DHCP DNS registration on FreeIPA
-
Re: Forward DNS queries to Active directory DNS Server
Hi Ladies and Gents here,
I would be very thankful if someone could help me.
A: I am having a Pfsense running with the following services:
- DHCP for 7 vlans.
- DNS resolver, managing my own owned domain (godadday)
- It’s my gateway to the internet
B: Two CentoS FreeIPA IAM Servers to manage all internal DNS (I’m still in the process of moving all clients DNS to the FreeIPA).
- I’m using the Pfsense as a forwarder to the Internet (could use the ISP directly to reduce latency, but that’s another story).
- I have tested and most is working pretty well till now, except few things (no’ 3)
- The most difficult part is:
I’m interested to get the Pfsense DHCP Server to register DNS A and AAA records for the clients directly (and automatically) on the FreeIPA DNS server, I tried to get this work but no luck.
The only thing that works is getting the DNS settings assignment by DHCP, but that’s where it ends.
So the bottom line is getting the DHCP from Pfsense DNS resolver to register DNS records to the FreeIPA domain controller instead of the itself (only for internal leases).
Many Thanks
 on advance.
on advance. -
i don't know FreeIPA but if it's using bind you just need to:
under the dhcp server / Dynamic DNS
Enable registration of DHCP client names in DNS -> tick
Enter the dynamic DNS domain which will be used to register client names in the DNS server. -> example.local
Primary domain name server IP address for the dynamic domain name. -> ip of FreeIPA/bind
configure the Dynamic DNS domain key name which will be used to register client names in the DNS server. -> rndc-key
select Key algorithm HMAC-SHA 256 it's the current bind9 default
insert the DNS Domain key secret -> you can generate it with rndc-confgen
and press apply
if you have bind correctly configured it should workfor example on my ubuntu server i have this on named.conf
zone "trmultiservice.lab" { type master; file "/etc/bind/internal/pri.trmultiservice.lab"; allow-update { key rndc-key; }; }; zone "1.168.192.IN-ADDR.ARPA" IN { type master; file "/etc/bind/internal/reverse-192.168.1"; allow-update { key rndc-key; }; };and they are updated by pfsense dhcp server
-
Many Thanks @kiokoman,
I will try that tomorrow, not that I’m doubting the information, but isn’t DDNS is designed for updating Public DNS?
Thanks again.
-
@Phonix66
Ok, have been reading this here:
https://docs.netgate.com/pfsense/en/latest/services/dhcp/ipv4.htmlmakes sense!
Will apply ASAP.Thx
-
Thanks, @kiokoman
I have completed all as advised.
I cannot tell if it's really working since I don't see a difference to the state I had before.
What I can surly see is the following, on the FreeIPA I see that no DNS records are being automatically created on the server (nor A or reverse).
That makes me believe that something isn't being registered as suppose to.KR,
-
you need to check named logs, you should see something like
02-Oct-2020 13:02:52.314 client @0x7ff3d81c3850 172.16.0.254#25129/key rndc-key: view trusted: updating zone 'trmultiservice.lab/IN': deleting rrset at 'PC-PRINK.trmultiservice.lab' TXT 02-Oct-2020 13:02:52.314 client @0x7ff3d81c3850 172.16.0.254#25129/key rndc-key: view trusted: updating zone 'trmultiservice.lab/IN': adding an RR at 'PC-PRINK.trmultiservice.lab' TXT "31329b13b011cd42487cdf165ec99d3832" 02-Oct-2020 13:02:52.314 client @0x7ff3d81c3850 172.16.0.254#25129/key rndc-key: view trusted: updating zone 'trmultiservice.lab/IN': deleting rrset at 'PC-PRINK.trmultiservice.lab' A 02-Oct-2020 13:02:52.314 client @0x7ff3d81c3850 172.16.0.254#25129/key rndc-key: view trusted: updating zone 'trmultiservice.lab/IN': adding an RR at 'PC-PRINK.trmultiservice.lab' A 192.168.1.13 02-Oct-2020 13:02:52.322 client @0x7ff3d81c3850 172.16.0.254#33543/key rndc-key: view trusted: updating zone '1.168.192.IN-ADDR.ARPA/IN': deleting rrset at '13.1.168.192.in-addr.arpa' PTR 02-Oct-2020 13:02:52.322 client @0x7ff3d81c3850 172.16.0.254#33543/key rndc-key: view trusted: updating zone '1.168.192.IN-ADDR.ARPA/IN': adding an RR at '13.1.168.192.in-addr.arpa' PTR PC-PRINK.trmultiservice.lab.where 172.16.0.254 is my pfsense.
