Dumb question, can I allow traffic from an IP range for VOIP?
-
I just have a home VOIP solution (literally just one phone on a static IP). However, I've noticed that the firewall is blocking some of the SIP and RTP traffic. This is causing inbound calls to not connect but outbound is fine.
My provider has this guide showing the IP's that need to be allowed. The main range that is being blocked is the 81.187.30.110 - 81.187.30.119 range.
Can I do this is one rule (i.e. allow 81.187.30.110 - 81.187.30.119 on ports 5000 to 5999)? Apologies, I'm not network-savvy at all.
-
Yes, you can do that in a few ways. The best way is via an IP alias.
First create an alias for the range of IP's.
Firewall > Aliases > IP
Select Host(s) as type and fill in the rest with something that makes sense to you.Then enter an IP range, using your VOIP example,
81.187.30.110:81.187.30.119Or select Network(s) type
Then enter a single network, using your VOIP example,
90.155.3.0/24Then you have a create a firewall rule using that alias (assuming the phone is on LAN interface).
Firewall > Rules > LanCreate a rule similar to the one below. In my example below, the 8x8 subnets is the alias for my VOIP providers IP's. Notice the ports are not specified, a wildcard is used and it is allowed to go to any port to those specific IP's. That should be enough.
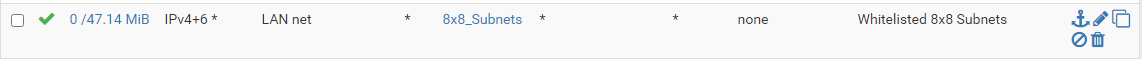
In my case though, that was enough for some phones but oddly enough other phones didn't like that. If the method above works for you, great, stick with that. If not, scrap the first method and then try allowing your specific phone IP (which is static) to go out of any port.
No alias needed for this method since it's only one IP. Create a rule on LAN similar to the one below. In your case don't use an alias and enter the single IP of your phone.
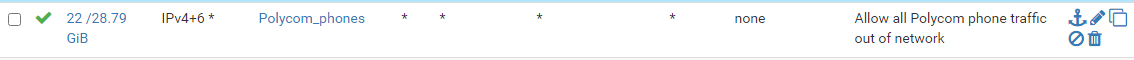
Note that if you have any block rules on LAN, you might have to put the new rules created from method one or method two above the block rule. Otherwise the block rule could be the first rule evaluated and acted on, and your new rule might not work.
-
@Raffi_ Thank you, I did not know about aliases that works well. The phone is on the LAN. It's just a simple 192.168.0.1/24 network.
However, the issue is with inbound calls and from what I can see on my firewall log there's a bunch of blocked traffic (mainly RTP) from my VOIP provider coming inbound to my WAN IP.
Shouldn't the rule be on my WAN then and not the LAN?
-
@adowson Yeah, you can try it, but you're going to need a NAT rule most likely. So, let's start there.
Go to Firewall -> NAT, and create a new Port Forward rule. Doesn't really matter if it's at the bottom, top, or middle of this list, just make a new one and program it like this:
Interface: WAN
Protocol: TCP/UDP
Source: the IP address of your VOIP provider
Source Port Range: any
Destination: WAN address
Destination Port Range: Other (and in the custom box put in your port range alias you created earlier)
Redirect Target IP: address of your phone
Redirect Target Port: (port range alias here again, as above)
Description: give it a good name
Filter Rule Association: add associated filter ruleOk, then click save, and a NEW firewall rule on your WAN interface will be created. Go double check that. You might need to reboot the pfsense box after this, but maybe not.
Hope that helps!
Jeff
-
@akuma1x I'm using the siproxd package which does have my phone registered. Doesn't that cover the NAT requirements?
-
@adowson Ooooo, don't know about that. I didn't see that you were using that package in your original post, and I don't use it anyway. Sorry about that.
-
@adowson said in Dumb question, can I allow traffic from an IP range for VOIP?:
@Raffi_ Thank you, I did not know about aliases that works well. The phone is on the LAN. It's just a simple 192.168.0.1/24 network.
However, the issue is with inbound calls and from what I can see on my firewall log there's a bunch of blocked traffic (mainly RTP) from my VOIP provider coming inbound to my WAN IP.
Shouldn't the rule be on my WAN then and not the LAN?
That might be necessary. I'm not familiar with that particular VOIP provider. For my VOIP service, I never had to do anything special in terms of creating WAN rules and I didn't need the siproxd package, but then again not all services work the same. I personally would avoid putting ANY rules on the WAN unless it is the very last resort. I would probably prefer changing my VOIP service provider rather than open ports from the WAN side.
Edit, in your case if the WAN rules are limited to your VOIP IP ranges ONLY, it may not be so bad. I still would be hesitant though. Try what I suggested if you haven't already tried it on the LAN and see where that gets you.
Edit again, I probably should have started off asking what your LAN rules look like. If you already have the default Any - Any rule, then my suggestions for the rules on the LAN don't matter since any traffic originating from your LAN would allowed out of the network.
-
Well, at the risk of tempting the gods, the issue seems to have suddenly stopped and only lasted a day. All inbound calls have been working, no IP's from my provider have been blocked by PFsense. I do not have any rules running to allow it, it's on default deny.
I agree that I would rather not meddle with my WAN firewall rules. I'll keep an eye on the issue and see what happens. It could have just been a fault or siproxd going haywire, I don't know.