OpenVPN on PFSense behind NAT tunel communication problem
-
Hi,
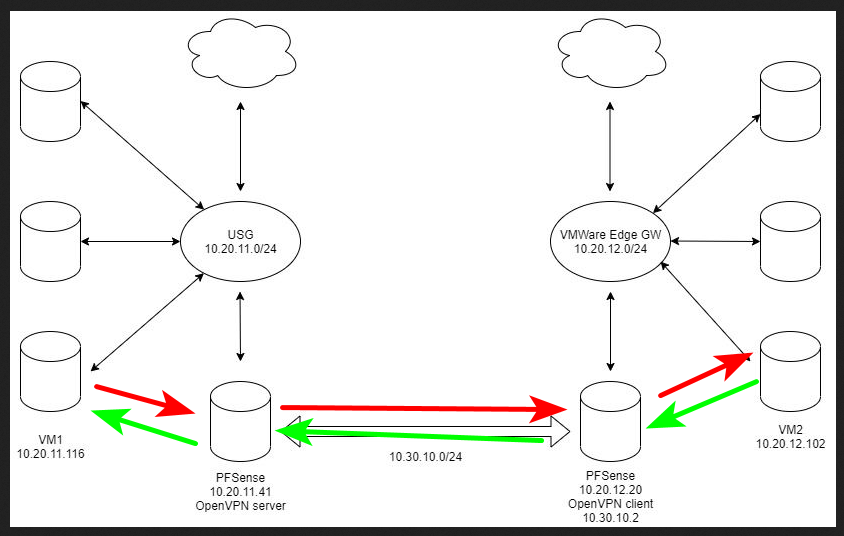
I have two networksFirst is 10.20.11.0/24, there is Unifi Security gateway.
Installed PFsense (10.20.11.41) as virtual machine, behind NAT, firewall is disabled.
On Unifi Security gateway there is static route that routes traffic to 10.20.12.0/24 over 10.20.11.41
There is OpenVPN server Peer to Peer.
Tunnel network is 10.30.10.0/24Second, 10.20.12.0/24, there is VMWare Edge Gateway, some virtual machines...
Installed PFsense (10.20.12.20) as virtual machine, behind NAT, firewall is disabled.
On Edge Gateway, static route that routes traffic to 10.20.11.0/24 over 10.20.12.20 (PFSense)
There is OpenVPN client configured and active.I need machines in both networks to communicate to each other.
I can ping every device in 10.20.11.0/24 from side with Edge Gateway.
But from USG side, I can ping only Edge Gateway and PFSense, but can't ping other devices.Can you help me please?
-
Simple drawing showing your network makes it 1000x easier to assess..
Without drawing this out, It seems you prob have asymmetrical issues. This 10.20.11 is your transit network between your usg and pfsense. And you have hosts on this network? Without host routing, and or natting, and port forwarding you will have asymmetrical routing problems.
behind NAT, firewall is disabled.
How exactly did you accomplish that on pfsense?
Even with firewall rules that allow all traffic, you can still run into out of state traffic being blocked.
If you want to remove asymmetrical issues and allow networks to talk to each other without problems. Routers, be it they firewall or not need to be connected via transit networks (a network with no hosts/clients on it)..
Talking to and from clients that are on a transit network (network between routers) is always going to be problematic because of asymmetrical traffic flow. Unless these hosts on the transit have routes on them saying which router to talk to to get to what networks.
-
Sorry, here is my diagram.
Firewall is "disabled" by adding allow rule everything to everyhing on both PFSense.
Disable all packet filtering is unticked.In digram: VM1 can't access VM2 on other side but VM2 can access VM1.
