Firewall rules ignored when GW-monitoring is off
-
I have tested this on 2 separate pfS installations and either I'm doing something fundamentally wrong, or there is a bug.
I use FW rules with specified GW for routing traffic over VPN. Recently, I setup a VPN where I can't get GW-monitoring working because the far end does not allow any ICMP. I thought I would just disable GW-mon and therefor it would be "Always Online". However, now the FW rules are just ignored. There are 0 evaluations even though it is high up on the order. My PC still hits the default at the bottom. I have tried rules with all * and still no dice.
I do have the "Skip rules when gateway is down" option selected in System/Advanced/Misc because I need this type of behavior.
Any ideas on how to get this working? Is it possible to monitor a GW with something other than icmp/Ping like on Fortigate?
-
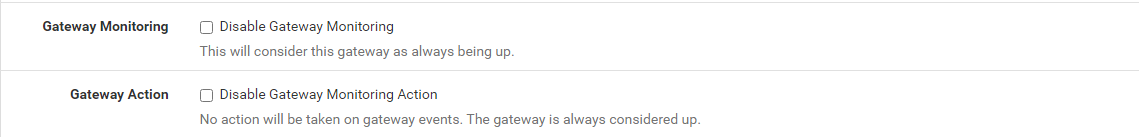
You have the top option check and not the bottom one? If so, try it the other way around and see if that works. Monitoring graphs I suspect will still show no response, but it will be ignored. Maybe a workaround of sorts.
-
I have tried selecting both options and individually. I even tried setting the monitor IP to 127.0.0.1 to try to fool it. In each case, I see 0 for all stats on the FW rule. (eval/packets/bytes)
On GWs that I have monitoring working, I have no issues with rules and they behave as expected.
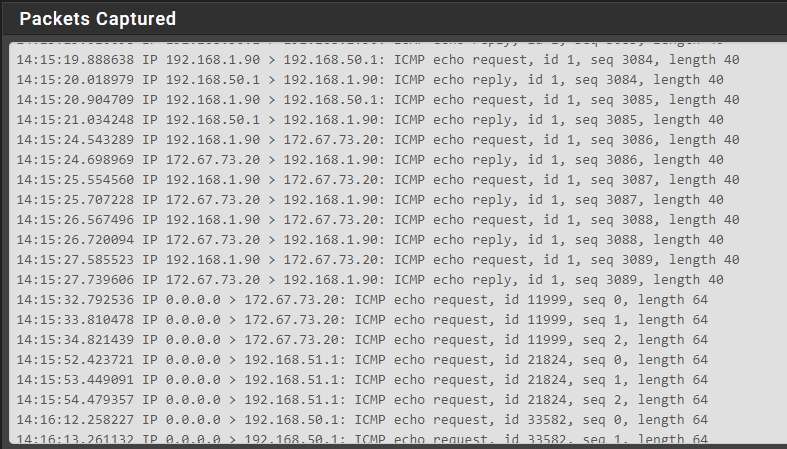
On a side note, I have one specific VTI where I control the other side's Edgerouter and therefor allowed all traffic. From my PC, I can ping and access the router and internet across the tunnel. However, when pfS pings, it uses source 0.0.0.0 IP and fails the ping. Hence monitoring isn't working either. But, fixing this only fixes one of my tunnels at home since I'm not allowed to ICMP to the vendor at work.
Thanks for the help.
-
@jimp Can you weigh in on this? I saw your reply to me on the other post. I agree that the P2 negotiation is expected behavior and not related to the OP in the other thread.
In my case, I think it is relevant because from my understanding, pfS uses the Local subnet from P2 as it's VTI address. Hence it uses 0.0.0.0 as the source IP for pinging across the VTI.
If I cannot setup NAT and I cannot manually set the VTI address, how am I supposed to get pfS to use an IP like 192.168.1.254 (pfS LAN IP) or 192.168.51.1 (pfS VPN network) for ping?
Is my claim that without successful GW-Mon, FW rules with specified GW don't work accurate?
Thanks!
