too.
I also have another dumb TPLink 16 port switch switch lying around as well that I can probably use for the IOT network unless I have POE devices on that as well
-
@akuma1x said in VLAN on LAN vs on separate physical port:
@Inxsible You can isolate networks on different pfsense ports all day long. But, then you have to have separate switches to plug those interfaces into. To minimize the amount of switches you need to install, VLANs can work with a single smart/managed switch, all you have to do is program it properly.
Hi again @akuma1x , I think I confused myself a bit there so I thought I'd rather clarify.
Since I only have 1 switch that supports VLANs currently, I cannot create a separate regular LAN network as I use that same switch for my main LAN network.
Can I still create a VLAN based on a different physical port and use it with the same switch as my main LAN switch?
Or does the parent interface for my Camera VLAN has to be my main LAN in order to use the same switch?
-
@Inxsible Ok, I've got Ciso switches too, on my main LAN network. On this same network, I've also got a GUEST VLAN running on tag 8.
Here's my LAN network settings on the switch, ALL ports are set to UNTAGGED. VLAN ID says 1, but I think that's a Cisco default number, I'm not actually running that tag anywhere on my network.
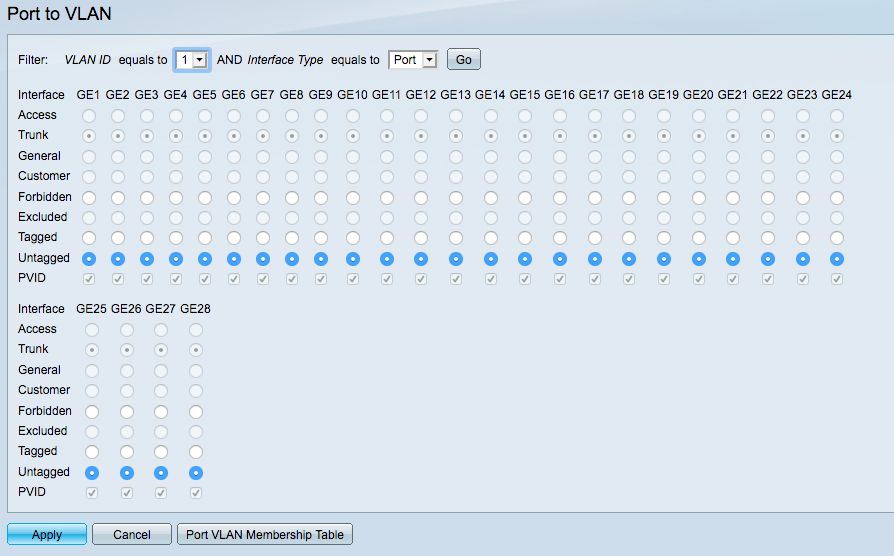
Here's the GUEST settings, using VLAN tag 8, on the same switch.
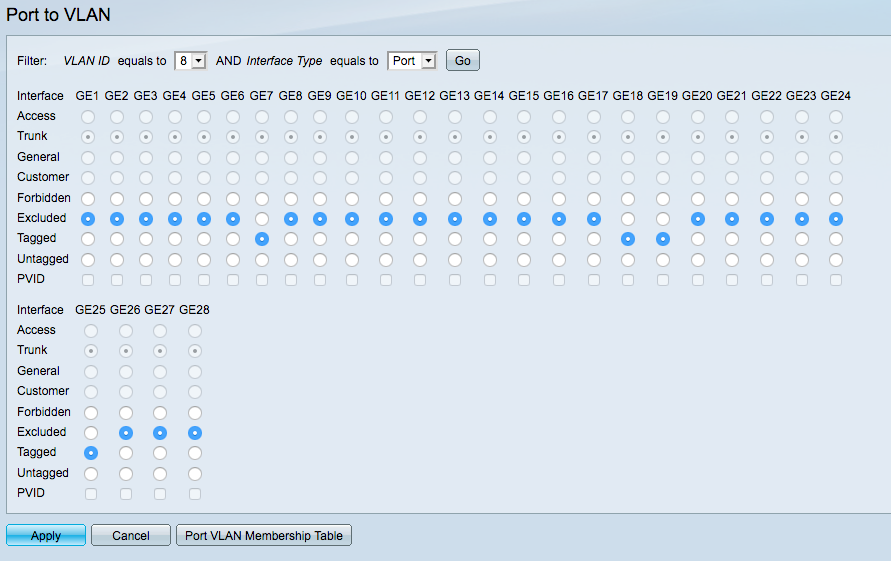
Ports GE7, GE18, and GE19 have wireless acess points plugged into them, using VLAN tag 8, and port GE25 runs back to my pfsense LAN port.
