I see some : openvpn 95093 TCP/UDP packet too large on write - Should i be worried ?
-
One of my OpenVPN Server daemons have begun logging the below
Oct 13 11:04:09 openvpn 95093 TCP/UDP packet too large on write to [AF_INET]112.121.x.x:44795 (tried=1572,max=1570) Oct 13 11:04:09 openvpn 95093 TCP/UDP packet too large on write to [AF_INET]112.121.x.x:44795 (tried=1572,max=1570) Oct 13 11:04:05 openvpn 95093 TCP/UDP packet too large on write to [AF_INET]112.121.x.x:44795 (tried=1572,max=1570) Oct 13 11:04:05 openvpn 95093 TCP/UDP packet too large on write to [AF_INET]112.121.x.x:44795 (tried=1572,max=1570) Oct 13 11:04:01 openvpn 95093 TCP/UDP packet too large on write to [AF_INET]112.121.x.x:44795 (tried=1572,max=1570) Oct 13 11:04:01 openvpn 95093 TCP/UDP packet too large on write to [AF_INET]112.121.x.x:44795 (tried=1572,max=1570) Oct 13 11:03:57 openvpn 95093 TCP/UDP packet too large on write to [AF_INET]112.121.x.x:44795 (tried=1572,max=1570) Oct 13 11:03:57 openvpn 95093 TCP/UDP packet too large on write to [AF_INET]112.121.x.x:44795 (tried=1572,max=1570)They come in bursts of 5..7 lines , and a bit random , 2..3 times a minute.
Is that just an info , or am i actually dropping data ?How do i trace what would be generating this (besides tcpdump/wireshark) ?
Would a MAX MTU on the OVPN interface cure it ?I see no erroors on the Client side (a pfSense 2.4.4-p3)
/Bingo -
mtu issue, packets are dropped
try withfragment 1450; mssfix 1450;custom option of openvpn
-
Thanx
Is that on/in the VPN server definitions ?
Do i set it on the Client side too , even if i don't see any issues there ?/Bingo
-
@bingo600 That's the very first box under the Advanced Configuration of the pfsense OpenVPN server settings. You've got to either copy and paste it in there, or type it by hand.
Don't know if the client has to be set too, however.
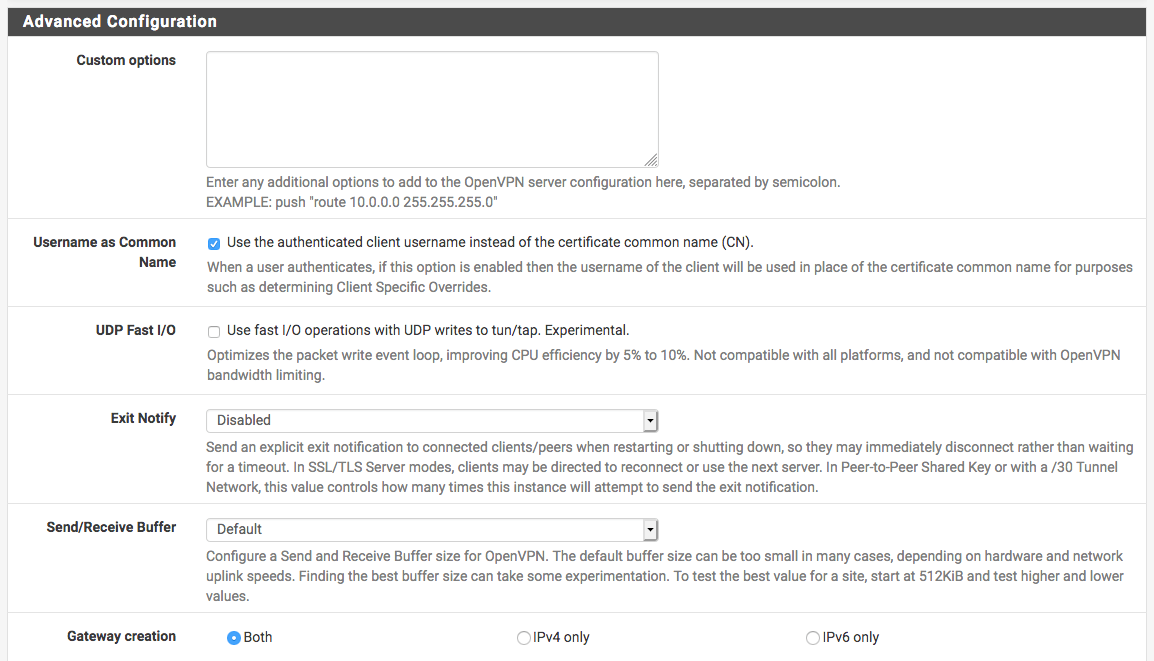
-
i have it on both side on my site to site i think.. let me check what i have..
yes, it's mandatory to have the same settings on both side or you get this error
FRAG_IN error flags=0x2a187bf3: FRAG_TEST not implemented -
-
Just tried on two test firewalls.
Hint: Apply on client first , then on server.
1:
I applied the fix on the client , then the server , client disconnected then reconnected and came up.2:
I applied the fix on server , then client disconnected and was "lost"
I saw these on the serverOct 14 08:43:01 openvpn 10921 FRAG_IN error flags=0xfb00001d: bad fragment size Oct 14 08:43:00 openvpn 10921 FRAG_IN error flags=0xfb00001d: bad fragment sizeCame up after i did a HTTPS to Outside , and applied the client fix.
I'd recommend to have a HTTPS access to the "Outside ip" (NON VPN based) , just in case ...
Or you prob could remove the server fix , and do it in reverse order./Bingo