be sure you have -> include "/path/to/rndc.key"; inside your named.conf,
check acl to be sure your pfsense is trusted by bind9
you need to manually create the zone files, they will not be automagically generated by bind
if you have set everything on pfsense as I said earlier you need to configure bind to receive it. maybe ask FreeIPA forum about that -
@kiokoman Thanks for the quick reply.

First I am unable to add the "/path/to/rndc.key", here Pfsense will not accept anything else then"rndc-key", adding the "/path/to/rndc.key", throws this error:
The following input errors were detected:
The domain key name may only contain the characters a-z, A-Z, 0-9, '-' and '_'
My file on the BIND server is at "/etc/rndc.key".Also looking into the logs on the BIND server, and comparing to your logs, I get:
02-Oct-2020 13:21:16.571 client @0x7f784c0ce650 192.168.6.254#44662: request has invalid signature: TSIG rndc-key: tsig verify failure (BADKEY)
02-Oct-2020 13:25:17.450 client @0x7f78384cdef0 192.168.6.254#43356: request has invalid signature: TSIG rndc-key: tsig verify failure (BADKEY)
02-Oct-2020 13:25:21.403 client @0x7f7838295ef0 192.168.6.254#38503: request has invalid signature: TSIG rndc-key: tsig verify failure (BADKEY)
02-Oct-2020 13:28:35.301 client @0x7f783c293a00 192.168.6.254#33923: request has invalid signature: TSIG rndc-key: tsig verify failure (BADKEY)
02-Oct-2020 14:03:33.533 client @0x7f78380a0940 192.168.6.254#59003: request has invalid signature: TSIG rndc-key: tsig verify failure (BADKEY)
02-Oct-2020 14:10:26.461 client @0x7f784c0ce650 192.168.6.254#18281: request has invalid signature: TSIG rndc-key: tsig verify failure (BADKEY)
02-Oct-2020 14:16:53.216 client @0x7f7838295ef0 192.168.6.254#59198: request has invalid signature: TSIG rndc-key: tsig verify failure (BADKEY)
02-Oct-2020 14:25:14.917 client @0x7f78383ac9d0 192.168.6.254#38966: request has invalid signature: TSIG rndc-key: tsig verify failure (BADKEY)
02-Oct-2020 14:25:21.406 client @0x7f784c0bfa80 192.168.6.254#10953: request has invalid signature: TSIG rndc-key: tsig verify failure (BADKEY)
where 192.168.0.254 is my pfsense (This Vlan interface for that zone)I was looking into FreeIPA documentation and there is no GUI option for the bind server, it's just as any CLI bind configuration.
