Not able to import CA certificate to use for OpenVPN Client
-
I am trying to configure OpenVPN client in pfsense 2.4.5-RELEASE-p1.
I have client cert and key, and the cert of the CA which generated both the server and the client cert. Using this artifacts with other OpenVPN Client Software works correctly and connects to the server.
In order to get the Ca in the Dropdown list to configure the Peer Certificate Authority field I try to import the CA cert into the Cert. Managers CA List. this gives me the error:
"The submitted certificate does not appear to be a Certificate Authority, import it on the Certificates tab instead."
It seems that this issue: https://redmine.pfsense.org/issues/7885 introduced a check that my ca does not pass! But why is this? It's a valid cert and it was used to create my client/server certs ( I do not need it as a 'usable CA' as the bug report askes for to be checked when importing CAs).
Is there some other way I can import my CA as 'trusted CA' only and not as 'usable Ca'!?
-
If it does not have that flag, then it is not a CA, and could not have issued certificates. Are you certain you are using the correct file?
Can you post the CA here? (without the key, of course)
-
@jimp said in Not able to import CA certificate to use for OpenVPN Client:
If it does not have that flag, then it is not a CA
Exactly... If it was a CA it would have that flag - you can check the cert with just openssl yourself you don't believe pfsense.
So I grabbed the acme CA..
C:\test>openssl.exe x509 -in test.crt -text Certificate: Data: Version: 3 (0x2) Serial Number: 0a:01:41:42:00:00:01:53:85:73:6a:0b:85:ec:a7:08 Signature Algorithm: sha256WithRSAEncryption Issuer: O = Digital Signature Trust Co., CN = DST Root CA X3 Validity Not Before: Mar 17 16:40:46 2016 GMT Not After : Mar 17 16:40:46 2021 GMT Subject: C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3 Subject Public Key Info: Public Key Algorithm: rsaEncryption RSA Public-Key: (2048 bit) Modulus: 00:9c:d3:0c:f0:5a:e5:2e:47:b7:72:5d:37:83:b3: 68:63:30:ea:d7:35:26:19:25:e1:bd:be:35:f1:70: 92:2f:b7:b8:4b:41:05:ab:a9:9e:35:08:58:ec:b1: 2a:c4:68:87:0b:a3:e3:75:e4:e6:f3:a7:62:71:ba: 79:81:60:1f:d7:91:9a:9f:f3:d0:78:67:71:c8:69: 0e:95:91:cf:fe:e6:99:e9:60:3c:48:cc:7e:ca:4d: 77:12:24:9d:47:1b:5a:eb:b9:ec:1e:37:00:1c:9c: ac:7b:a7:05:ea:ce:4a:eb:bd:41:e5:36:98:b9:cb: fd:6d:3c:96:68:df:23:2a:42:90:0c:86:74:67:c8: 7f:a5:9a:b8:52:61:14:13:3f:65:e9:82:87:cb:db: fa:0e:56:f6:86:89:f3:85:3f:97:86:af:b0:dc:1a: