Failover does not work
-
Hi All,
I have a system with two WANs, to same ISP, but on separate connections. I am trying to setup failover only, such that if the main fails it automatically switches to the backup and when the main returns it is automatically reconnected. I have tried two ways of configuring this, one that used the "Floating" firewall rules, but that did not work. The second is to configure Gateway groups with the main as tier 1 and the backup as tier 2 and viseversa. The LAN firewall rules is configured also, but this still does not work. For testing I disconnected the ethernet cable from WAN1.
Any new procedure to get failover working? -
@econst said in Failover does not work:
Any new procedure to get failover working?
Hi,
Nope, such does not exist...

- it always works that way - GW group + tier
https://docs.netgate.com/pfsense/en/latest/multiwan/load-balance-and-failover.html
https://docs.netgate.com/pfsense/en/latest/multiwan/index.html
https://www.youtube.com/channel/UC3Cq2kjCWM8odzoIzftS04A/videos+++edit:
by the way, I’ll tell you that two connections from same ISP, anyway don’t mean redundancy
(as these are usually ruined at the same time)therefore, "failover" makes no sense, possibly just "load balancing"
unless it is one not ADSL the other is DOCSIS or GPON, etc.but the problems at the ISP are usually global, not system dependent
hmmm, that's not entirely true either, so for "failover", I'd use two independent ISPs like cable and 4G LTE
-
You only have to setup the gateway group for failover as outlined here.
https://docs.netgate.com/pfsense/en/latest/multiwan/load-balance-and-failover.html?highlight=failoverThen make sure your default gateway IPV4 is set to use gateway group you just set up and not automatic.
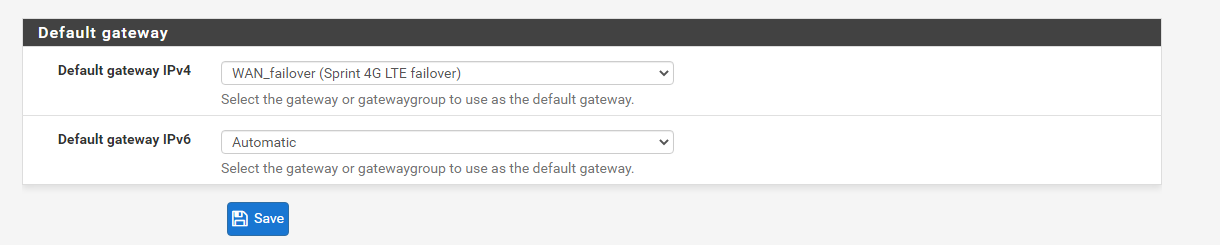
Interface rules have nothing to do with failover working. If you're not sure if you have your interface rules setup right, use the default any <> any rules for the internal interfaces.
-
@Raffi_
Hi Raffi -

-
I've already taken it off this COVID stuff, there is a separate topic about this...

I just wanted to know, everything is fine now, -with younasty world

-
Yup, everything is good here. I hope the same for you.
-
@Raffi_ said in Failover does not work:
I hope the same for you.
I still can't travel, there was 6 flight cancellations in 3 weeks, hahaha
but at least I’m healthy and my family too, that’s the point

-
Thanks for the response. I had read those guides you posted but as following this: https://www.cyberciti.biz/faq/howto-configure-dual-wan-load-balance-failover-pfsense-router/#:~:text=A%20dual%20wan%20setup%20allows,automatically%20to%20a%20backup%20connection.
So according to your guide, i just need to create one gateway group and then set that as the default IPV4 gateway?
-
Yes, that should be it.
-
Will this way automatically switch back when the failed member is reconnected?
Why all the other people's guides? Makes it confusing. Did you read the one I sent?
-
@econst said in Failover does not work:
Why all the other people's guides? Makes it confusing.
I would stick to the Netgate guides and max... Lawrence Youtube, these are sure resources
+++edit:
-
@econst said in Failover does not work:
Will this way automatically switch back when the failed member is reconnected?
Yes, when the failed member is reconnected pfsense will automatically switch NEW connections to the reconnected tier 1 gateway if its status is up. Notice how I emphasise new connections, because any existing states that were created on the tier 2 gateway will remain connected through that link until the states expire, either organically or manually closed by each client/server or by you going into the firewall states and killing them.
Why all the other people's guides? Makes it confusing. Did you read the one I sent?
I looked through that guide really quickly and it made everything way more complicated than it has to be. I would suggest you remove anything that guide told you to do. You shouldn't need any special firewall rules. Also, you don't have to put anything in the monitor IP address. By default leaving it blank for each gateway will ping your gateway address and normally that's the best option. Unless your gateway doesn't like responding to ping, then you may need another external address. You would know that right away though if you're getting no response.
-
@DaddyGo I ack your previous comments on redundancy, but there are times when only one link goes down. That's what I am trying to mitigate.
I'll give it a try and let you know. Thanks again.
-
@Raffi_ I have seen situations that if you don't put an external IP for the monitor IP and just use the local gateway address, when the link drops the gateway would still respond to the pings.
-
@econst said in Failover does not work:
@Raffi_ I have seen situations that if you don't put an external IP for the monitor IP and just use the local gateway address, when the link drops the gateway would still respond to the pings.
Interesting, yes in that case use the external address if that works best for you.
-
@econst said in Failover does not work:
if you don't put an external IP for the monitor IP and just use the local gateway address, when the link drops the gateway
There are many different opinions on this:
-
- it is possible to specify these known DNS server IPs (8.8.8.8 1.1.1.1. 9.9.9.9) as monitor IPs = my answer is absolutly NO
-
- ISP GW IP as a gateway monitor, realistic solution, but what about
the VPN IP GW
- ISP GW IP as a gateway monitor, realistic solution, but what about
therefore, I have established an external connection on one of our VPSs and are responding to PING from it
it is important not to get too far from NGFW as it will degrade the measurement results (RTT, RTTsd, Loss, Status)
BTW:
and influences the assessment of GW status -
-
@DaddyGo said in Failover does not work:
it is possible to specify these known DNS server IPs (8.8.8.8 1.1.1.1. 9.9.9.9) as monitor IPs = my answer is absolutly NO
In the past I have used 8.8.8.8 or 8.8.4.4 for years without issues. It may not be the best practice, but what is best and what works aren't always the same. What works for someone may not work for another. I guess that's why there are many opinions on it as you said. If there was one answer which was always correct, everyone would use that.
Edit, @econst In other words, if whatever monitor setting you have is working, leave it alone.
-
Thanks again guys. I'll try it later and let you know.
-
@Raffi_ said in Failover does not work:
In the past I have used 8.8.8.8 or 8.8.4.4 for years without issues. It may not be the best practice, but what is best and what works aren't always the same.
Yes, sure....
 - but
- butI used this for a long time... DNS server PING response... for GW monitor
(btw: some ISPs block PING requests that are constantly pointing to DNS servers)but I realized that the response time of DNS servers varies depending on their load, so I don't get exact values about the status of my GW
in the same data center where we have pfSense devices, I created a VPS for this purpose and also log GW(s) monitor PINGs on it
- so I kills two birds with one stone
I get a concrete picture of our GW status from several directions
- so I kills two birds with one stone