iPhone vs. pfSense - Schwierigkeiten beim Aufbau eines IKEv2 VPN
-
Hallo,
ich bin der Anleitung unter IPsec VPN für mobile Benutzer auf der pfSense oder OPNsense Firewall einrichten gefolgt, um ein VPN zwischen einem iPhone (IOS 13.4.1) und einer pfSense einzurichten.
Das klappt nicht :-(
Der Neustart der pfSense und des VPN-Dienstes sieht so aus:
Nov 2 15:13:34 charon 15[CFG] added configuration 'con-mobile' Nov 2 15:13:34 charon 15[CFG] loaded certificate "CN=hostname.beim.dyndns, C=DE, ST=Bremen, L=Bremen, O=MEIN, OU=LAN" from '/var/etc/ipsec/ipsec.d/certs/cert-1.crt' Nov 2 15:13:34 charon 15[CFG] adding virtual IP address pool 11.12.13.0/24 Nov 2 15:13:34 charon 15[CFG] keyexchange=ikev2 Nov 2 15:13:34 charon 15[CFG] mediation=no Nov 2 15:13:34 charon 15[CFG] sha256_96=no Nov 2 15:13:34 charon 15[CFG] dpdaction=1 Nov 2 15:13:34 charon 15[CFG] dpdtimeout=210 Nov 2 15:13:34 charon 15[CFG] dpddelay=35 Nov 2 15:13:34 charon 15[CFG] esp=aes256-sha256-modp2048,aes256-sha384-modp2048,aes256-sha512-modp2048,aes256gcm128-sha256-modp2048,aes256gcm128-sha384-modp2048,aes256gcm128-sha512-modp2048,aes256gcm96-sha256-modp2048,aes256gcm96-sha384-modp2048,aes256gcm96-sha512-modp2048,aes256gcm64-sha256-modp2048,aes256gcm64-sha384-modp2048,aes256gcm64-sha512-modp2048! Nov 2 15:13:34 charon 15[CFG] ike=aes256-sha256-modp2048! Nov 2 15:13:34 charon 15[CFG] eap_identity=%any Nov 2 15:13:34 charon 15[CFG] rightauth=eap-mschapv2 Nov 2 15:13:34 charon 15[CFG] rightdns=192.168.0.1 Nov 2 15:13:34 charon 15[CFG] rightsourceip=11.12.13.0/24 Nov 2 15:13:34 charon 15[CFG] right=%any Nov 2 15:13:34 charon 15[CFG] leftcert=/var/etc/ipsec/ipsec.d/certs/cert-1.crt Nov 2 15:13:34 charon 15[CFG] leftid=fqdn:hostname.beim.dyndns Nov 2 15:13:34 charon 15[CFG] leftauth=pubkey Nov 2 15:13:34 charon 15[CFG] leftsubnet=192.168.0.0/24,192.168.72.0/24 Nov 2 15:13:34 charon 15[CFG] left=192.168.178.10 Nov 2 15:13:34 charon 15[CFG] conn con-mobile Nov 2 15:13:34 charon 15[CFG] received stroke: add connection 'con-mobile' Nov 2 15:13:34 ipsec_starter 26518 'bypasslan' shunt PASS policy installed Nov 2 15:13:34 charon 05[CFG] received stroke: route 'bypasslan' Nov 2 15:13:34 charon 16[CFG] added configuration 'bypasslan' Nov 2 15:13:34 charon 16[CFG] mediation=no Nov 2 15:13:34 charon 16[CFG] sha256_96=no Nov 2 15:13:34 charon 16[CFG] dpdtimeout=150 Nov 2 15:13:34 charon 16[CFG] dpddelay=30 Nov 2 15:13:34 charon 16[CFG] rightsubnet=192.168.0.0/24,2a02:8109:dc0:481a::/64 Nov 2 15:13:34 charon 16[CFG] right=%any Nov 2 15:13:34 charon 16[CFG] leftsubnet=192.168.0.0/24,2a02:8109:dc0:481a::/64 Nov 2 15:13:34 charon 16[CFG] left=%any Nov 2 15:13:34 charon 16[CFG] conn bypasslan Nov 2 15:13:34 charon 16[CFG] received stroke: add connection 'bypasslan' Nov 2 15:13:34 ipsec_starter 26518 charon (26716) started after 460 ms Nov 2 15:13:34 charon 00[JOB] spawning 16 worker threads Nov 2 15:13:34 charon 00[LIB] loaded plugins: charon unbound aes des blowfish rc2 sha2 sha1 md4 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey ipseckey pem openssl fips-prf curve25519 xcbc cmac hmac drbg curl attr kernel-pfkey kernel-pfroute resolve socket-default stroke vici updown eap-identity eap-sim eap-md5 eap-mschapv2 eap-dynamic eap-radius eap-tls eap-ttls eap-peap xauth-generic xauth-eap