Don't show traffic pass through /var/log/filter.log
-
Hi all,
With : PfSense 2.4.4-RELEASE-p2, FreeBSD 11.2-RELEASE-p6
I get no get traffic from determinate sub-net, and not showing traffic in: /var/log/filter.log (pass or block), neither if i capture the packet traffic (PCAP)
But i see traffic with tcpdump:
tcpdump -ni em0 src x.x.x.x | grep 8.8.8.8
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on em0, link-type EN10MB (Ethernet), capture size 262144 bytes
16:12:07.744874 IP x.x.x.x > 8.8.8.8: ICMP echo request, id 55561, seq 0, length 64
16:12:08.746726 IP x.x.x.x > 8.8.8.8: ICMP echo request, id 55561, seq 1, length 64I already checked the routes, are right.
So, the traffic can't get through this firewall, and i don't no why?!
Any ideas , how troubleshoot what is going on?
Thanks !
-
You mean you have a downstream network? Why are you hiding rfc1918 address?
the packet capture is the same as tcpdump - so you saying that is not working while tcpdump does makes no sense at all.
Unless your listening the wrong interface, or on a vlan or however yours setup need to be in promiscuous mode...
Some more details of your setup would be helpful in helping you.
-
Hi johnpoz, thanks for reply
The source of the traffic is behind an MPLS from a service provider. (i think is that you refer about downstream network)
I don't understand neither about tcpdump and packet capture, maybe packet capture is slow, i don't know.
I verify the interface, it's listening the right one.
What another information will be useful ?
Thanks for help
-
Well the packet capture used via the gui, is just using tcpdump.. So doesn't make any sense that you would see traffic in tcpdump doing via cli/command line but not seen in packet capture gui.
-
Ok, thanks.
There is a command to show the packet that are drop, and not passing through the rules?
-
Huh? packet capture will show you everything being seen on the interface that meets your criteria set in the capture, IP, port, protocol, etc. Has nothing to do with if rules would pass the traffic or not.
-
johnpoz,
In GUI (Diagnostics -> Packet Capture) if i capture with filter : 10.13.0.20 , 8.8.8.8 . No output:
 image url)
image url)But in Cli : tcpdump -ni em0 host 10.13.0.20 get output
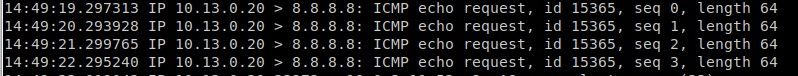
But independently of this, and this what i don't understand : **the packet 10.13.0.20 -> 8.8.8.8 : icmp no should match with the "deny" default rule ??? (at least) or "pass" if it match with another rule **
Thanks
-
What are you settings on the gui capture?
What is this interface em0? Do you have vlans setup on this interface?
Does the gui capture anything?
-
What are you settings on the gui capture?
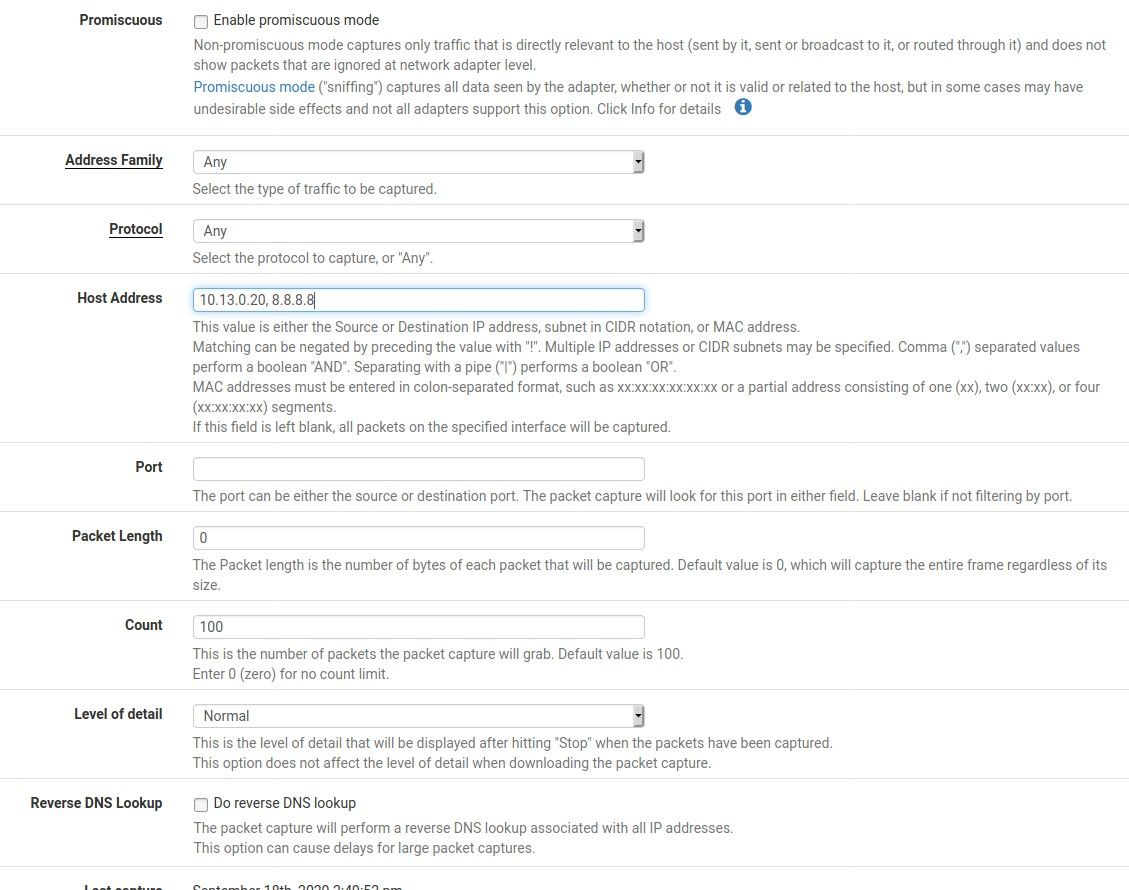
What is this interface em0? Do you have vlans setup on this interface?
