Allow established/related traffic only? Coming from UniFi...
-
Hello all,
I'm configuring an SG-1100 box, to replace my Ubiquiti UniFi USG 3P. I now have the same VLANs set up in pfSense and they work on my UniFi switches. Now comes translating the firewall rules for those VLANs.
In UniFi, I have a basic "Allow all established/related traffic" rule so devices in adjacent VLANs can "talk back" but not start new connections:
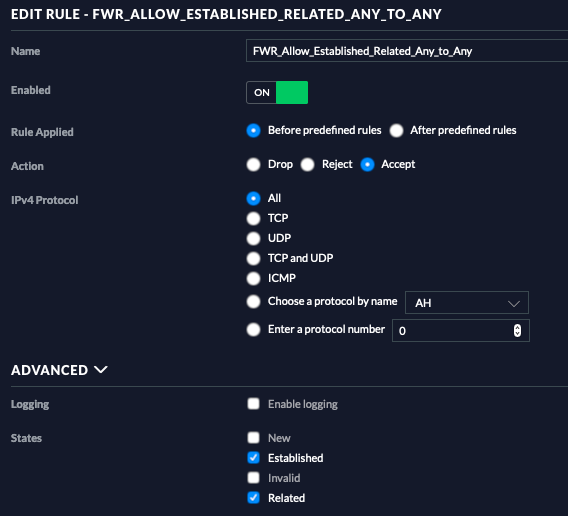
Let's assume I have VLAN 10 secure devices and VLAN 70 IoT. I want 10 to talk to 70 and establish a connection, but I don't want 70 to start new connections to 10.
My ruling concept is the following, rule order top to bottom:- allow established/related <any source> to <any destination>
- allow <all states> from VLAN10 to VLAN70
- block <all states> from VLAN70 to VLAN10
I can't seem to find an option to do this in pfSense. Should I go about doing this in a different way to accomplish the same?
Thanks!
PetePS I should have mentioned that the UniFi way of firewallling is to route all traffic to/from a VLAN by default, no restrictions. At the start, the rules list is empty and all traffic is allowed. If the aim is to block traffic, one must add a block rule (there are default WAN rules of course).
I already found out that pfSense works in the opposite way: no rules means all traffic is blocked. -
If you have vlan X and vlan Y
And you let vlan X talk to vlan Y, via rules on X interface - there are no rules need to be added on Y for it to be able to talk back.. The state you create from X to Y when you allowed the traffic would allow Y to talk back.
The vlan Y interface could have zero rules on it.. And you would still be able to talk back to X because of the state that was created. But Y would not be able to start a conversation with something in X, unless rules that allowed that were placed on interface Y.
UniFi way of firewallling is to route all traffic to/from a VLAN by default
With Pfsense, default is deny on all new vlans. The only network that gets default any any rule is the first (LAN).. Whenever you create a new vlan/network - it defaults to no rules (other than say hidden rules to allow dhcp when you enable dhcpd on that network).
If you want a new vlan to be able to start a conversation to anything - you would have to create the allow rules. But conversations started to it from another vlan would be allowed to return.
-
That is a brilliant explanation, thanks a lot. I've tested and it works! Kudos

-
Yeah I ran a usgp3 for my main router for a short amount of time.. I needed something quick and cheap after I updated my isp speed to 500.. My sg4860 was on back order.. So at 100 bucks - sure works..
While overall at that price point its not a bad little box.. But wow was firewalling a PITA compared to how easy it is with pfsense... Couldn't get it off my network fast enough once the netgate appliance got here..
My son is currently using the usg on his network.. It reports into my controller, and his flexHD ap.. So I can keep an eye on it.. But his network is just 1 flat network.. His TVs and him and his GF laptops and phones.. So not a lot of firewalling to have to be done on the usg.. And since it only he has 100mbps isp - the dpi even works out fine, etc.
Once you go pfsense, you won't be going back to unifi firewalls any time soon ;) To be honest it blows away most anything else I have worked on, juniper, checkpoint, cisco, palo, etc.
-
Can someone explain why ubiquity chose to not automatically create "talk back" rules like pfsense? They combine all "corporate" networks (and later call it "lan". confusing!) to one "interface". all "lan" subnets are wide open. I can understand these choices to make it easier for users.
But not integrating "talking back" rules is a failure imho. Is this deliberate? Just lazy? Is this a BSD vs Linux thing?
-
@mistere You prob have better luck asking that question over on their forums.
While there are many a unifi AP user here, and even some of their switches.. To their actual router/firewall devices - I doubt you will find many users here, since pretty much everyone here is because they use pfsense as their firewall router ;)
Why they do some of the stuff they do is questionable - WTF were they thinking putting just a 1gig interface on their wifi 6 (ax) access points? I'm at a complete loss there..
-
@mistere Just guessing here, but it might be that the little USG is not capable of going full statefull on firewalling internally between VLANs. The Talk back rule looks suspiciously like something you would do in a Switch ACL to allow return TCP traffic when there is no state. but I don’t know.
-
Well, i think here are more experts with actual low level firewall knowledge. Or experience with the design decision other brands made.
Probably there are some use cases for real one-way traffic (UDP?) in enterprise settings but i do not see the use cases for ubiquity customers. Not sure if we can actually mimic the same behaviour in pfsense if we want to.
It should really easy to automatically create the "talk back" rule. So, you would think this is deliberate. So, i am afraid i am missing something obvious. But it is probably just a stupid design :P
-
I was a USG user when I started learning VLANs and firewall rules. So to me it was the only way I knew at the time. For all I knew all systems would work the same. Boy was I surprised when I started using pfSense.
As pointed out above, pfSense is building states with every pass rule, which are basically invisible in the UI. There is no need to create talk back rules in the other VLAN. We (as pfSense users) are aware that by default, VLANs cannot start connections unless pass rules are created for that VLAN. As UniFi works completely reverse (all inter-VLAN traffic allowed by default) users need to create a block all traffic rule in each VLAN. This is just guessing on my part, but requiring to add state rules above the block rule may give starting users more insight in the logic of top down firewall rules. Actually I can't think of any use case where one would like to allow established/related traffic without also having the counter part rules on the VLAN that is initiating that traffic.
Pete