ef:6b:0d:95:16:7d:c4:2b:a0:65:b2:99:04:36:75: 80:6b:ac:4a:f3:1b:90:49:78:2f:a2:96:4f:2a:20: 25:29:04:c6:74:c0:d0:31:cd:8f:31:38:95:16:ba: a8:33:b8:43:f1:b1:1f:c3:30:7f:a2:79:31:13:3d: 2d:36:f8:e3:fc:f2:33:6a:b9:39:31:c5:af:c4:8d: 0d:1d:64:16:33:aa:fa:84:29:b6:d4:0b:c0:d8:7d: c3:93 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Basic Constraints: critical CA:TRUE, pathlen:0 X509v3 Key Usage: critical Digital Signature, Certificate Sign, CRL Sign Authority Information Access: OCSP - URI:http://isrg.trustid.ocsp.identrust.com CA Issuers - URI:http://apps.identrust.com/roots/dstrootcax3.p7c X509v3 Authority Key Identifier: keyid:C4:A7:B1:A4:7B:2C:71:FA:DB:E1:4B:90:75:FF:C4:15:60:85:89:10 X509v3 Certificate Policies: Policy: 2.23.140.1.2.1 Policy: 1.3.6.1.4.1.44947.1.1.1 CPS: http://cps.root-x1.letsencrypt.org X509v3 CRL Distribution Points: Full Name: URI:http://crl.identrust.com/DSTROOTCAX3CRL.crl X509v3 Subject Key Identifier: A8:4A:6A:63:04:7D:DD:BA:E6:D1:39:B7:A6:45:65:EF:F3:A8:EC:A1 Signature Algorithm: sha256WithRSAEncryption dd:33:d7:11:f3:63:58:38:dd:18:15:fb:09:55:be:76:56:b9: 70:48:a5:69:47:27:7b:c2:24:08:92:f1:5a:1f:4a:12:29:37: 24:74:51:1c:62:68:b8:cd:95:70:67:e5:f7:a4:bc:4e:28:51: cd:9b:e8:ae:87:9d:ea:d8:ba:5a:a1:01:9a:dc:f0:dd:6a:1d: 6a:d8:3e:57:23:9e:a6:1e:04:62:9a:ff:d7:05:ca:b7:1f:3f: c0:0a:48:bc:94:b0:b6:65:62:e0:c1:54:e5:a3:2a:ad:20:c4: e9:e6:bb:dc:c8:f6:b5:c3:32:a3:98:cc:77:a8:e6:79:65:07: 2b:cb:28:fe:3a:16:52:81:ce:52:0c:2e:5f:83:e8:d5:06:33: fb:77:6c:ce:40:ea:32:9e:1f:92:5c:41:c1:74:6c:5b:5d:0a: 5f:33:cc:4d:9f:ac:38:f0:2f:7b:2c:62:9d:d9:a3:91:6f:25: 1b:2f:90:b1:19:46:3d:f6:7e:1b:a6:7a:87:b9:a3:7a:6d:18: fa:25:a5:91:87:15:e0:f2:16:2f:58:b0:06:2f:2c:68:26:c6: 4b:98:cd:da:9f:0c:f9:7f:90:ed:43:4a:12:44:4e:6f:73:7a: 28:ea:a4:aa:6e:7b:4c:7d:87:dd:e0:c9:02:44:a7:87:af:c3: 34:5b:b4:42 -----BEGIN CERTIFICATE----- MIIEkjCCA3qgAwIBAgIQCgFBQgAAAVOFc2oLheynCDANBgkqhkiG9w0BAQsFADA/ MSQwIgYDVQQKExtEaWdpdGFsIFNpZ25hdHVyZSBUcnVzdCBDby4xFzAVBgNVBAMT DkRTVCBSb290IENBIFgzMB4XDTE2MDMxNzE2NDA0NloXDTIxMDMxNzE2NDA0Nlow SjELMAkGA1UEBhMCVVMxFjAUBgNVBAoTDUxldCdzIEVuY3J5cHQxIzAhBgNVBAMT GkxldCdzIEVuY3J5cHQgQXV0aG9yaXR5IFgzMIIBIjANBgkqhkiG9w0BAQEFAAOC AQ8AMIIBCgKCAQEAnNMM8FrlLke3cl03g7NoYzDq1zUmGSXhvb418XCSL7e4S0EF q6meNQhY7LEqxGiHC6PjdeTm86dicbp5gWAf15Gan/PQeGdxyGkOlZHP/uaZ6WA8 SMx+yk13EiSdRxta67nsHjcAHJyse6cF6s5K671B5TaYucv9bTyWaN8jKkKQDIZ0 Z8h/pZq4UmEUEz9l6YKHy9v6Dlb2honzhT+Xhq+w3Brvaw2VFn3EK6BlspkENnWA a6xK8xuQSXgvopZPKiAlKQTGdMDQMc2PMTiVFrqoM7hD8bEfwzB/onkxEz0tNvjj /PIzark5McWvxI0NHWQWM6r6hCm21AvA2H3DkwIDAQABo4IBfTCCAXkwEgYDVR0T AQH/BAgwBgEB/wIBADAOBgNVHQ8BAf8EBAMCAYYwfwYIKwYBBQUHAQEEczBxMDIG CCsGAQUFBzABhiZodHRwOi8vaXNyZy50cnVzdGlkLm9jc3AuaWRlbnRydXN0LmNv bTA7BggrBgEFBQcwAoYvaHR0cDovL2FwcHMuaWRlbnRydXN0LmNvbS9yb290cy9k c3Ryb290Y2F4My5wN2MwHwYDVR0jBBgwFoAUxKexpHsscfrb4UuQdf/EFWCFiRAw VAYDVR0gBE0wSzAIBgZngQwBAgEwPwYLKwYBBAGC3xMBAQEwMDAuBggrBgEFBQcC ARYiaHR0cDovL2Nwcy5yb290LXgxLmxldHNlbmNyeXB0Lm9yZzA8BgNVHR8ENTAz MDGgL6AthitodHRwOi8vY3JsLmlkZW50cnVzdC5jb20vRFNUUk9PVENBWDNDUkwu Y3JsMB0GA1UdDgQWBBSoSmpjBH3duubRObemRWXv86jsoTANBgkqhkiG9w0BAQsF AAOCAQEA3TPXEfNjWDjdGBX7CVW+dla5cEilaUcne8IkCJLxWh9KEik3JHRRHGJo uM2VcGfl96S8TihRzZvoroed6ti6WqEBmtzw3Wodatg+VyOeph4EYpr/1wXKtx8/ wApIvJSwtmVi4MFU5aMqrSDE6ea73Mj2tcMyo5jMd6jmeWUHK8so/joWUoHOUgwu X4Po1QYz+3dszkDqMp4fklxBwXRsW10KXzPMTZ+sOPAveyxindmjkW8lGy+QsRlG PfZ+G6Z6h7mjem0Y+iWlkYcV4PIWL1iwBi8saCbGS5jN2p8M+X+Q7UNKEkROb3N6 KOqkqm57TH2H3eDJAkSnh6/DNFu0Qg== -----END CERTIFICATE----- C:\test>You will notice the
X509v3 extensions: X509v3 Basic Constraints: critical CA:TRUE, pathlen:0 -
Thx. for your replies and the info of how to check with openssl (I only had my windows cert display and was not able to find this 'extension' and how it should look like).
Yes, my Ca cert has not set this flag.
I see my client cert having this self signed Ca cert as root and as mentioned: if I use this in my Windows OpenVpn GUI client (2.5.0) everything works fine. So for OpenVPN this flag seems not to be an issue. I also rechecked the Log. There is no warning about the CA being suspicious or something like this.
I got this certs from my admin. No Idea how and with which tools he generated the certs. And as everybody else uses windows clients only I doubt if I will get a change there (nevertheless I will feedback this info to him) ...
For now I am looking for a workaround here. Maybe I can set "ca cafile.crt" as custom, option in advanced features !? Will this work and override the ca I have to select in 'Peer Authority' (could use my own self signed pfSense CA here as a dummy).
But therefore I would have to copy the cert to some location on my own (will try that some when next evenings ...) -
@RobertK66 said in Not able to import CA certificate to use for OpenVPN Client:
I got this certs from my admin.
admin ?
Aren't you the pfSense admin ?If you want to set up OpenVPN, on pfSense you could actually import a CA cert from 'elsewhere' :
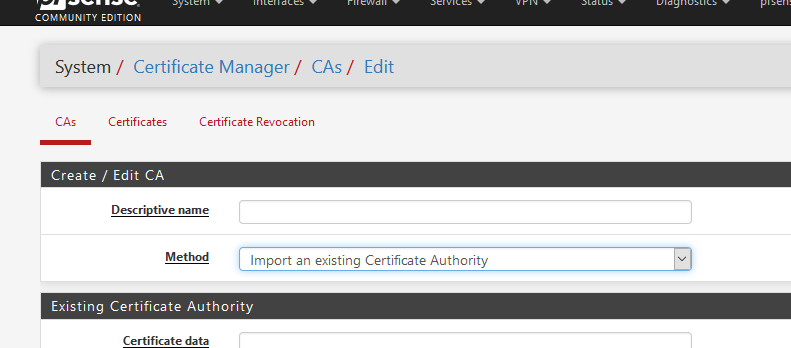
It should be a CA of course.
