VPN Tunnel between remote site
-
I have an OpenVPN setup between our main office and a remote location. Occasionally, I have to go into the main server's OpenVPN server and "save" the settings or go through the status, and restart. This occurs at random times, and has been happening about once a week where something gets "lost". I don't change any of the settings, but simply open the dialog, and "save". Not sure if it's a memory issue, or where to start looking.

Thanks in advance.
-
Ok, I have some more information on this. We have a backup internet, where our internet provider has a "cellular" backup that if our internet goes down, it switches to "cellular". Well, our static IP doesn't work on the backup, so I have a routing setup so that if the main internet goes down, it begins to route traffic through the backup (with a dynamic IP). It appears that after all is back (and so far these outages are barely 15 min in time at night), when everything goes back to normal operation mode, the VPN doesn't re-establish connection properly and has the "outage" until I hit the "save" button on the VPN page.
Not sure where to go from here, I could be way off base here, but it appears to fit the facts right now. Let me know what I can provide to assist. -
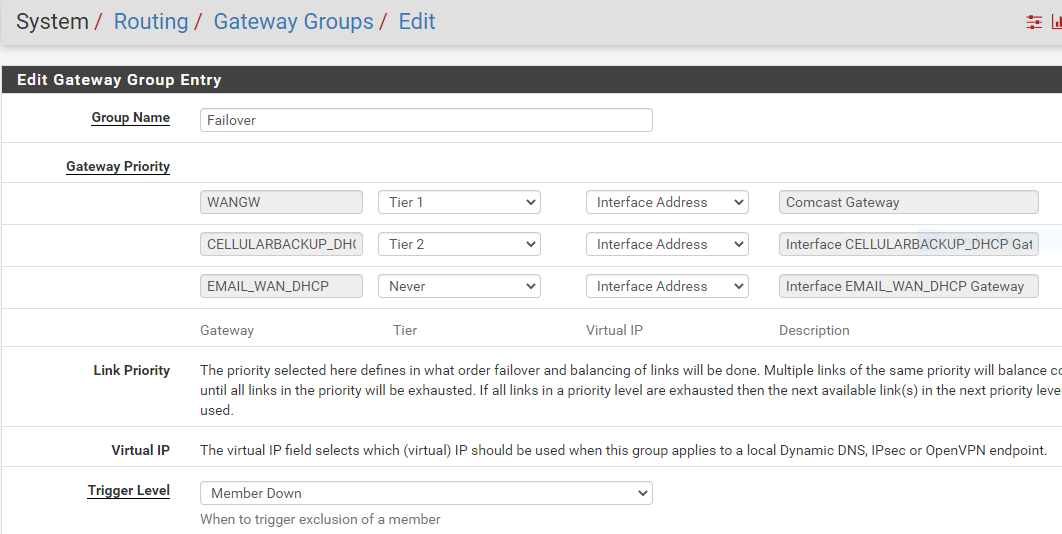
-
Well, this happened again, I received a "notification" saying the Main/Cellular connection was switched at 3AM. Here is the log from the VPN is that will help out
Oct 22 10:45:38 openvpn 38906 Initialization Sequence Completed
Oct 22 10:45:38 openvpn 38906 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Oct 22 10:45:37 openvpn 38906 Peer Connection Initiated with [AF_INET]131.93.XXX.XXX:51011
Oct 22 10:45:37 openvpn 38906 UDPv4 link remote: [AF_UNSPEC]
Oct 22 10:45:37 openvpn 38906 UDPv4 link local (bound): [AF_INET]75.146.XXX.XXX:1195
Oct 22 10:45:37 openvpn 38906 /usr/local/sbin/ovpn-linkup ovpns2 1500 1573 192.168.70.1 192.168.70.2 init
Oct 22 10:45:37 openvpn 38906 /sbin/ifconfig ovpns2 192.168.70.1 192.168.70.2 mtu 1500 netmask 255.255.255.255 up
Oct 22 10:45:37 openvpn 38906 TUN/TAP device /dev/tun2 opened
Oct 22 10:45:37 openvpn 38906 TUN/TAP device ovpns2 exists previously, keep at program end
Oct 22 10:45:37 openvpn 38906 Initializing OpenSSL support for engine 'cryptodev'
Oct 22 10:45:37 openvpn 38906 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Oct 22 10:45:37 openvpn 38732 library versions: OpenSSL 1.0.2u-freebsd 20 Dec 2019, LZO 2.10
Oct 22 10:45:37 openvpn 38732 OpenVPN 2.4.9 amd64-portbld-freebsd11.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on May 4 2020
Oct 22 10:45:37 openvpn 38732 disabling NCP mode (--ncp-disable) because not in P2MP client or server mode
Oct 22 10:45:37 openvpn 50465 SIGTERM[hard,] received, process exiting
Oct 22 10:45:37 openvpn 50465 /usr/local/sbin/ovpn-linkdown ovpns2 1500 1573 192.168.70.1 192.168.70.2 init
Oct 22 10:45:37 openvpn 50465 event_wait : Interrupted system call (code=4)
Oct 22 10:45:19 openvpn 50465 Initialization Sequence Completed
Oct 22 10:45:19 openvpn 50465 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Oct 22 10:45:19 openvpn 50465 Peer Connection Initiated with [AF_INET]131.93.XXX.XXX:51011
Oct 22 10:45:17 openvpn 50465 UDPv4 link remote: [AF_UNSPEC]
