Floating Rule - permit rule on WAN block traffic on LAN
-
Hello everyone, this is my first post.
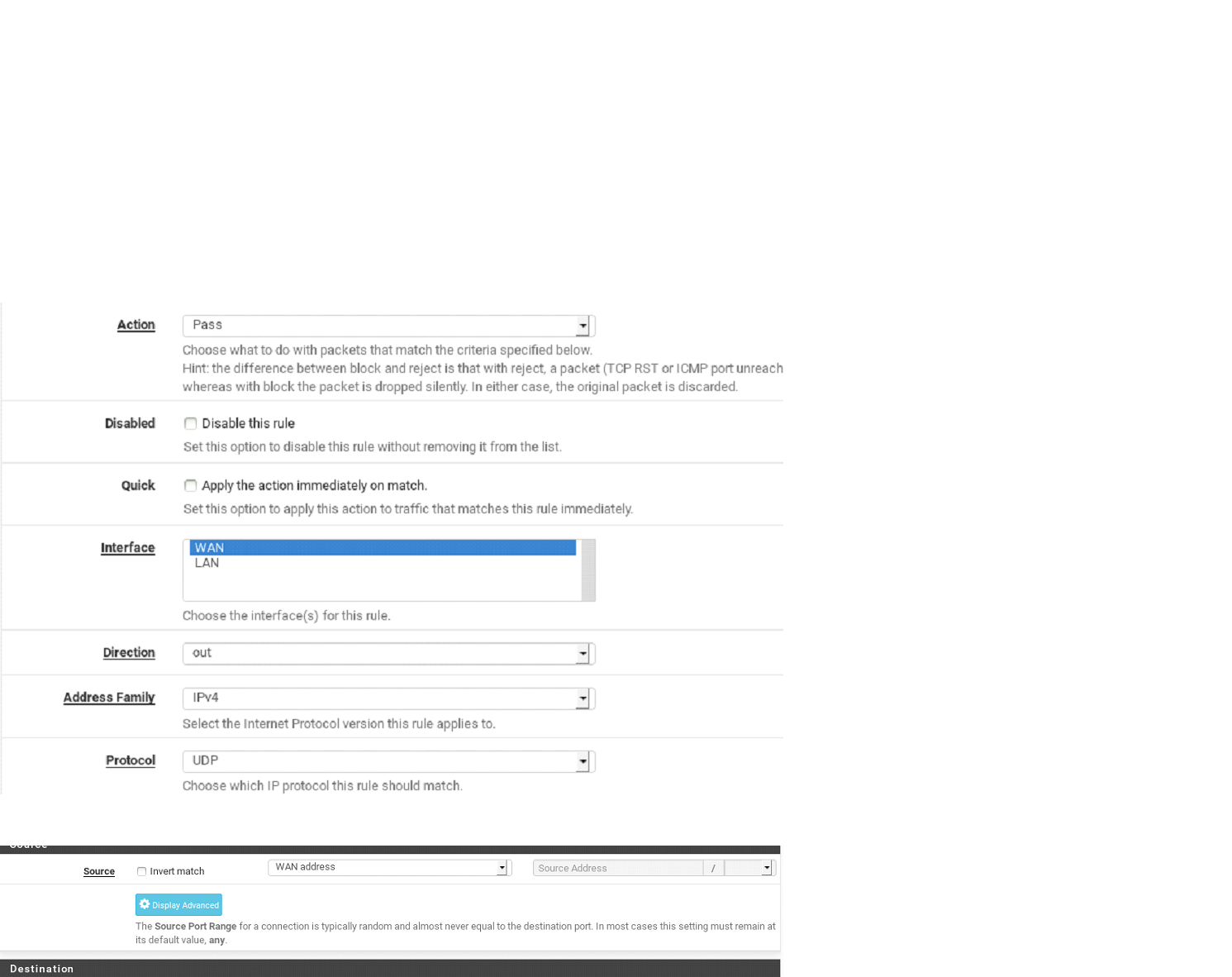
I was testing the floating rules. I have configured a rule on WAN interface, out direction, UDP protocol, port 53, action PASS. If I run nslookup from the firewall shell the result is ok, but if I do it from a client, I don't get the response. I have logged that the rule is matched but I cannot understand why the client is not receiving the response.
pfsense is configured with 2 interfaces: WAN with no defined rule and LAN with a pass all rule. There is the default NAT rule (masquerade).
If i disable rule, nslookup is ok and i can navigate on internet.
Any idea?P.s. Sorry for my english and Thanks for your help
-
@Mimmozart said in Floating Rule - permit rule on WAN block traffic on LAN:
I have configured a rule on WAN interface, out direction, UDP protocol, port 53, action PASS.
Why ?
A (floating) firewall rule has something like 48 settings and options. Sure, some combination can mess up traffic pretty good.
Please included details like screen shots etc, something that can be used to find an answer.@Mimmozart said in Floating Rule - permit rule on WAN block traffic on LAN:
If i disable rule, nslookup is ok and i can navigate on internet.
Any ideas?Yeah.
Stop testing
@Mimmozart said in Floating Rule - permit rule on WAN block traffic on LAN:
There is the default NAT rule (masquerade).
There is not default NAT rule.
@Mimmozart said in Floating Rule - permit rule on WAN block traffic on LAN:
but if I do it from a client, I don't get the response.
What DNS is used by this client ?
(The IP of) pfSEnse ?
Some other private data collector like "8.8.8.8" ?
