Zoom Alert! (Network Trojan Detected)
-
Hello,
i have seen on my pfsense logs an alert/blocked traffic generated from an ip address that belong to "zoom".
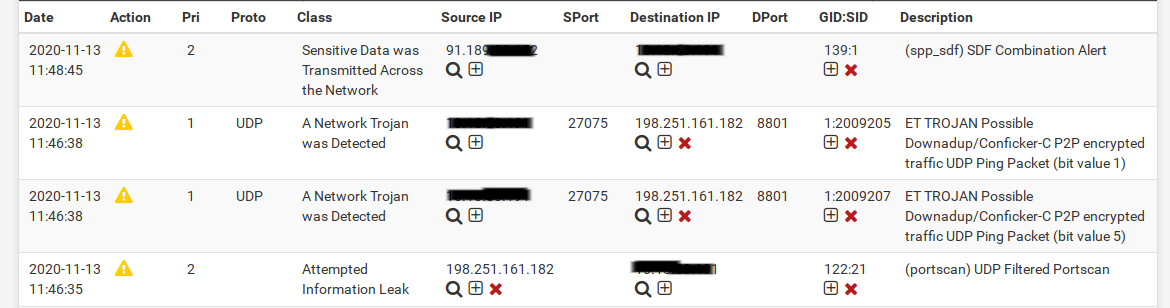
198.251.161.182
(portscan) UDP Filtered Portscan -- 2020-11-13 11:46:35
ET TROJAN Possible Downadup/Conficker-C P2P encrypted traffic UDP Ping Packet (bit value 5) -- 2020-11-13 11:46:38
ET TROJAN Possible Downadup/Conficker-C P2P encrypted traffic UDP Ping Packet (bit value 1) -- 2020-11-13 11:46:38Has anybody seen this alert from "zoom" before?
IPS Policy Selection is set to "Security".
-
@rimaju
First off, you have to find out what device is sending that. Use the IP address or MAC to determine that.
BTW, are you hiding NAT addresses? If so, that won't accomplish much.
-
Well that is a zoom owned IP, 198.251.128.0/17
And that is a zoom port, per listing on their website..
So pretty much 100% chance its false positive.. Which is very common with such alerts..
-
@JKnott
The device is identified and the traffic is blocked. The image is from WAN interface. LAN is on NAT, naturally.
I was wondered that zoom generate such traffic. -
@johnpoz
I read this article and made myself alert.
https://blog.snort.org/2019/07/snort-rule-update-for-july-16-2019.html. -
And are you on a mac? Do you have those ports forwarded to your PC that this webserver listened on? Why would you have any ports open?
Also zoom removed that webserver they installed back in july of 2019. Is your zoom software that far out of date?
-
@rimaju Perhap's you should read also this article also-
https://doc.emergingthreats.net/bin/view/Main/2009205Notice the Date
-
I'm on ubuntu 20.04 LTS.
I have no port forwards.
Zoom was on ubuntu 20.04 LTS installed.On my sort WAN interface i have included/activated about "11 Conficker" rules.
