pfBlockerNG and Chrome
-
Hello
I have been searching a long time why the pfBlockerNG was NOT blocking sites in my DNSBL blacklist.... it was completly transparent as if pfBlockerNG was not there???
Then I discover in the parameters of Chrome the following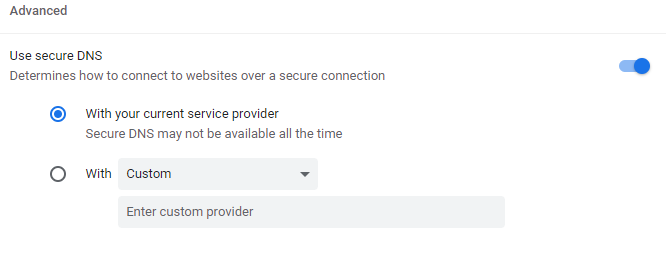
And there was the "solution" if I turn that off in Chrome all my bad sites where blocked as expected if I turn it back on the sites where not blocked anymore!
Is there something to overcome that because as different users will connect to my network I have no waty to check the setting of that Chrome parameter ?
Thanks for your help
Pierre -
@pierrelyon said in pfBlockerNG and Chrome:
pfBlockerNG was NOT blocking sites in my DNSBL blacklist..
Hi,
welcome to the real world

it’s the sleazy Chrome, uses ilyne stuff like DoH (a hat sucks), do this:
https://forum.netgate.com/topic/157500/blocking-dns-over-https-seems-the-only-way-is-to-fire-a-shotgun-at-itthere is no way to solve your question at once, no AD
+++edit:
it is very important that all DNS requests point to the pfSense box, manually or via DHCP, no matter
-
Does that switch in Chrome force DNS over HTTPS or just TLS (Port 853)? I have a separate VLAN for all of my IoT devices, and use a NAT forward to reroute ports 53 & 853 to pfSense for DNS. But I've seen some devices (e.g. Neato) hardware 8.8.8.8 over 443 for all DNS requests. No way to capture/fix that.
-
@Draco said in pfBlockerNG and Chrome:
Does that switch in Chrome force DNS over HTTPS or just TLS (Port 853)?
Chrome switch = DoT
and DoH
Chrome disable DoH:chrome://flags/#dns-over-https
Check: https://www.cloudflare.com/ssl/encrypted-sni/
FireFox:
about:config
network.trr.mode 5https://support.mozilla.org/en-US/kb/firefox-dns-over-https#firefox:win10:fx82
with IoT,...... you probably won't be able to do anything because the built - in firmware is dependent on DNS request via DoH-use in this case
if you disable the device's predefined DNS method (by an external device or method) way, it will not work
I recommend it to you again:
https://forum.netgate.com/topic/157500/blocking-dns-over-https-seems-the-only-way-is-to-fire-a-shotgun-at-it/30 -
@Draco said in pfBlockerNG and Chrome:
Does that switch in Chrome force DNS over HTTPS or just TLS (Port 853)?
Chrome switch = DoT
and DoH
Chrome disable DoH:chrome://flags/#dns-over-https
Check: https://www.cloudflare.com/ssl/encrypted-sni/
FireFox:
about:config
network.trr.mode 5https://support.mozilla.org/en-US/kb/firefox-dns-over-https#firefox:win10:fx82
with IoT you probably won't be able to do anything because the built - in firmware is dependent on DNS request via DoH-use in this case
if you disable the device's predefined DNS method (by an external device or method) way, it will not work
I recommend it to you again:
https://forum.netgate.com/topic/157500/blocking-dns-over-https-seems-the-only-way-is-to-fire-a-shotgun-at-it/30 -
@Draco
There are some feeds in PFBLOCKER now that you can use to block IPV4 and IPV6 DNS, 'The GreatWall' lists. I also use https://public-dns.info/nameservers.txt. I block port 53 and 443 to these lists, and 853 is not allowed out - as I am using resolving so am not forwarding to any public DNS servers. Just using the root servers for DNS which is the PFSense default. And of course, the NAT redirect of 53. I can see my IOT stuff (Kindles, phones) hitting my DNS servers in IPV4 and IPV6, and see some NAT redirects. Just run around plugging the holes, and the IOT stuff ends up using my DNS because there is nothing else. -
@Tzvia Oh, I like that idea -- blocking SSL to DNS servers. Unfortunately for my IoT devices that hardwire that into their code, I suspect they might fail if I did that. I think I'll try just logging those requests for awhile to see what I find. Thanks!
-
@Draco Watching will show you that they are going to hard-coded DNS, but we know that already. The only way to tell if they will fall back to DHCP options or the default gateway is to block and see what they do. I ran around the house power cycling everything (and rebooting PFSense to clear cache/states and start fresh) and tested them all. My IOT is printers, TVs, phones, blueray players, Kindles and the old playstation3. So far, so good, none of them barfed at my settings. The newer things seem to fall back to what is in DHCP options, querying my DNS servers in ipv6, and the older stuff in ipv4. I see the occasional 8.8.8.8 on 53 being redirected, and some MDNS broadcasts on 5353 but everything is working.
-
Temporary fix is to disable secure DNS in chrome here:
chrome://settings/security
Scroll down the page until you see :
Use secure DNS
Determines how to connect to websites over a secure connectionAnd disable it.
I believe this is because PfBLOCKER uses an unsecure page to display a note to the user:
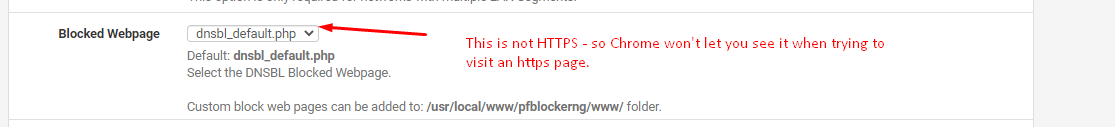
I haven't figured out yet how to make PfBlocker display a secure page.
-
@ihavealegohead: Yes, I know about the Chrome settings, but I am more concerned with dealing with this globally, not browser by browser. Also with my IoT devices that hardwire access (e.g. 8.8.8.8 over HTTPS). It seems I've gotten rid of the last of those devices, since a floating rule I put in place to detect HTTPS connections to DNS servers is no longer getting hits.
As for pfBlocker displaying a secure page: if it blocks an HTTPS page, your browser will never show it to you. The certificate in use at that moment is an internal pfBlocker cert, while the browser is expecting to see a certificate for the domain name you entered (while it is asked to show the internal pfBlocker SITE BLOCKED page). Ergo there will always be a certificate mismatch.