The DNS your ISP assigned you ?Default, all these IP's are accessible by clients on a LAN, none and nothing is blocked.
Did you change any DNS related (unbound) settings ?
@Mimmozart said in Floating Rule - permit rule on WAN block traffic on LAN:
UDP protocol, port 53, action PASS
We are way past 1983, where DNS was UDP only. Add TCP also.
-
Hi, thanks for your help.
Client use 8.8.8.8 DNS.
Pfsense has two ip addresses:
LAN 172.16.20.1/24
WAN 10.10.10.11 /24 - GW 10.10.10.1client --- > pfsense
172.16.20.100/24 WAN 10.10.10.11 - GW 10.10.10.1
GW 172.16.20.1 LAN 172.16.20.1
DNS 8.8.8.8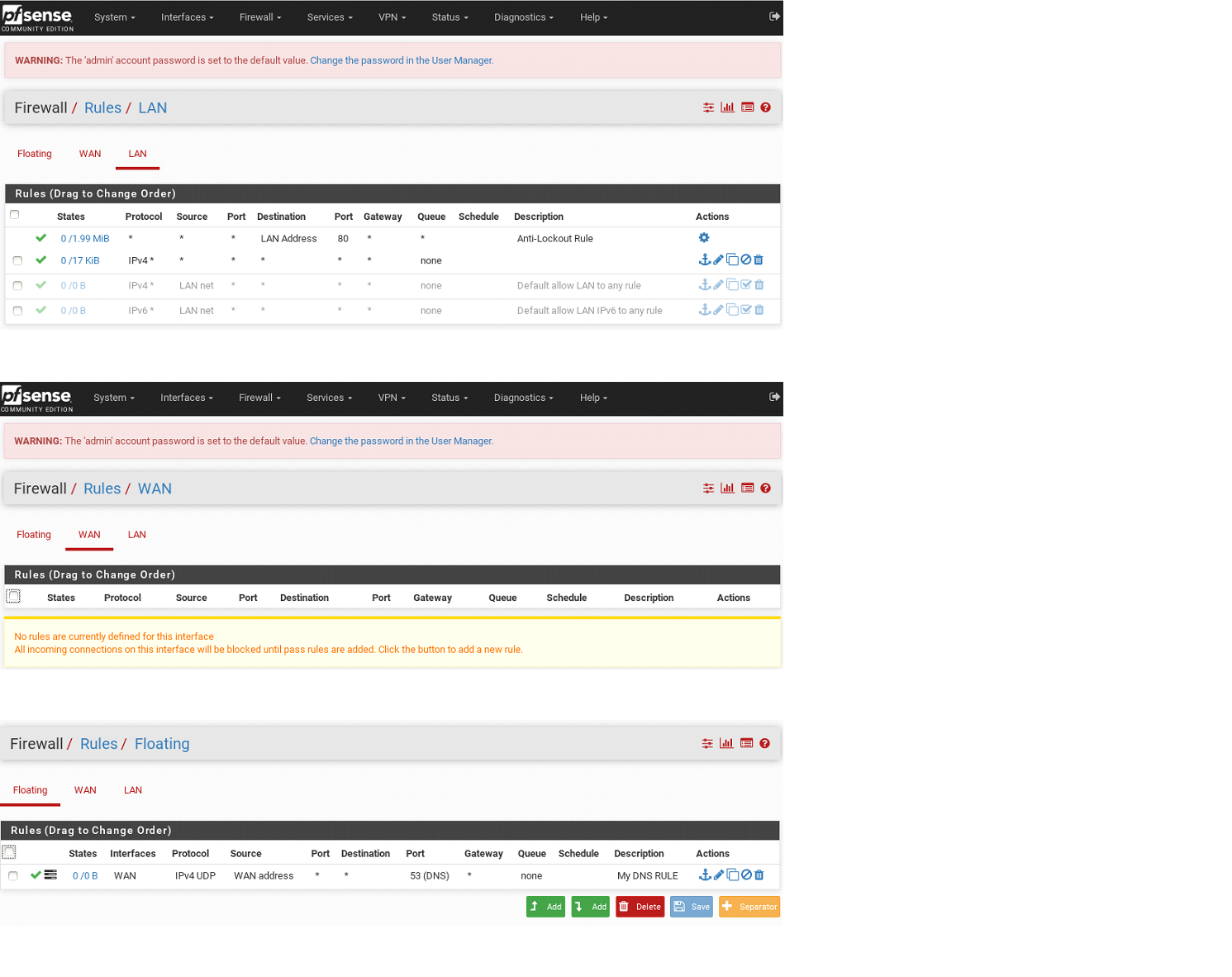
-
-
The default behaviour of a firewall is : block everything.
LAN rules are fine.
WAN rules (none) is ok.A client device on LAN can have 8.8.8.8 as a DNS, it should be is reachable as any other IP on the Internet. If not, your issue is up stream (above pfSense).
You're floating rule shows 0/0 which means : it never applies / matches. Understandable, as the source is "WAN Address" which means a device from the WAN network would use the WAN address of pfSense to do DNS lookup (?). That's totally .... not common at all.
Just delete this floating rule as it has no sense at all.
Or start explaining why you think you need this rule. -
Hi,
I configured this rule only to test floating rules. If I understand, this rule should allow outgoing requests from the WAN ip to any UDP port 53 destination. What confuses me is that enabling this rule, the access DNS from the client does not work.
Thanks