Port firewalled automatically
-
Hi guys,
I have a PBX sending SMDR (phone call logs) to a TCP port on a Linux box (using nc to read the logs) over IPSEC.
This works OK but after a while the port starts getting blocked by the "default firewall rule". Even if I go and manually explicitly allow the port it still gets blocked (by the way I have rule to allow all IPSEC traffic).
If I change the port to send the data to, then everything starts working again OK (don't need to change any rules because as I said all the IPSEC traffic is allowed by default)
Could there be a setting somewhere that blocks the port due to the continuous flow of data?
Thanks!
-
no,
more likely trouble on your smdr
what you see on the firewall log are probably packet arriving after the connection’s state has been removed -
Hmmm....
Data is not flowing though.
And even if I reboot the Linux box and the Avaya PBX data flow is not restored.
I need to go and change the port on PBX and on nc in Linux... -
copy here the firewall logs,
try with
Go to System > Advanced
Click Firewall & NAT
Set ‘Firewall Optimization Options’ to Conservative -
Hi,
Sorry for taking a while to reply. Was waiting for the problem to reappear...
here is what I see in the logs:
Sep 8 10:13:09 IPsec Default deny rule IPv4 (1000000101) 192.168.2.50:4238 192.168.8.5:1936 TCP:A
Sep 8 10:13:19 IPsec Default deny rule IPv4 (1000000101) 192.168.2.50:4238 192.168.8.5:1936 TCP:A
Sep 8 10:13:29 IPsec Default deny rule IPv4 (1000000101) 192.168.2.50:4238 192.168.8.5:1936 TCP:A
Sep 8 10:13:39 IPsec Default deny rule IPv4 (1000000101) 192.168.2.50:4238 192.168.8.5:1936 TCP:A
Sep 8 10:13:49 IPsec Default deny rule IPv4 (1000000101) 192.168.2.50:4238 192.168.8.5:1936 TCP:A
Sep 8 10:13:59 IPsec Default deny rule IPv4 (1000000101) 192.168.2.50:4238 192.168.8.5:1936 TCP:AAnd here are my firewall rules for IPSec interface:
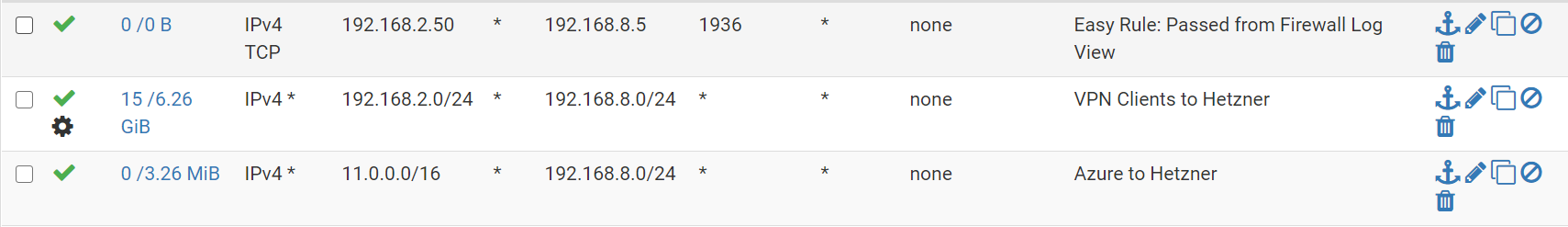
I added the first line to explicitly allow the TCP 1936 port but it gets ignored
Note that the logs just keep filing with lines like this every 10 seconds - so it means that the PBX is actively trying to send the data.
I changed the Firewall Optimization Options to Conservative and rebooted pfsense but didn't fix it.
In the past I had port 1935 setup and it was working for 2-3 days. Then it stopped and moved to port 1936 but again it stopped. Now I changed the port back to 1935 (which was blocked) and it works again. So it seems something is blocking the ports for a specific period. If traffic stops on that port - then it starts working again.
-
is 192.168.50.0/24 the ip of the ipsec interface?
what's 11.0.0.0/16 ? does it generate traffic on the same interface?something is wrong
maybe you have something on the floating tab?
remember that floating rules and NAT rules have precedence over firewall rules
the first rule overlap the second rule, and state say 0/0 so it was never used
a complete screenshots is needed to understand , if you have sensitive data just edit the image and delete ip from it -
I have 3 sites:
Office: 192.168.2.0/24
Hetzner servers: 192.168.8.0/24
Azure servers: 11.0.0.0/16The PBX is located in the Office: 192.168.2.50
It is trying to write data to the Hetzner network and a Linux box running in: 192.168.8.0/24 (192.168.8.5 specifically)The only floating ones I have are from Ban Lists on PFfBlockerNG and as you see they affect the WAN interface not the IPSec one:
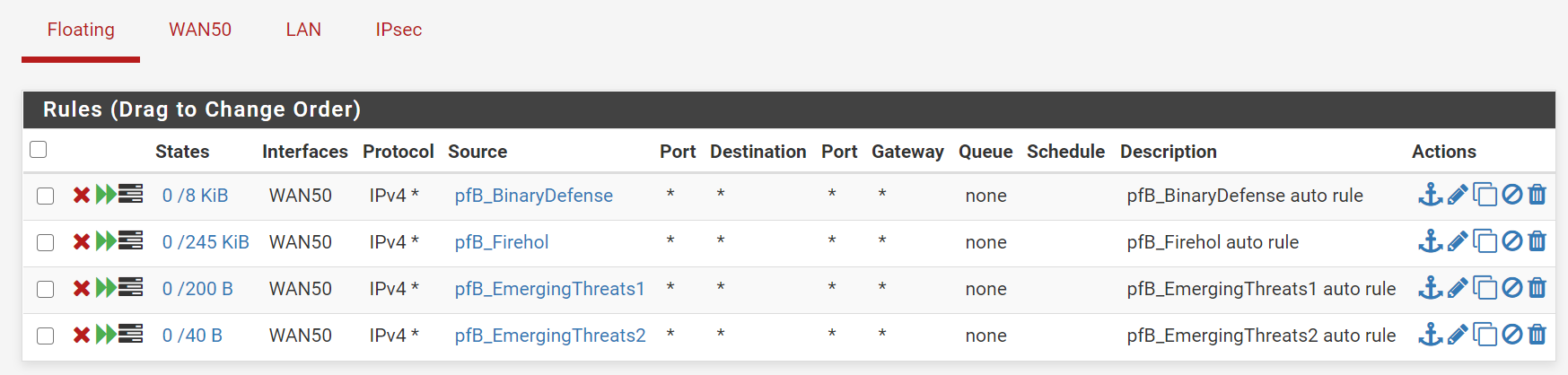
You are right about overlaps, that's what I assumed that the first one is prioritised and it shouldn't be 0/0 - but it seems that the IPsec rules are overridden. The traffic is purely over the IPSec network though as you see both are private range IPs (192.168.2.50 and 192.168.8.5)