Oct 22 10:45:17 openvpn 50465 UDPv4 link local (bound): [AF_INET]75.146.XXX.XXX:1195:1195
Oct 22 10:45:17 openvpn 50465 /usr/local/sbin/ovpn-linkup ovpns2 1500 1573 192.168.70.1 192.168.70.2 init
Oct 22 10:45:17 openvpn 50465 /sbin/ifconfig ovpns2 192.168.70.1 192.168.70.2 mtu 1500 netmask 255.255.255.255 up
Oct 22 10:45:17 openvpn 50465 TUN/TAP device /dev/tun2 opened
Oct 22 10:45:17 openvpn 50465 TUN/TAP device ovpns2 exists previously, keep at program end
Oct 22 10:45:17 openvpn 50465 Initializing OpenSSL support for engine 'cryptodev'
Oct 22 10:45:17 openvpn 50465 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Oct 22 10:45:17 openvpn 50457 library versions: OpenSSL 1.0.2u-freebsd 20 Dec 2019, LZO 2.10
Oct 22 10:45:17 openvpn 50457 OpenVPN 2.4.9 amd64-portbld-freebsd11.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on May 4 2020
Oct 22 10:45:17 openvpn 50457 disabling NCP mode (--ncp-disable) because not in P2MP client or server mode
Oct 22 10:45:17 openvpn 85577 SIGTERM[hard,] received, process exiting
Oct 22 10:45:17 openvpn 85577 /usr/local/sbin/ovpn-linkdown ovpns2 1500 1573 192.168.70.1 192.168.70.2 init
Oct 22 10:45:17 openvpn 85577 ERROR: FreeBSD route delete command failed: external program exited with error status: 1
Oct 22 10:45:17 openvpn 85577 event_wait : Interrupted system call (code=4)
Oct 22 05:29:13 openvpn 68112 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]74.120.XXX.XXX:36147
Oct 22 05:27:53 openvpn 68112 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.XXX.XXX:41882
Oct 22 03:06:43 openvpn 85577 Initialization Sequence Completed
Oct 22 03:06:43 openvpn 85577 Peer Connection Initiated with [AF_INET]131.93.XXX.XXX:51011
Oct 22 03:05:27 openvpn 85577 UDPv4 link remote: [AF_UNSPEC]
Oct 22 03:05:27 openvpn 85577 UDPv4 link local (bound): [AF_INET]75.146.XXX.XXX:1195
Oct 22 03:05:27 openvpn 85577 Preserving previous TUN/TAP instance: ovpns2
Oct 22 03:05:27 openvpn 85577 Re-using pre-shared static key
Oct 22 03:05:27 openvpn 85577 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Oct 22 03:05:22 openvpn 85577 SIGUSR1[soft,ping-restart] received, process restarting
Oct 22 03:05:22 openvpn 85577 Inactivity timeout (--ping-restart), restarting -
@KruglerD said in VPN Tunnel between remote site:
Oct 22 10:45:37 openvpn 38906 Peer Connection Initiated with [AF_INET]131.93.XXX.XXX:51011
Oct 22 10:45:37 openvpn 38906 UDPv4 link remote: [AF_UNSPEC]
Oct 22 10:45:37 openvpn 38906 UDPv4 link local (bound): [AF_INET]75.146.XXX.XXX:1195Oct 22 10:45:19 openvpn 50465 Initialization Sequence Completed
Oct 22 10:45:19 openvpn 50465 Peer Connection Initiated with [AF_INET]131.93.XXX.XXX:51011
Oct 22 10:45:17 openvpn 50465 UDPv4 link remote: [AF_UNSPEC]
Oct 22 10:45:17 openvpn 50465 UDPv4 link local (bound): [AF_INET]75.146.XXX.XXX:1195:1195Oct 22 03:06:43 openvpn 85577 Initialization Sequence Completed
Oct 22 03:06:43 openvpn 85577 Peer Connection Initiated with [AF_INET]131.93.XXX.XXX:51011
Oct 22 03:05:27 openvpn 85577 UDPv4 link remote: [AF_UNSPEC]
Oct 22 03:05:27 openvpn 85577 UDPv4 link local (bound): [AF_INET]75.146.XXX.XXX:1195We can only see here 3 successful connection attempts obviously to the same IP, which may be your main WAN, I guess.