Tracert from VM1 to VM2 ends on 10.30.10.2, which is OpenVPN client address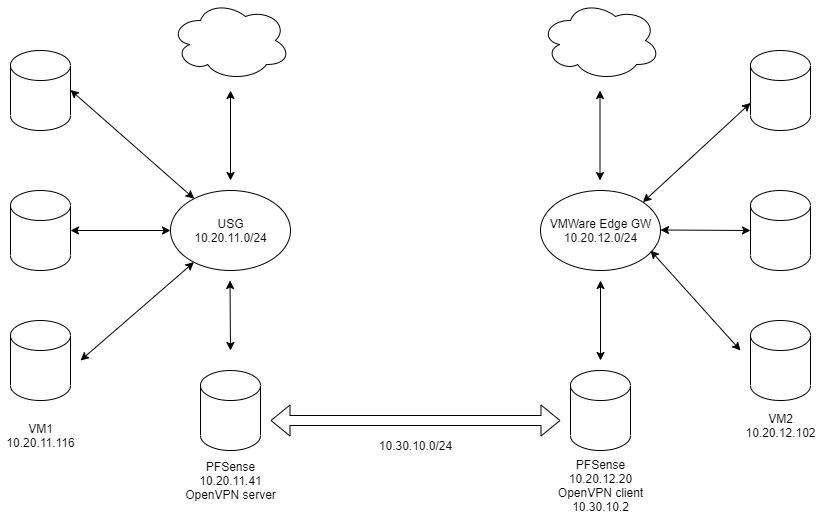
-
That is asymmetrical mess
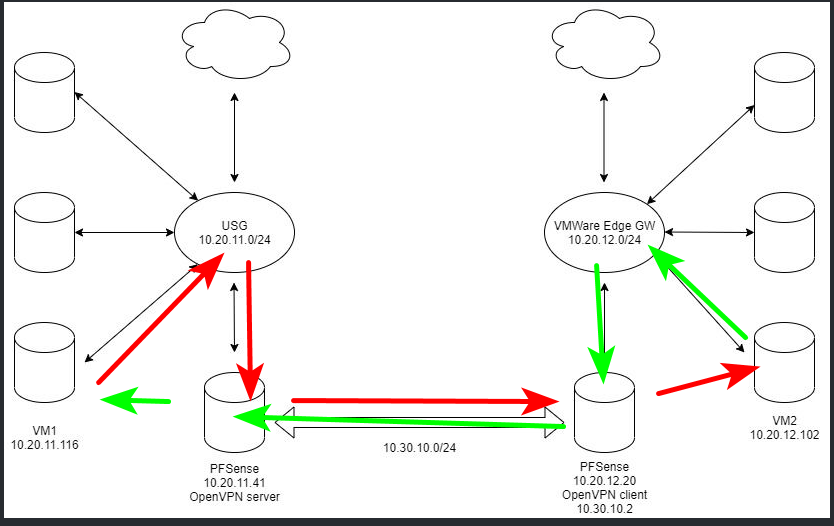
If you want to use pfsense as downstream routers from your USGs then connect them with transit networks..
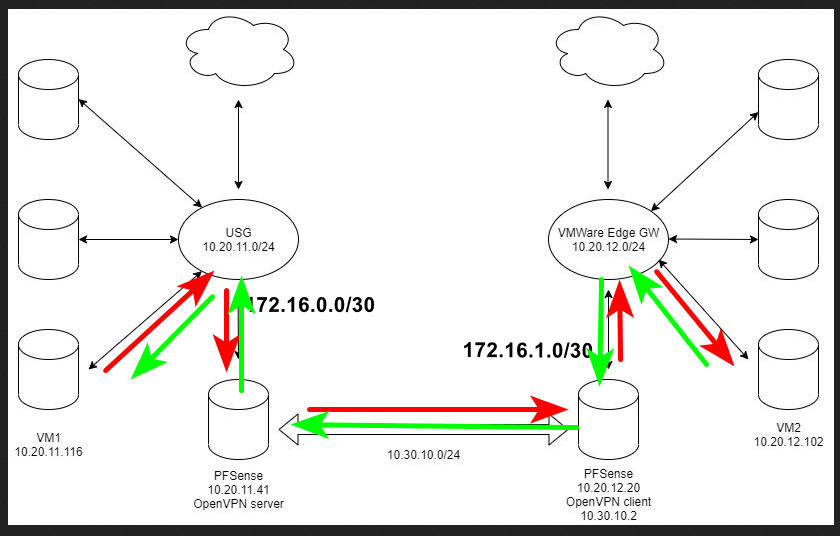
You could also just solve this with just a transit between your 2 USGs.. 1 pfsense between the 2 of them with leg connected to each USG which would be the transit network connected to each USG.
You could also use port forwarding and source natting to solve the problem on every host in your different 20.11 and 20.12 networks. Or host routing so your flow would look like this.