Multiple OpenVPN Servers
-
Is it possible to create two OpenVPN server on PFSense? Currently I have a vanilla OpenVPN with UDP port 1194. However, many Public WiFi Hot Spots e.g Dunkin Donuts block anything but port 80 and 443. Can I create an additional server using TCP 443? Most hot spots allow TCP 443 traffic. Will I need to port forward on PFSense, and if I do, will that mess anything up? Thanks
-
You may run as many OpenVPN servers as you want as long as they are listening on different IP / port combinations.
You can set up an additional server listening on port 443 TCP.@FrankZappa said in Multiple OpenVPN Servers:
Will I need to port forward on PFSense
You can set the server to listen on the WAN IP 443 TCP, so no forwarding is needed.
Since you have to configure the protocol (UDP or TCP) in the OpenVPN settings the only option for using both is setting up an additional server.After you can configure your clients to connect to the TCP server if the UDP connection fails.
-
After you can configure your clients to connect to the TCP server if the UDP connection fails.
To do that, you'd have to copy over some things from the other OVPN server settings like the DH Key and make the exact same settings crypto wise.. You have to define a second, distinct tunnel network though, it has to be another one then the one you defined for the UDP server. But if you don't think you'll have more then 120 clients at the same time
 you can easily split the tunnel network in half (if you used a /24 on the udp server) and use one half of the /24 as /25 (or even a /26 for each if ~60 clients are enough). Makes routings easier in the long run :)
you can easily split the tunnel network in half (if you used a /24 on the udp server) and use one half of the /24 as /25 (or even a /26 for each if ~60 clients are enough). Makes routings easier in the long run :)But if you do that, you can modifiy your client configuration, add a second "remote" line with <your_ip_or_dns> 443 tcp instead of 1194 udp and modifiy the timeouts for a bit and have one client configuration for both servers that switch automagically after ~10-15s if the server is not responding so it retries with 443/tcp.
-
Thanks JeGr. So what would the line look like in the .ovpn file if I set up a second "remote" line (assuming it's in the .ovpn file)? I dont ever plan on having more than 2 connections at the same time to my server. Most of the time, it will only be me.
-
I feel you :) Almost the same with me.
Then just do that:
- duplicate (that works since 2.4.5! great!) the current VPN server
- choose protocol TCP
- choose port 443
- TLS Key should already be the same so no copy&pasta
- All other things (certs etc.) should be the same, too
- If you have a /24 tunnel network, just use x.y.z.128/25 here instead of .0/24
- everything else should already be fine
- save
now edit the first one (the udp/1194) and edit the tunnel network from .0/24 to .0/25.
That's how you now have a single /24 split between both servers and your connection always originates from the x.y.z.A/24 network. So you can use that in any rules for access from/to the VPN network.Now have a look at your local client configuration and fire up that ovpn file.
- search for the
remote <ip or ddns> 1194 udpline - duplicate it
- modifiy the second line to `remote <ip or ddns> 443 tcp
- check for a
verb statement(most commonly you won't have one) - if there's one check what level it is (verb 0? verb 1)
- change or create a new line to
verb 3so you get more verbose information at dial in if something doesn't work - 3 is always good to have without exposing vital information (also good for the server side) - if you want a fast switch from UDP to TCP in case it fails you can also add or modify:
verb 3 keepalive 10 30 connect-timeout 15With decreased keepalive, connection loss will be detected sooner. The timeout don't make you wait for 30-60s until it tries re-connecting.
You can play around with them as you like but don't set them too small, as that can also trigger a re-connect for a simple lag/connection hiccup.
-
@FrankZappa said in Multiple OpenVPN Servers:
Most of the time, it will only be me
If this is just for remote access for you.. There really is little reason to go through all the copy of config info over into the server and edit your already working client ovpn file, etc.
Just fire up your new instance, and export that config file.
Now you have 2 different configs, one that points to udp and other that points to tcp.. That way you can just use the UDP normally - but if you run into somewhere that is not working you can try the tcp one.
-
Thanks Johnpoz. I think that might be easier. It's what I did with my Asus router. Although JeGr's solutions sounds pretty cool as well.
Thanks to both of you.
-
Yeah you might want to do something like what he suggests if you have a lot of users that already have a config file. And just easier for them to edit it adding 1 line, or if you have common config file you could send out, etc.
But if just for your own use, just 2nd instance with its own setup seems easier to me.. I have a few edited ovpn files that do stuff like force all traffic or just route the specific networks, etc.
So sure you can get pretty fancy with different options and configurations.
-
@JeGr ,
4 years later, ... thanks! I went with the two separate client profiles option and your server-side instructions were perfect!
Question: I noticed that using a single vpn account I can log in once to each of the vpn servers. For example, I logged in from device A to 443 and device B in to 1194. A vpn server is not happy when both devices A & B try to log onto the same server using the same account. Is there a setting to allow multiple sessions per account?
Thanks!
Gary
-
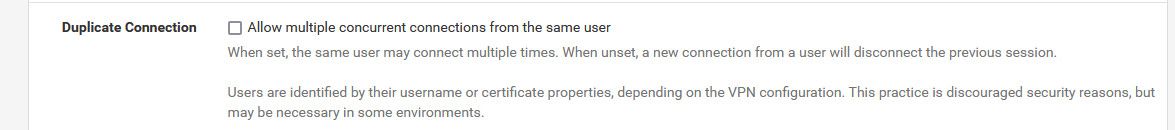
@garyn said in Multiple OpenVPN Servers:
Is there a setting to allow multiple sessions per account?
This one
-
Thank you! And, I really should have seen that, ... doh!