xauth-pam whitelist addrblock counters Nov 2 15:13:34 charon 00[CFG] loaded 0 RADIUS server configurations Nov 2 15:13:34 charon 00[CFG] opening triplet file /usr/local/etc/ipsec.d/triplets.dat failed: No such file or directory Nov 2 15:13:34 charon 00[CFG] loaded EAP secret for jka Nov 2 15:13:34 charon 00[CFG] loaded RSA private key from '/var/etc/ipsec/ipsec.d/private/cert-1.key' Nov 2 15:13:34 charon 00[CFG] loading secrets from '/var/etc/ipsec/ipsec.secrets' Nov 2 15:13:34 charon 00[CFG] loading crls from '/usr/local/etc/ipsec.d/crls' Nov 2 15:13:34 charon 00[CFG] loading attribute certificates from '/usr/local/etc/ipsec.d/acerts' Nov 2 15:13:34 charon 00[CFG] loading ocsp signer certificates from '/usr/local/etc/ipsec.d/ocspcerts' Nov 2 15:13:34 charon 00[CFG] loading aa certificates from '/usr/local/etc/ipsec.d/aacerts' Nov 2 15:13:34 charon 00[CFG] loaded ca certificate "CN=pfsense.mein.lan, C=DE, ST=Bremen, L=Bremen, O=MEIN, OU=LAN" from '/usr/local/etc/ipsec.d/cacerts/552649c0.0.crt' Nov 2 15:13:34 charon 00[CFG] loading ca certificates from '/usr/local/etc/ipsec.d/cacerts' Nov 2 15:13:34 charon 00[CFG] ipseckey plugin is disabled Nov 2 15:13:34 charon 00[CFG] loading unbound trust anchors from '/usr/local/etc/ipsec.d/dnssec.keys' Nov 2 15:13:34 charon 00[CFG] loading unbound resolver config from '/etc/resolv.conf' Nov 2 15:13:34 charon 00[NET] enabling UDP decapsulation for IPv6 on port 4500 failed Nov 2 15:13:34 charon 00[KNL] unable to set UDP_ENCAP: Invalid argument Nov 2 15:13:34 charon 00[DMN] Starting IKE charon daemon (strongSwan 5.8.4, FreeBSD 11.3-STABLE, amd64) Nov 2 15:13:33 ipsec_starter 26074 Starting strongSwan 5.8.4 IPsec [starter]...Hier ein fehlerhafter Verbindungsversuch:
Nov 2 15:15:50 charon 12[IKE] <bypasslan|1> IKE_SA bypasslan[1] state change: CONNECTING => DESTROYING Nov 2 15:15:50 charon 12[NET] <bypasslan|1> sending packet: from 192.168.0.1[4500] to 192.168.0.110[4500] (80 bytes) Nov 2 15:15:50 charon 12[ENC] <bypasslan|1> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ] Nov 2 15:15:50 charon 12[IKE] <bypasslan|1> peer supports MOBIKE Nov 2 15:15:50 charon 12[IKE] <bypasslan|1> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding Nov 2 15:15:50 charon 12[IKE] <bypasslan|1> processing INTERNAL_DNS_DOMAIN attribute Nov 2 15:15:50 charon 12[IKE] <bypasslan|1> processing INTERNAL_IP6_DNS attribute Nov 2 15:15:50 charon 12[IKE] <bypasslan|1> processing INTERNAL_IP6_DHCP attribute Nov 2 15:15:50 charon 12[IKE] <bypasslan|1> processing INTERNAL_IP6_ADDRESS attribute Nov 2 15:15:50 charon 12[IKE] <bypasslan|1> processing INTERNAL_IP4_DNS attribute Nov 2 15:15:50 charon 12[IKE] <bypasslan|1> processing INTERNAL_IP4_DHCP attribute Nov 2 15:15:50 charon 12[IKE] <bypasslan|1> processing INTERNAL_IP4_NETMASK attribute Nov 2 15:15:50 charon 12[IKE] <bypasslan|1> processing INTERNAL_IP4_ADDRESS attribute Nov 2 15:15:50 charon 12[CFG] <bypasslan|1> no alternative config found Nov 2 15:15:50 charon 12[IKE] <bypasslan|1> peer requested EAP, config unacceptable Nov 2 15:15:50 charon 12[CFG] <bypasslan|1> selected peer config 'bypasslan' Nov 2 15:15:50 charon 12[CFG] <1> candidate "bypasslan", match: 1/1/24 (me/other/ike) Nov 2 15:15:50 charon 12[CFG] <1> looking for peer configs matching 