Way more easy : go here and create your own :
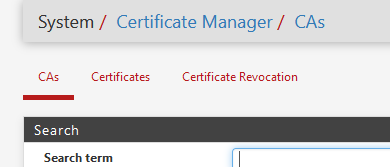
and hit the green Add button at the bottom of the page, fill in what you the descriptive name and other fields if needed, hit Save and done.
You have your own CA that can be sued to create certs for your OpenVPN server. -
@Gertjan: Yes I am the admin of my pfSense :-). But it happens to be that I want/have to join a OpenVpn setup by somebody else ;-). So this client certs where generated by some other admin - not me.
I know that I can set up my own CA and a OpenVpn server and so on on my side. But that's not the point here. So thx for info. But exactly the import step fails, because I have a 'not so valid' CA cert ;-) ....
-
Joining an OpenVPN setup means to mean :
You (your pfSense) or your PC (Phone, whatever) is the client and the someone is hosting the OpenVPN server.
You will connect to this OpenVPN server using your OpenVPN client which could be pfSense.
In that case, the other party would send you an opvn file, which could include cert info, or send a opvn file with separate certificate files.
One of these has to be imported as the CA file.That changes everything.
If you host a OpenVPN server then people join your Open (pfSense based) server. In this case you would probably create a CA and based certs from if for every user etc.
So, what are you setting up ?
-
Ok, maybe i was not clear enough in my first message but I want to join a remote VPN by using OpenVPN Client on my pfSense!
I have not received a opvn file. I received only the certs. I created the opvn config file by myself. referencing the received certs and the Windows OpenVPN client is completely happy with that. It connects and everything works.I only wish to use my pfSense now, because I want to have this work from every node in my LAN here.
-
Well how would your windows client connect if you don't have the CA file? What is your config - is this specific vpn service you can point to.. there are many of them - they normally have a webite ;) Which is it?
-
I have the CA file (Its a self signed certificate from the guy who setup his OpenVPN server on his side. In my Windows OpenVPN Client I configured the 3 files I have within my test.ovpn file:
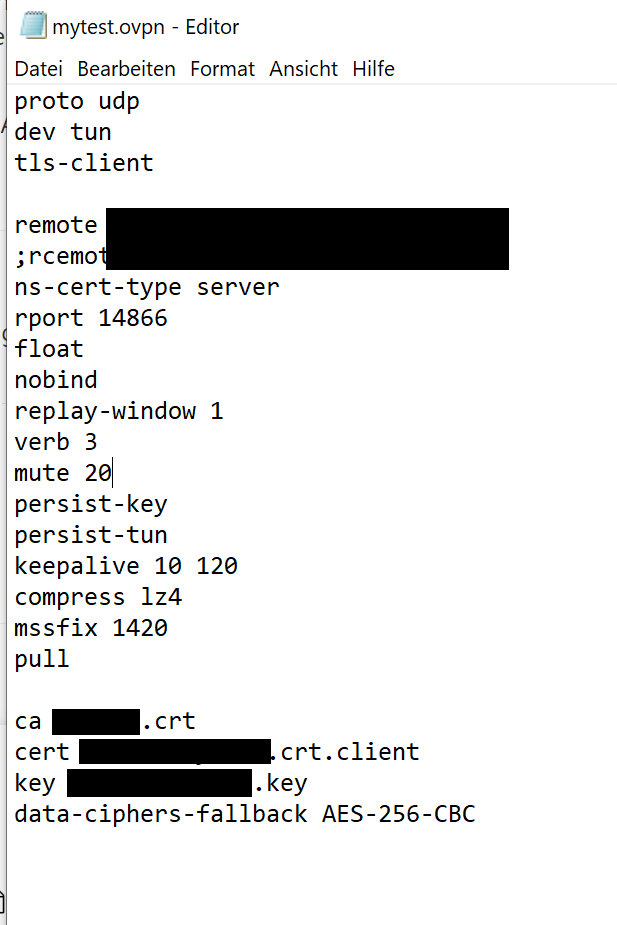
For OpenVPN Client this makes it work!
