Block scanners / Custom list
-
Hi, I'm wondering if there is a feature that adds the scanners on wan to a block list automaticly? Or is there another way to do it? Thanks
-
Try something like this:-
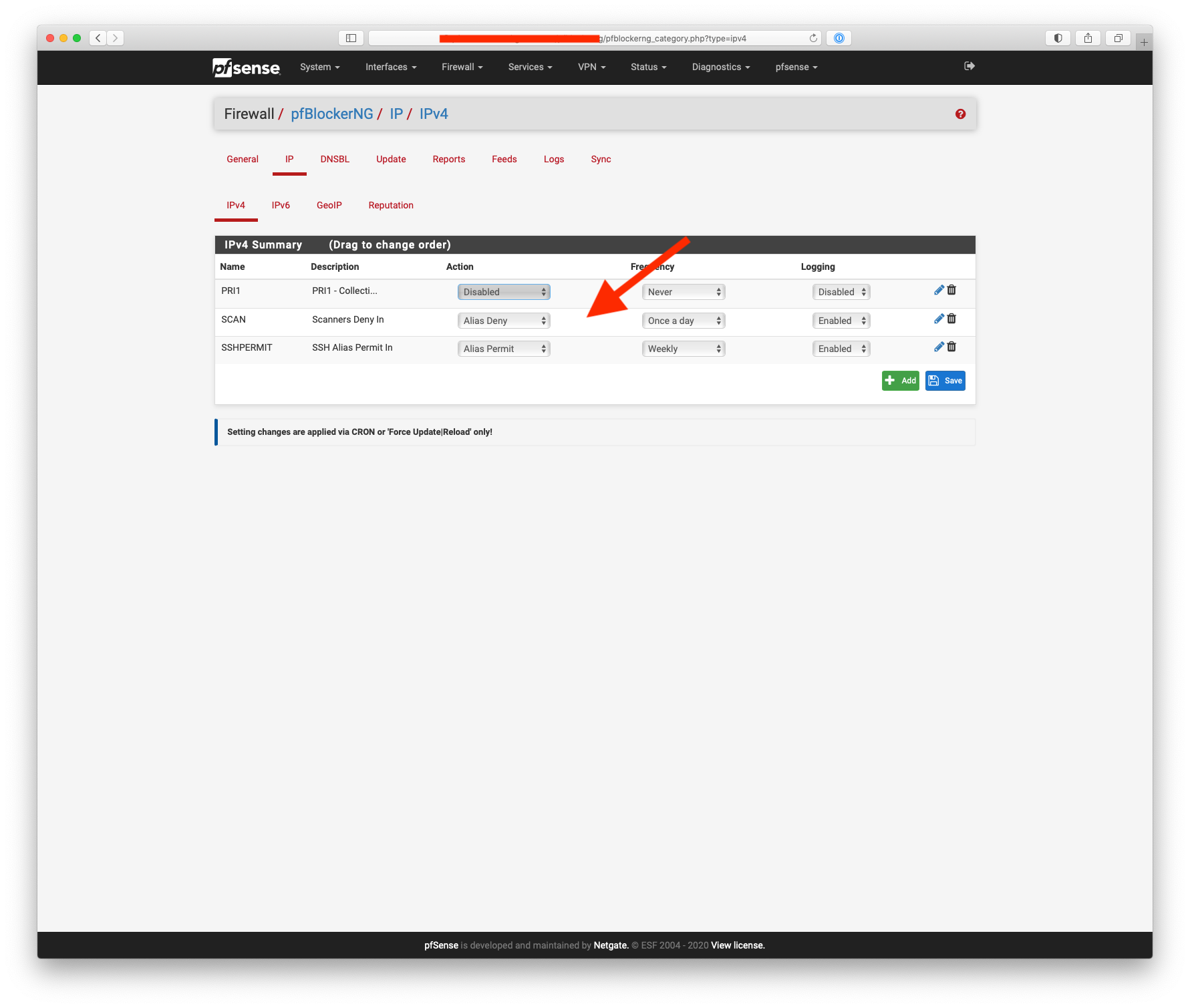
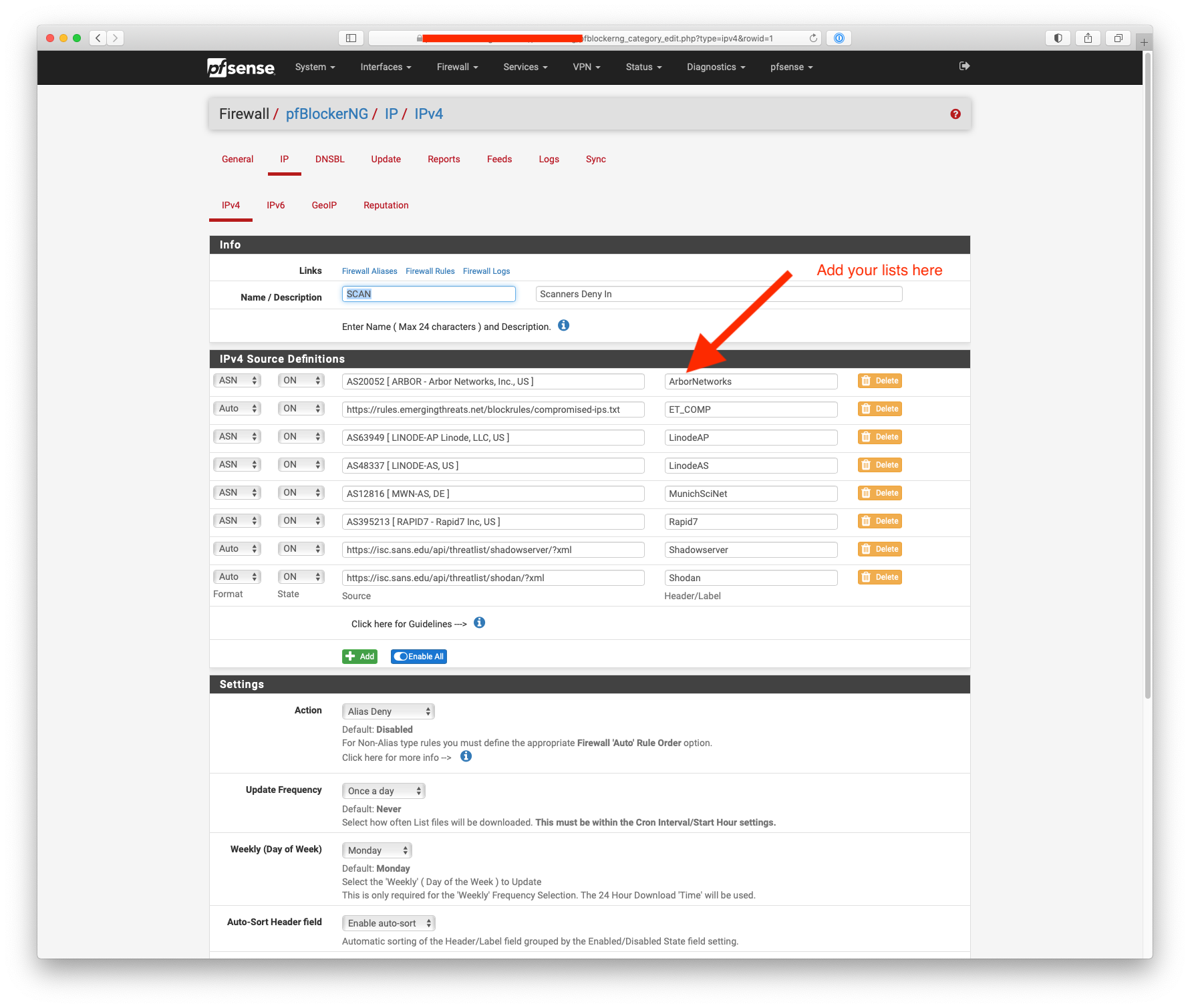
-
Nice, looks good.
Is there a way to record the scanners knocking on the wan and create my own list/contribute to a list?
Thanks -
Nope unless you were to also install snort on the wan interface.
The idea is to use block lists that are updated from elsewhere.
Do you do any port forwards on the wan to the lan?
-
Im not having anything open yet. Its just precaution. My idea was to block all outbound traffic to scanners. Im new in this, how does snort work?
-
You need to block inbound to the WAN interface, this is the default out the box.
Snort does does a pattern match and then blocks even if you have a pass rule.
The screen shots I posted are to create an alias that I use on a WAN interface block rule, next set of rules are allow rules for an IPsec VPN.
Rules are read from the top down.
-
Ok, have it running on the wan now. I wanted to set it up on all interfaces but 2gb of memory seem to be not enough. Im wondering if snort is dropping outbound connection if there is a compromised host on the lan side, when it is running on the wan side?
-
@o51
It depends on the rules if it drops outbound or inbound connections.
If I had 2Gb of RAM I wouldn’t run Snort & pfBlocker, especially if I didn’t have any port forwards.
-
Yeah, probably not the best idea but it works. Im thinking to run a hotspot and dont want to find myself feeding bots.