-
0.0.0.0/0as a P2 has zero to do with anything on the interfaces or traffic sources. It's only a Child SA negotiated with an IPsec peer, which is expected with most third-party devices using routed IPsec. It's a complete red herring for whatever issue you're chasing. -
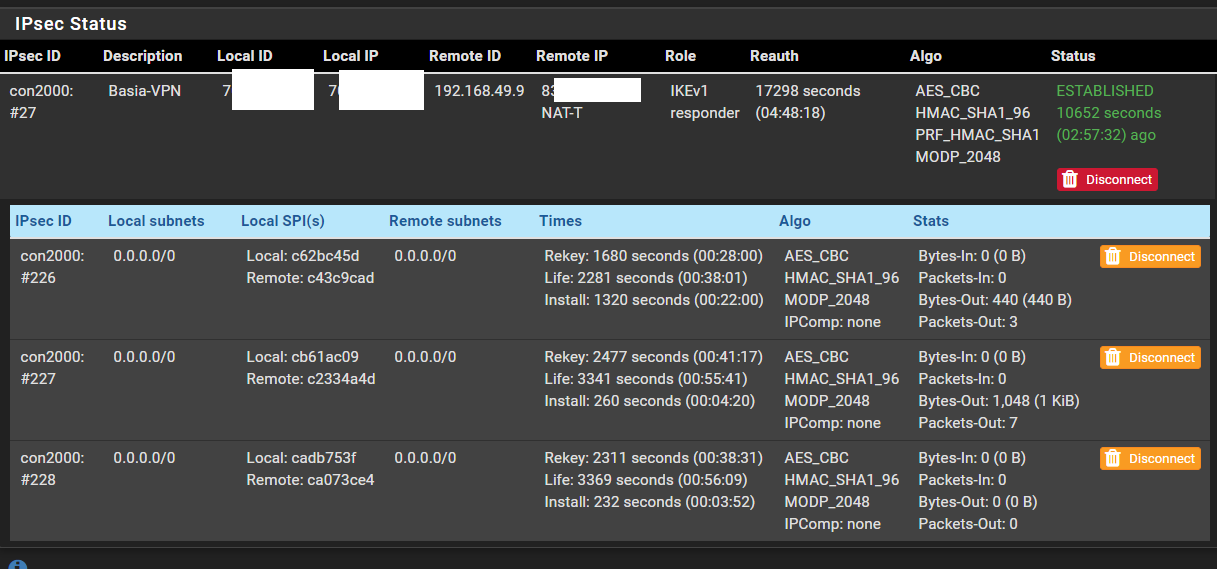
Ok, so how does pfS choose the IP from which it will ping across the VPN? I setup the connection using the standard VTI guide.
My issues are pretty clear:
- pfS uses 0.0.0.0 as source IP and Ping fails
- Ping failing means GW-mon doesn't work which means I can't use FW rules specifying that GW.
-
It selects an address based on the available interface addresses and the routing table. It uses the routing table to determine the address "closest" to the target and then selects an address on that interface which shares a subnet with the gateway through which the address will be sent.
That goes for stateless protocols like UDP and ICMP when initiating or replying, and for TCP when initiating. When responding to TCP it always responds using the address to which the initiator connected.
We have seen systems use 0.0.0.0 before on very rare occasions (maybe 3-4 ever) but I don't think we have ever nailed down why. It isn't from the VTI P2, though, because that is not an interface address, it's just a coincidence.
-
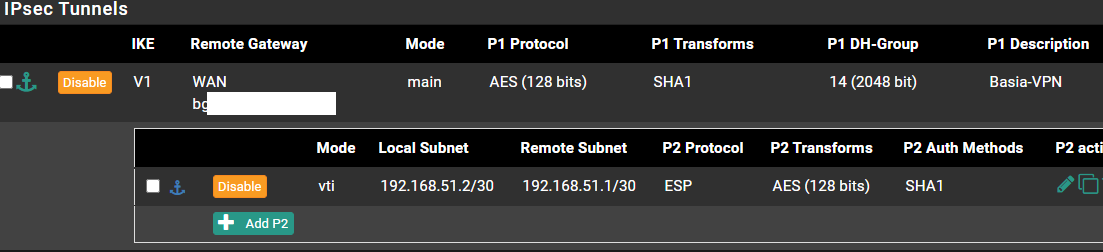
That makes sense that it would use the interface address. But, pfS doesn't allow setting the interface address like on the EdgeRouter bind command. pfS also prevents me from setting a Gateway IP address under Gateway settings.
I would expect the VTI interface address to be 192.168.51.2/30. It would probably work if pfS used ANY real IP.
I have run out of ideas of what I could have possibly done wrong. The ER was factory reset and its only purpose is the VPN.
-
FIXED. The issue was with the remote subnet. I set it to address instead of /30 network after stumbling on your Routed-IPsec slides from 2018 hangout.
With GW monitoring working, my FW rules with specified GW instantly started working. Can you confirm that these rules get ignored even when GW-mon is manually disabled?
Thanks.