Hope that helps.
Jeff
-
@akuma1x said in VLAN on LAN vs on separate physical port:
Ports GE7, GE18, and GE19 have wireless acess points plugged into them, using VLAN tag 8, and port GE25 runs back to my pfsense LAN port.
And GE25 is a separate physical port than the one which runs LAN on pfSense for you? I am just trying to confirm if I can have a VLAN running on a physical port which does not have a regular network on it. If I can, I can physically separate my Camera traffic from my main LAN traffic on the router -- but still use the same switch with separate VLANs for my Camera traffic and my LAN traffic.
Not sure which model switch you have but I don't have a fancy WebUI for my 3750X switch -- Well I did get the WebUI installed, but it has no options to configure VLANs etc. Everything has to be via CLI. :) I created a thread on spiceworks to see if someone knows of a version which would support managing VLANs via the WebUI for 3750X -- https://community.spiceworks.com/topic/2286162-cisco-3750x-webui
I also have only 1 AP running DD-WRT and it supports VLANs too. So I intend to run all VLANs via a single cable to the AP but then have the AP run tagged traffic to my 2 wifi doorbells. Other wireless devices would continue to run untagged traffic on the same AP.
The cameras would be POE and connected to my patch panel/switch via Ethernet.
-
@Inxsible The switch is a Cisco SG300-28P. So, it's 28 ports, all running the LAN network from pfsense, with the 4 individual ports also carrying the GUEST VLAN tag 8. Three of these 4 ports are plugged into Unifi access points, all running LAN and GUEST VLAN8 traffic on 2 separate SSIDs.

Port GE25 carries both LAN and GUEST VLAN8. This port goes back to my pfsense LAN port. I couldn't imagine doing this without a WebGUI on the switch, but it must be possible.
So, yes, you can run two separate network ports on your pfsense box - 1 for LAN and the other for CAMS. Just make sure you activate 1 of the extra ports (igb2), I think pfsense will call it something like OPT1. Then all you have to do is go create a new VLAN, call it something like CAMS, and give it a VLAN tag, and pick the parent interface of OPT1 port. You have to do this two step process, you can't just simply create a new VLAN interface, it has to "ride on top of" an existing physical interface.
Plug that OPT1 port into the Cisco switch, with a tag on that switch port, then put the VLAN tags on the other switch ports where you plug in the physical camera network cables.
Jeff
-
@akuma1x said in VLAN on LAN vs on separate physical port:
You have to do this two step process, you can't just simply create a new VLAN interface, it has to "ride on top of" an existing physical interface.
Thank you yet again. I will create LAN2 on igb2 first and then run the Camera VLAN on top of that.
-
I have now created LAN2 -- as a dummy network just so that I can run the CAMERA VLAN on top of it. Do I need to enable the DHCP server on the LAN2 and assign an IP range even though I don't intend to use that network? I have already enabled the DHCP on the CAMERA VLAN.
-
The cameras I've set up used static addresses. In fact, just to configure the static address I had to create a static ARP and use that to connect to the camera or I had to use the app that would find the cameras and then could configure them. At no point was DHCP ever used for the cameras.
-
@JKnott said in VLAN on LAN vs on separate physical port:
The cameras I've set up used static addresses. In fact, just to configure the static address I had to create a static ARP and use that to connect to the camera or I had to use the app that would find the cameras and then could configure them. At no point was DHCP ever used for the cameras.
Advantage of using the Static ARP over DHCP IP reservation on the VLAN interface ?
In DHCP, after you have the cameras/devices setup, you can provide a static address outside the DHCP range. So you wouldn't technically need DHCP -- but it does become easier when first setting up the device to have DHCP turned on. We can immediately get an IP once connected, configure the device & set a static IP address outside the DHCP range.
-
@Inxsible said in VLAN on LAN vs on separate physical port:
Advantage of using the Static ARP over DHCP IP reservation on the VLAN interface ?
The static ARP was used only to configure the IP address. The cameras did not support DHCP and they had no address out of the box. So I would manually create an ARP entry with an IP address, so that I could use a browser to configure the address. After that was done, it was ready for service and the NVR configured for all the cameras. As I mentioned, there was also an app to configure the cameras, but I found it wasn't always reliable, whereas the static ARP method always worked.