How to set these freebsd firewall rules in pfSense?
-
Rules on freebsd:
int_if = "hn0"
ext_if = "hn1"
localnet = $int_if:network
table <t> { 10.0.0.0/8,127.0.0.0/8,192.168.0.0/16}rdr pass on $int_if proto { tcp,udp } from any to ! <t> -> 127.0.0.1 port 7892
rdr pass on lo0 proto { tcp,udp } from $ext_if to ! <t> -> 127.0.0.1 port 7892
nat on $ext_if from $localnet to any -> ($ext_if)
pass out on $ext_if route-to lo0 proto { tcp,udp } from $ext_if to ! <t>Thanks!
-
Hi,
PfSense is not purely FreeBSD, it is actually optimized for handling from the GUI, so that not only IT profesional guys can handle it.
This fact is a big part of its popularity.So you can manage firewall rules here very easily:
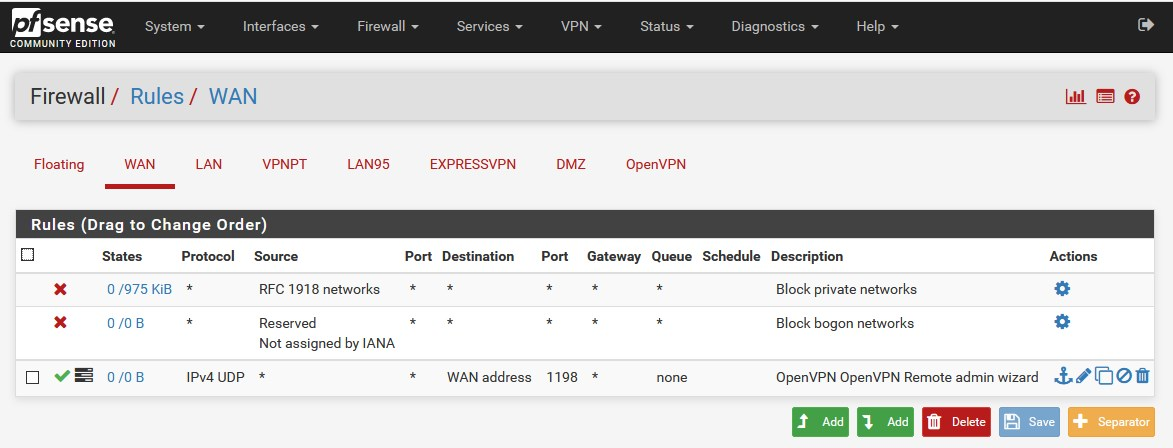
or
if you absolutely love the black screen then here: /shellhttps://docs.netgate.com/pfsense/en/latest/book/config/console-menu-basics.html
-
@jinzhanhua said in How to set these freebsd firewall rules in pfSense?:
10.0.0.0/8,127.0.0.0/8,192.168.0.0/16
create an alias with 10.0.0.0/8,127.0.0.0/8,192.168.0.0/16
Firewall / Aliases / IPcreate a rule under
Firewall / NAT / Port Forward
destination -> tick the invert match , type -> single host or alias, address/mask -> the name you chose for the alias
destination port other 7892
? redirect target 127.0.0.1 port 7892 ?
I think you need to change the redirect target, 127.0.0.1 is pfsense itself and afaik there is nothing listening on 7892
also idk what interface is hn0 / hn1, you need to adjust that too -
Question is, what is it that is running on 7892 and what should it do? Makes no sense to just single-mindedly copy the given rules without asking, what is running on localhost. As pfSense itself isn't running anything default on that port, what has the OP running that he wants to redirect to?
It that's clear, one can make the rules for it. Simply adapting rules without sense makes no sense at all to me :)
-
@kiokoman said in How to set these freebsd firewall rules in pfSense?:
@jinzhanhua said in How to set these freebsd firewall rules in pfSense?:
10.0.0.0/8,127.0.0.0/8,192.168.0.0/16
create an alias with 10.0.0.0/8,127.0.0.0/8,192.168.0.0/16
Firewall / Aliases / IPcreate a rule under
Firewall / NAT / Port Forward
destination -> tick the invert match , type -> single host or alias, address/mask -> the name you chose for the alias
destination port other 7892
? redirect target 127.0.0.1 port 7892 ?
I think you need to change the redirect target, 127.0.0.1 is pfsense itself and afaik there is nothing listening on 7892
also idk what interface is hn0 / hn1, you need to adjust that tooI setup one proxy listening on 7892.
I don't know how to set these rules in pfSense GUI:
nat on $ext_if from $localnet to any -> ($ext_if)
pass out on $ext_if route-to lo0 proto { tcp,udp } from $ext_if to ! <t> -
@JeGr said in How to set these freebsd firewall rules in pfSense?:
Question is, what is it that is running on 7892 and what should it do? Makes no sense to just single-mindedly copy the given rules without asking, what is running on localhost. As pfSense itself isn't running anything default on that port, what has the OP running that he wants to redirect to?