1 2009200 tcp $EXTERNAL_NET any $HOME_NET 445 ET TROJAN Conficker.a Shellcode
1 2009201 tcp $EXTERNAL_NET any $HOME_NET 445 ET TROJAN Conficker.b Shellcode
1 2009206 udp $HOME_NET [!1720,!1722,!2427,!5060,1024:] $EXTERNAL_NET [!1720,!1722,!2427,!5060,1024:] ET TROJAN Possible Downadup/Conficker-C P2P encrypted traffic UDP Ping Packet (bit value 4)
1 2009207 udp $HOME_NET [!1720,!1722,!2427,!5060,1024:] $EXTERNAL_NET [!1720,!1722,!2427,!5060,1024:] ET TROJAN Possible Downadup/Conficker-C P2P encrypted traffic UDP Ping Packet (bit value 5)
1 2009208 udp $HOME_NET [!1720,!1722,!2427,!5060,1024:] $EXTERNAL_NET [!1720,!1722,!2427,!5060,1024:] ET TROJAN Possible Downadup/Conficker-C P2P encrypted traffic UDP Ping Packet (bit value 16)
1 2008739 tcp $HOME_NET any $EXTERNAL_NET $HTTP_PORTS ET TROJAN Conficker/MS08-067 Worm Traffic Outbound
1 2009205 udp $HOME_NET [!1720,!1722,!2222,!2427,!5060,1024:] $EXTERNAL_NET [!1720,!1722,!2427,!5060,1024:] ET TROJAN Possible Downadup/Conficker-C P2P encrypted traffic UDP Ping Packet (bit value 1)
1 2009024 tcp $HOME_NET any $EXTERNAL_NET $HTTP_PORTS ET TROJAN Downadup/Conficker A or B Worm reporting
1 2008737 tcp $HOME_NET any $EXTERNAL_NET $HTTP_PORTS ET TROJAN Conficker/KernelBot/MS08-067 related Trojan Checkin
1 2009114 tcp $HOME_NET any $EXTERNAL_NET $HTTP_PORTS ET TROJAN Downadup/Conficker A Worm reporting
1 2008738 tcp $HOME_NET any $EXTERNAL_NET $HTTP_PORTS ET TROJAN Suspicious Accept-Language HTTP Header zh-cn likely Kernelbot/Conficker Trojan RelatedWith those rules applied, i found a lot of alerts. Not only from Zoom ip's.
-
You honestly think that Conflicker infected your ubuntu machine?
You really should not run an IPS unless you understand that its going to be a TON of noise and false positives.. And you disable the ones that create false positives for your normal traffic flow..
Well you should investigate the traffic if your concerned.. That's why you run a IPS right..
-
No one seemed to answer your question, so I will, even if it is LATE.
Yes, I have seen this. Here is what I get when using my Synology RT6600ax with "Threat Prevention".
ET MALWARE Possible KEYPLUG/Downadup/Conficker-C P2P encrypted traffic UDP Ping Packet (bit value 1)
I also get (bit value 4) and (bit value 5) events.
This is traffic going from my wife's phone when doing SilverSneakers with zoom. The target IP is 147.124.99.62
which is Zoom Video Communications, Inc (ZVC). Destination port is 8801.So, the same thing you are seeing, but a slightly different IP for Zoom.
It isn't clear to me if the phone actually has something, or, more likely, the "Threat Prevention" is just seeing encrypted P2P using UDP and is assuming it is a trojan.
-
@mtiede the phone has something? It’s an obvious false alert.
-
It's obvious until it isn't. I was just trying to do for him what I was hoping for. That someone else could CONFIRM the same thing was happening with a different environment. That makes it more obvious for me.
-
@mtiede I understand but without looking at the payload of a packet you can deduce based on IP reputation and ownership as well as Zoom documentation which tells you what ports are needed to work. Without a SIEM stack this is the best that can be done I would think.
-
@mtiede you understand this thread is over 2 year old??
Blatantly obvious 2 years ago this was a false positive..
-
Yes, I knew it was 2 years old. But since no one answered the question, I thought I would, for the record. His question was, "Has anybody seen this alert from "zoom" before?" Which, in fact, was the question I was trying to answer by searching and finding his post. Yep, both denis__ju and I have seen that alert with zoom. Which is somewhat reassuring that it is a normal thing for zoom to cause this alert.
And how do you know that in 2 years some hacker hasn't figured out a way to spread conficker via Android phones? And that hack just happened to get reported when it tried to infect the zoom server?
To help someone else, here are the IP addresses and ports used by zoom: https://support.zoom.us/hc/en-us/articles/201362683
-
@mtiede said in Zoom Alert! (Network Trojan Detected):
And that hack just happened to get reported when it tired to infect the zoom server?
Common Sense ;) Yeah 2 years ago android phones were spreading conflicker talking to zoom IPs.. And that port would be a download of the payload etc, not trying to infect it.. So yeah his the zoom server was being used to spread conflicker - and his android phone was infected..
Or I don't know common sense says he uses zoom, and the IPS reported a false positive based on traffic type and port -- anyone that has ever used IPS or IDS for more than 10 minutes knows that is quite common... So yeah common sense..