On pfSense:
I successfully imported the client certificate with its private key into the CertManagers Certificate page, but I am - like stated above - not able to use the <wahtevername>.crt content (paste the hole string ---- Begin blablabla to ---- END ) to import a CA on the Certificate Managers CA page. -
I perfectly understand now - why pfSense refuses this import.
because it is obvious, that my CA.cert does not fulfill the correct specification of a CA cert. - So now - until I get the other side to correct all this stuff - I am just curious if I can make some workaround to use this ca.crt like the OpenVPN Client under windows does
.... -
Another Info:
prior to opening this issue here I also tried to import the <ca>.crt into my Windows 10 '"Trusted Root Certification Authorities Store". This only because I suspected this cert to be somehow incorrect ;-). Windows does also accept this without warning!
So I already assumed the pfSense Software to be 'too strict' on this checking. But Its not up to me to judge who is doing it right or wrong here in this case ;-). -
remote-cert-tls server
ns-cert-type was deprecated long time ago..
Compress lz4?
Yeah that is not what I would call a current or secure setup..
-
@johnpoz said in Not able to import CA certificate to use for OpenVPN Client:
Yeah that is not what I would call a current or secure setup..
Yeah ok, but that's not the issue here, or is it? If the setup is not good/secure enough to be allowed to work we should file a bug with OpenVPN for that. But fact is I can connect with current version of OpenVPN but I can't with pfSense ...
-
Not a bug that you setup an insecure config..
Be it that the windows doesn't validate its actually a CA cert.. Have never tested that - but doesn't even look like your verify that..
The client should validate that CA is a CA and that your client cert was issued/signed by it..
I would have to do some testing on what exactly happens if you use some none CA tagged cert in windows client. But pfsense isn't going to let you install cert into the cert manager unless its actually marked as a CA..
I would suggest you get with whoever setup this openvpn instance to fix their shit ;) And compression is not secure.. What version of openvpn are you even using? Lets see the log of this connection..
You should see a verify at min.
exampleNov 10 06:12:04 openvpn 50634 VERIFY OK: depth=1, CN=OpenVPN CA -
I use OPENVPN GUI 11.20.0.0/2.5.0 and I get a Verify in the Log:

-
You only get the 1 verify.. You should see a verify for the server cert and the ca..
I would be curious to see who issued the cert your using.. Does it list the other cert as the issuing?
Can you verify it with the CA cert you have - example
C:\test>openssl verify -CAfile HomeCA.crt sg4860.crt sg4860.crt: OK -
@johnpoz said in Not able to import CA certificate to use for OpenVPN Client:
But pfsense isn't going to let you install cert into the cert manager unless its actually marked as a CA..
Thx, I got it :-) (some hours ago ;-) )!
Only question I have remaining is about a possible workaround. If there is none - ok, fine with me.....
-
Thats how opemnssl verifies the clients cert:
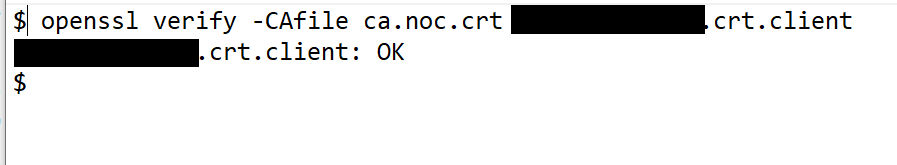
and yes, the ca is the issuer of the client cert. I already mentioned that I checked this with means of windows cert viewer. So to mee it all looks good - only thing missing is this one flag on the CA cert......
-
So the cert they created, just isn't marked as CA, but it was used to sign the the cert.. That is on the creator of the certs to fix.. Your just doing selfsigned..
As to a work around - I do not know how to import a cert into the cert manager as a CA, when it has not been marked as a CA
When they are creating the cert they are going to use as their CA, they need to set
basicConstraints=CA:true