It that's clear, one can make the rules for it. Simply adapting rules without sense makes no sense at all to me :)
Clash run on pfSense.
https://github.com/Dreamacro/clash
It listen on 7892 port and forward packets to remote server.
Thanks! -
OK you installed an manual service/proxy on pfSense that listens on 7892.
Sooo what now? You wanna connect to it via WAN? Then just add a port forward rule with destination "WAN address" (or whatever IP on WAN you want to use) and as redirect IP use 127.0.0.1. With port 7892 of course. Anything else traffic wise would be from the proxy itself to <whereever> and would be allowed outgoing coming from "localhost".
It's nearly the same as having OpenVPN configured to listen to localhost instead of a WAN and just port forwarding it to localhost/udp1194 - that is done in MultiWAN configurations all the time. :)
That should do it:
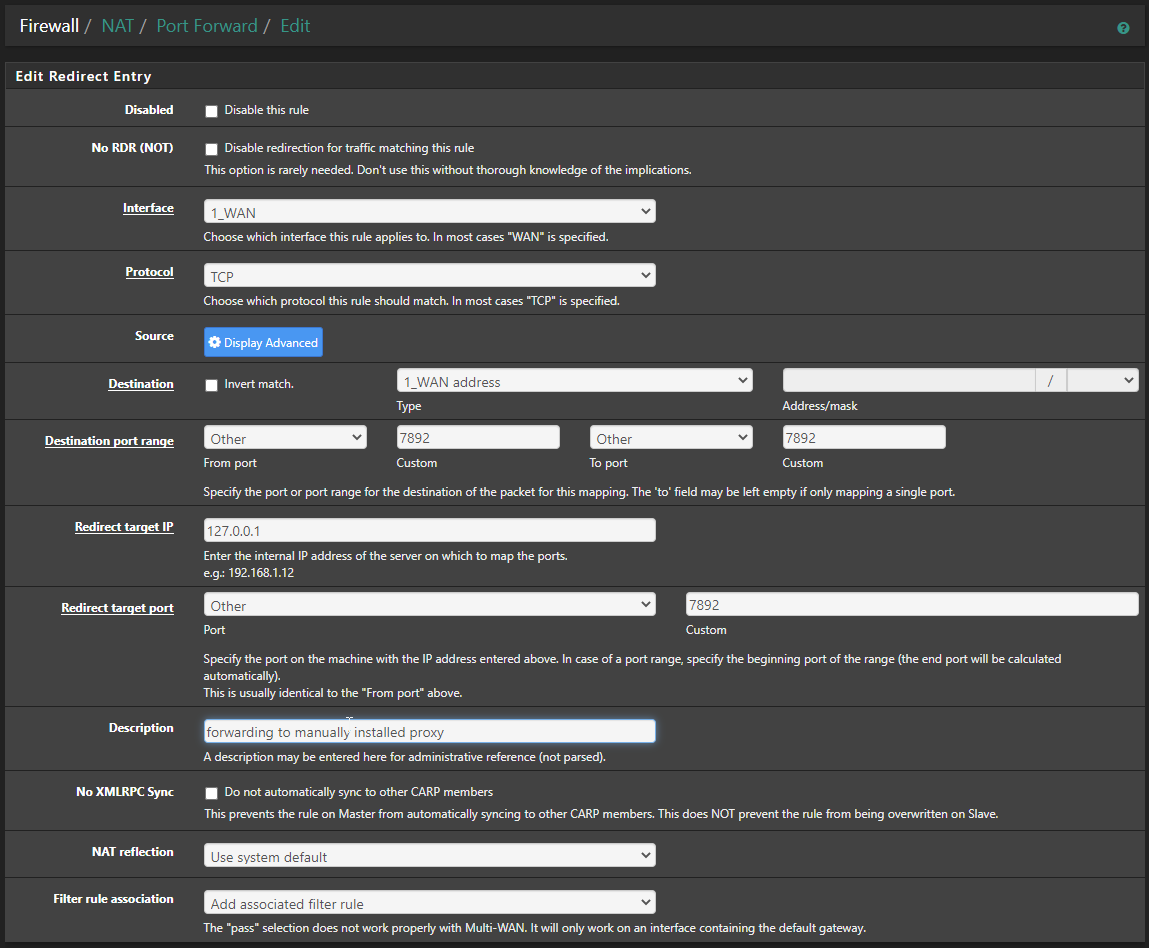
With the "Add assoc. filter rule" there should be a rule on WAN allowing the traffic, too. So you should be set.