So that cannot give any hint at all.Don't see a real problem here.
Is the client configured to switch to the backup WAN if the main isn't reachable (via DynDNS) or is that not desired? -
@viragomann yeah, and this only happens when the Comcast connection goes down. The Cellular backup kicks in (I get a notification on the Dynamic IP, but don't have a dynamic domain IP setup for this).
so the firewall sends email's me this email
3:06:36 93080MONITOR: WANGW is available now, adding to routing group Failover 8.8.8.8|75.146.XXX.XXX|WANGW|28.803ms|12.393ms|0.0%|noneWhen this happens I get the call in the morning that they cannot connect to the server if I haven't logged in remotely to fix it. Trying to figure out how to fix this other than "save" my setting. Not sure if I have to figure out how to reboot after an outage, or if I can just fix this. If there is another log that someone needs, I'll be happy to post. But it seems like once the internet drops, PF either isn't resetting something or something else is going on.
-
@KruglerD
Possibly it helps to kill the states on gateway failure.This can be done automatically by checking System > Advanced > Miscellaneous > State Killing on Gateway Failure.
Give it a try. -
This setting did not effect the issue. Had our system have intermediate internet issues, and the VPN was down till I "Saved" my settings on the main VPN server.
Any other suggestions?
-
@KruglerD
Still not clear if the client is configured to connect to the backup WAN. If it is, how is this done on client and server?@KruglerD said in VPN Tunnel between remote site:
I get a notification on the Dynamic IP, but don't have a dynamic domain IP setup for this)
What does this mean???
-
@viragomann the backup wan is not configured to connect to the VPN. the Backup WAN only works to allow users to browse the internet during the downtime. Once the internet is back, I guess I'm expecting the VPN's to re-negotiate and reconnect. Right now it appears I have to force the reconnection.
-
@KruglerD
I see. Since there is no hint in the log, it's hard to say, what could be the reason for this behavior.
Moreover, the log shows two connection attempts from other hosts which are probably between the WAN outage and the server restart:Oct 22 05:29:13 openvpn 68112 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]74.120.XXX.XXX:36147 Oct 22 05:27:53 openvpn 68112 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.XXX.XXX:41882But nothing from the remote office. That let me assume, that the server is working properly and the real reason for the problem is at the client side, which would make more sense to me.
What if you try to restart the client service in case of failure? Don't know if you have access to it.Possibly on the server it helps to set the OpenVPN server listen on localhost instead of the WAN interface and set a NAT rule to forward the OpenVPN packets to localhost.
Also the Service_Watchdog may help. As far as I know it is capable to monitor the VPN connection and restart the service if it's not up. You can use it on server and client.
-
I'm coming back to this as this was not resolved and would like this to be taken care of.
I thought instead of "saving" the vpn configuration on the main server I'd try rebooting the main firewall instead to see if that would rectify the problem. It didn't. It appears that when the main internet drops and the firewall switches to the "backup", there is a VPN setting that is getting corrupted (either gets hung up on the switch and doesn't switch back, or some other setting that gets flipped, but gets reset when I click save).
I have attached the server VPN log Server VPN.txt and client VPN log Client VPN.txt from 6pm to 8am (outage was 7:30pm to 8:30pm)
I am also attaching the main server log Server Main Log.txt
I noticed this line
OpenVPN: One or more OpenVPN tunnel endpoints may have changed its IP. Reloading endpoints that may use WANGW
Is this not reloading correctly?
Thanks in advance...