em0 (internal), no vlans
Does the gui capture anything?
yes, capture something similar, for example :
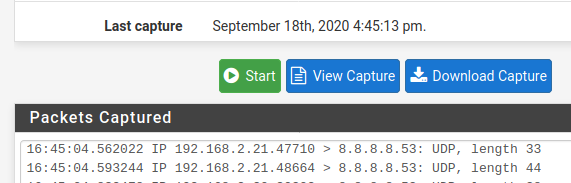
Thanks
-
@johnpoz,i realize that in gui put the wrong interface:
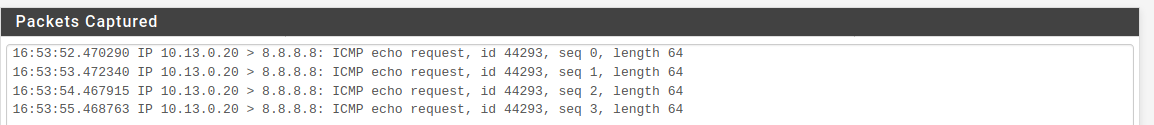
Now i see on GUI, but still no show "deny" or "pass" traffic on /var/log/filter.log
Thanks
-
Ok so the traffic is getting there.. And what do you set in logging. By default pass stuff is not logged. If you want passed traffic to be logged you would have enable that.
Did you turn off the default deny logging?
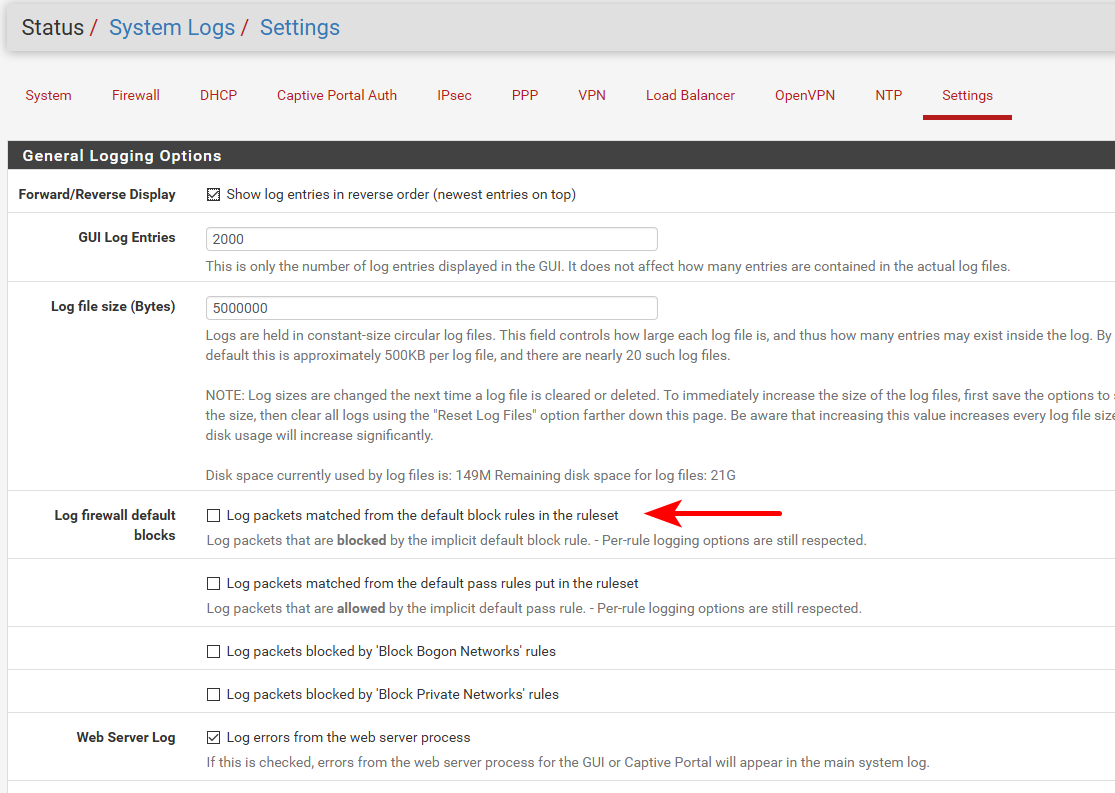
I have it off for example - because I only want to log specific stuff.