I believe that the rdnc.key the secret key is not being interpreted correctly by the DHCP server, but I'm quite lost at the moment...Thanks,
-
include "/path/to/rndc.key"-> go inside named.conf on freeipa
tsig verify failure (BADKEY)the key inside pfsense and the one inside rndc.key are not the same
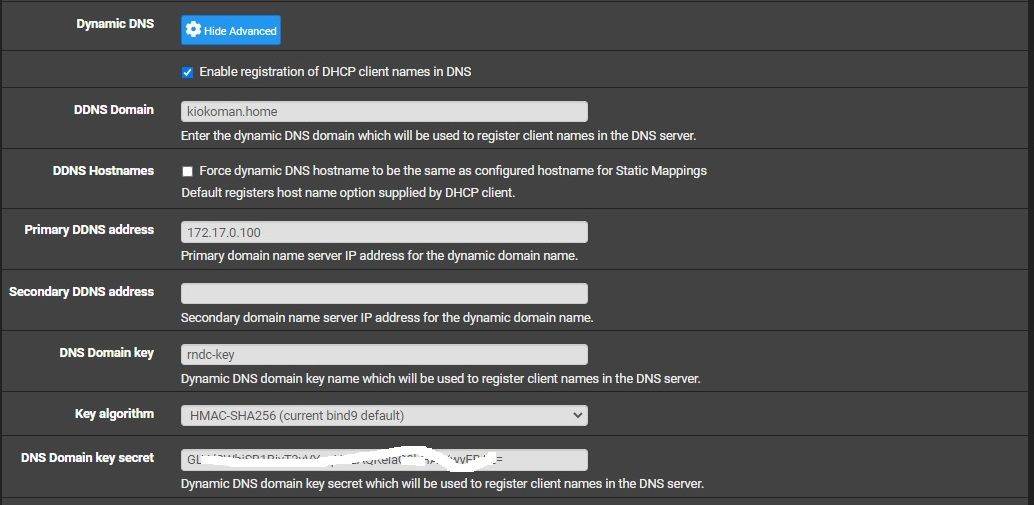
DNS Domain key secret must match what you have on freeipa inside rndc.key
-
I went into the named.conf on freeipa and added the:
include "/etc/rndc.key"unfortunately It didn't work, bind was not working after.
Otherwise I have set all the settings as you did, I have taken the key for theDNS Domain key secret from the rndc.key on the FreeIPA server.
Where should I put the?:
include "/etc/rndc.key"Here is how my /etc/named.conf looks like:
named-conf.txtUnfortunately it didn't work
-
under
include "/etc/named.rfc1912.zones"; include "/etc/named.root.key";did you forgot the
;at the end perhaps?
include "/etc/rndc.key";check the logs if it does not start, it will tell you why
-
Ok, I added all the info as you suggested.
It seems like we making progress, but now I get the following:02-Oct-2020 18:38:49.677 zone 0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.IP6.ARPA/IN: shutting down 02-Oct-2020 18:38:49.677 zone D.F.IP6.ARPA/IN: shutting down 02-Oct-2020 18:38:49.677 zone 8.E.F.IP6.ARPA/IN: shutting down 02-Oct-2020 18:38:49.677 zone 9.E.F.IP6.ARPA/IN: shutting down 02-Oct-2020 18:38:49.677 zone A.E.F.IP6.ARPA/IN: shutting down 02-Oct-2020 18:38:49.677 zone B.E.F.IP6.ARPA/IN: shutting down 02-Oct-2020 18:38:49.677 zone 8.B.D.0.1.0.0.2.IP6.ARPA/IN: shutting down 02-Oct-2020 18:38:49.677 zone EMPTY.AS112.ARPA/IN: shutting down 02-Oct-2020 18:38:49.688 managed-keys-zone: Key 20326 for zone . acceptance timer complete: key now trusted 02-Oct-2020 18:38:49.695 LDAP configuration for instance 'ipa' synchronized 02-Oct-2020 18:38:49.718 LDAP data for instance 'ipa' are being synchronized, please ignore message 'all zones loaded' 02-Oct-2020 18:38:49.808 zone 2.168.192.in-addr.arpa/IN: loaded serial 1601656729 02-Oct-2020 18:38:49.808 zone 6.168.192.in-addr.arpa/IN: loaded serial 1601656729 02-Oct-2020 18:38:49.809 zone int.example.com/IN: loaded serial 1601656729 02-Oct-2020 18:38:49.809 3 master zones from LDAP instance 'ipa' loaded (3 zones defined, 0 inactive, 0 failed to load) 02-Oct-2020 18:38:49.809 zone 2.168.192.in-addr.arpa/IN: sending notifies (serial 1601656729) 02-Oct-2020 18:38:49.809 zone 6.168.192.in-addr.arpa/IN: sending notifies (serial 1601656729) 02-Oct-2020 18:38:49.809 zone int.example.com/IN: sending notifies (serial 1601656729) 02-Oct-2020 18:38:54.812 zone 2.168.192.in-addr.arpa/IN: sending notifies (serial 1601656729) 02-Oct-2020 18:38:54.812 zone 6.168.192.in-addr.arpa/IN: sending notifies (serial 1601656729) 02-Oct-2020 18:38:54.812 zone int.example.com/IN: sending notifies (serial 1601656729) 02-Oct-2020 16:41:15.900 client @0x7f7a300ce650 192.168.6.254#37316/key rndc-key: updating zone 'int.example.com/IN': update failed: rejected by secure update (REFUSED)It seems that my reverse zones are replicating from the server without manually adding them (I added them on the GUI).