192.168.0.1[hostname.beim.dyndns]...192.168.0.110[192.168.0.110] Nov 2 15:15:50 charon 12[ENC] <1> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr CPRQ(ADDR MASK DHCP DNS ADDR6 DHCP6 DNS6 DOMAIN) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr N(MOBIKE_SUP) ] Nov 2 15:15:50 charon 12[ENC] <1> unknown attribute type INTERNAL_DNS_DOMAIN Nov 2 15:15:50 charon 12[NET] <1> received packet: from 192.168.0.110[4500] to 192.168.0.1[4500] (512 bytes) Nov 2 15:15:50 charon 12[NET] <1> sending packet: from 192.168.0.1[500] to 192.168.0.110[500] (481 bytes) Nov 2 15:15:50 charon 12[ENC] <1> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(CHDLESS_SUP) N(MULT_AUTH) ] Nov 2 15:15:50 charon 12[IKE] <1> sending cert request for "CN=pfsense.mein.lan, C=DE, ST=Bremen, L=Bremen, O=MEIN, OU=LAN" Nov 2 15:15:50 charon 12[CFG] <1> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 Nov 2 15:15:50 charon 12[CFG] <1> configured proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048 Nov 2 15:15:50 charon 12[CFG] <1> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 Nov 2 15:15:50 charon 12[CFG] <1> proposal matches Nov 2 15:15:50 charon 12[CFG] <1> selecting proposal: Nov 2 15:15:50 charon 12[IKE] <1> IKE_SA (unnamed)[1] state change: CREATED => CONNECTING Nov 2 15:15:50 charon 12[IKE] <1> 192.168.0.110 is initiating an IKE_SA Nov 2 15:15:50 charon 12[CFG] <1> found matching ike config: %any...%any with prio 24 Nov 2 15:15:50 charon 12[CFG] <1> candidate: %any...%any, prio 24 Nov 2 15:15:50 charon 12[CFG] <1> looking for an IKEv2 config for 192.168.0.1...192.168.0.110 Nov 2 15:15:50 charon 12[ENC] <1> parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ] Nov 2 15:15:50 charon 12[NET] <1> received packet: from 192.168.0.110[500] to 192.168.0.1[500] (604 bytes)Ich habe diese Frage natürlich auch im anderen Forum platziert. Aber ich dachte mir, dass ich parallel dazu auch mal hier frage. Wenn ich "irgendwo" eine Lösung habe, kann ich die ja gerne crossposten.
Liebe Grüße,
Jörg -
@altmetaller Was mir gleich auffällt wäre das:
Nov 2 15:15:50 charon 12[NET] <1> received packet: from 192.168.0.110[500] to 192.168.0.1[500] (604 bytes)Du versuchst eine IPSec VPN Verbindung im gleichen Netz aufzubauen, das funktioniert natürlich nicht. Hast du das mal von extern, außerhalb deines Netzwerks getestet?
Wenn das intern funktionieren soll, muss folgender Haken bei den erweiterten Einstellungen raus.
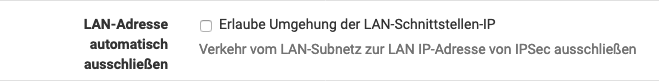
-
Hallo,
"sehr gut" beobachtet" :-)
Meine Firewall hat drei Netzwerkschnittstellen:
- WAN
- LAN
- DMZ
Das Handy hängt an der LAN-Schnittstelle.
Mein Ziel ist ein VPN mit Zugriff auf die DMZ, dass ich "immer eingeschaltet lassen kann". Der externe Hostname existiert daher doppelt:
- beim DynDNS-Anbieter (zeigt auf die Provider-IP)
- im lokalen DNS (zeigt auf die LAN-Schnittstelle der pfSense)
Dein Kommentar klopft mir tatsächlich gerade ein paar Schuppen hinter den Ohren hervor.
Aber - was wäre denn die korrekte Strategie? Ich habe keinen Bock, das VPN immer von Hand ein- und auszuschalten - abhängig davon, ob ich in meinem WLAN bin.
Gruß,
JörgEdit: Das VPN funktioniert perfekt! Es geht somit tatsächlich "nur" noch um die Vorgehensweise bzw. das Bedürfnis, das VPN nicht jedes Mal "von Hand" umschalten zu müssen :-)