What are you rules on this interface? Do you have any rules on your floating tab?
-
Yes, firewall blocks logs are enabled
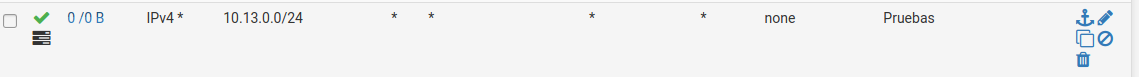
We have a lots of rules (floating and not floating), but for this and for diagnostic propose we have a floating rule:
-
Well that rule is not getting any hits. see the 0/0 - do you have quick enabled on it.
Is the traffic passing or not passing? Are you natting that, etc..
Nobody can really help you point out what you might have configured wrong when you show little tiny snippets of your setup without seeing the whole picture, etc.
Do you have quick set on that rule in floating? Do you have the correct interface selected? What other rules do you have above that in floating, what rules do you have on the actual interface, etc.
Is this 10.13.0/24 network downstream network? Or is that network directly attached to pfsense? If its downstream did you setup pfsense to nat it? Does pfsense know how to get to it via some other gateway? It could be just sending it out your wan without natting it, or not knowing how to send the traffic back even if there is an answer to it, etc.
I take it the actual problem is this 10.13.0.20 is trying to ping 8.8.8.8 and you get no answer? If its a downstream network and your not natting it, then no 10.13.0.20 wouldn't ever get to 8.8.8.8, even if you allowed it.. There are many pieces to this puzzle that are missing - for use to help you figure out what the actual problem is.
-
On these policy:
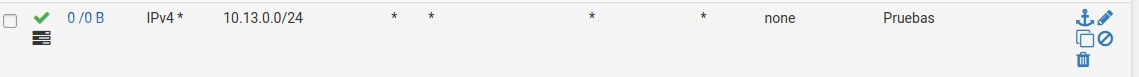
On "0/0 B" :
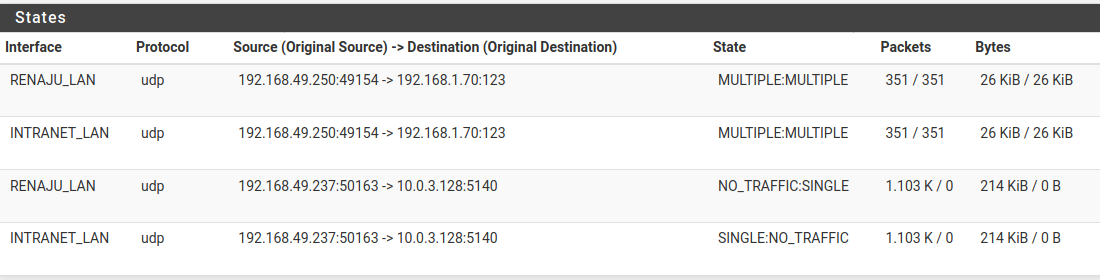
That's weird, i never use itYes, the interface on the policy is correct
Is this 10.13.0/24 network downstream network? Yes , there are hops to an MPLS, no directly attached, no NAT used by us (asking to ISP ), and pfsense cant reach to it.
From 10.13.0.20 -> to 8.8.8.8
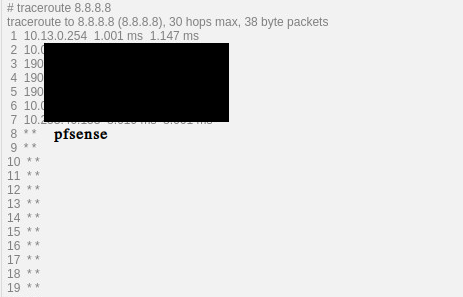
I take it the actual problem is this 10.13.0.20 is trying to ping 8.8.8.8 and you get no answer?
10.13.0.20 no reach 8.8.8.8 because its cut in pfsenseSorry me english and if i'm not clear in something
Thanks