But I don't know why I get refused, I used the right secret from the rdnc.key file:[root@ipa-dctrl1 ~]# cat /etc/rndc.key key "rndc-key" { algorithm hmac-sha256; secret "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"; };I also seen the permission on the file are ok:
[root@ipa-dctrl1 ~]# ls -l /etc/rndc.key
-rw-r-----. 1 root named 100 Sep 30 18:45 /etc/rndc.keyThanks,
-
@kiokoman said in DHCP DNS registration on FreeIPA:
allow-update { key rndc-key; };
^
it's inside your zone definition int.example.com ? -
I have set dynamic updates on the FreeIPA GUI to "dynamic updates":
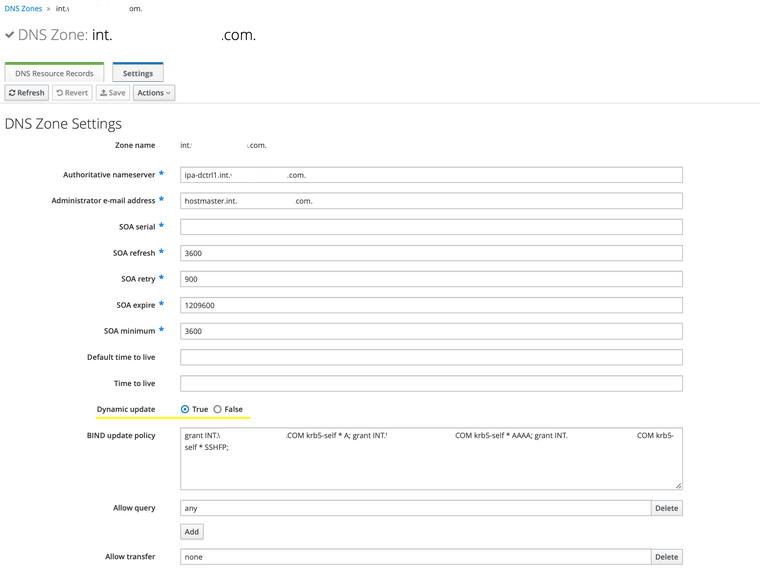 .
.So I don't know if I can change this anymore, should I put this line into the named.conf file?
looking into this info I think it's not possible anymore:
https://www.freeipa.org/page/Howto/ISC_DHCPd_and_Dynamic_DNS_updateTHX
-
that's why i generally don't like webgui for this stuff
ok ,so freeipa use Update Policies
https://bind9.readthedocs.io/en/v9_16_5/reference.html#dynamic-update-policiesyou need
grant "rndc-key" zonesub ANY;or something like that
-
@kiokoman
Should I insert it to the named.conf under include "/etc/rndc.key"; ? -
no, you can put it in the gui inside
BIND update policy
or it go insideupdate-policy { };inside named.conf
-
@kiokoman said in DHCP DNS registration on FreeIPA:
grant "rndc-key" zonesub ANY
IT WORKED! YOUR THE GREATEST!
Will add the details later on.


-
nice !

-
@kiokoman said in DHCP DNS registration on FreeIPA:
grant "rndc-key" zonesub ANY;
I just added the:
grant "rndc-key" zonesub ANY;In to the update policy in the GUI, and it works, I see that the A records are automatically updated.
In regards of the reverse records, I didn’t have the time to check, but now I believe that this can easily be resolved by repeating the procedure also for reverse records.Thanks again


-
yes, you just need to create the reverse zone
zone "1.168.192.IN-ADDR.ARPA" IN { type master; file "/etc/bind/internal/reverse-192.168.1"; allow-update { key rndc-key; }; };the same options are available under "dhcpv6 server & RA"