Strongvpn connects but firewall blocking incoming traffic
-
I had a openvpn client setup with IBVPN which was recently bought out by StrongVPN. My IbVPN client was working properly but I had to setup a new client for connecting to StrongVPN and deleted by IbVPN client. I used the guide on the StrongVPN site:
https://support.strongvpn.com/hc/en-us/articles/360038592794-pfSense-OpenVPN-Setup-Tutorial#STAT
I can sucessfully connect and the strongvpn server but I cannot browse from any device on my LAN. In checking firewall logs, it appears outgoing requests to websites are passed by the firewall but incoming traffic from those requests are denied? The setup per the tutorial leads to the same setup I had with IbVPN but for some reason not working now.
Any guidance would be appreciated. I've been pulling my hair out on this one.
-
@silverh22a
That tutorial is flat wrong,at least the outbound NAT section.Basically there is no reason to switch to manual mode, hybrid will do it right as well and pfSense can still generate rules automatically.
Next point, I suggest to not edit the WAN rules, but add the same for the VPN interfaces. In manual mode you can simply copy the WAN rules and edit the copies.
So you can still go out to your WAN if the VPN is not connected.And the primary problem is, you also need a rule for the common traffic (destination port any) on the VPN interface.
-
I switched to hybrid for outbound NAT and added rules on the VPN interface as suggested but still not working. Here are the settings. Any suggestions?
The other OpenVPN interface is for the pfsense OpenVPN server which works fine.
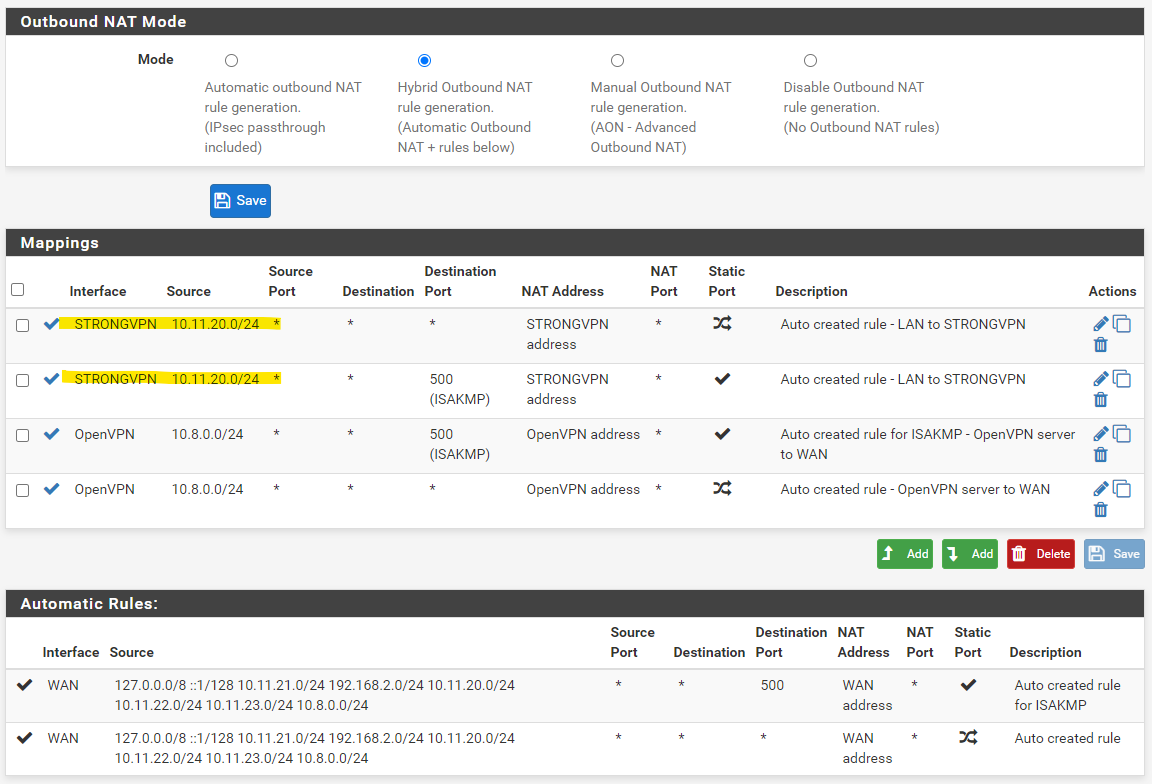
I have an Alias for all the devices I want routed through the VPN
-
-
As your automatic generated outbound NAT rules are showing, you have multiple internal subnets, but your VPN rule covers only one. Is that LAN and that one you have tested? So maybe its ok.
-
Try to access an internet host by its IP to exclude possible DNS issues.
Your rule directs the whole traffic from the alias group to the VPN, so they cannot use pfSense for DNS resolution anymore as long as there is no other (floating) rule allowing it. -
No idea, what you need the outbound NAT rule on "OpenVPN" for.
-
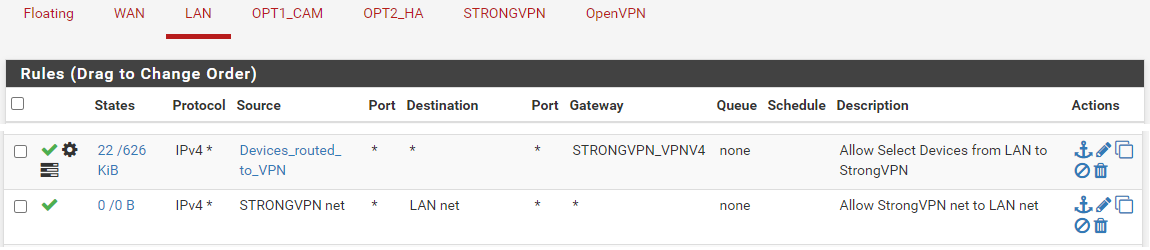
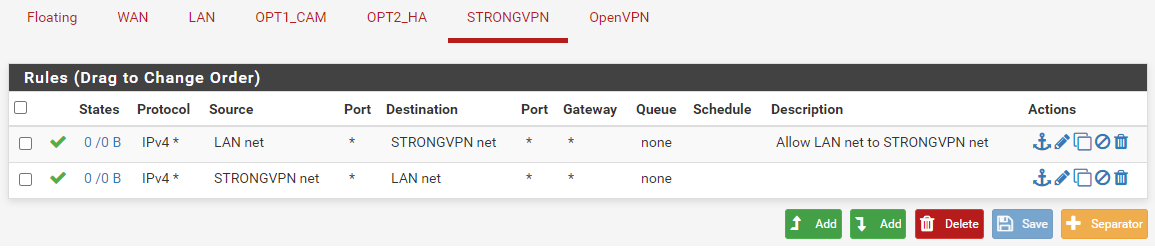
The "STRONGVPN net" rule on LAN is gratuitous, since there will be no packet entering the LAN interface from that source.
The same is true for the "LAN net" rule on the STRONGVPN interface. -
Do you really want to allow traffic from the STRONGVPN to your LAN subnet?
-
-
@viragomann said in Strongvpn connects but firewall blocking incoming traffic:
- As your automatic generated outbound NAT rules are showing, you have multiple internal subnets, but your VPN rule covers only one. Is that LAN and that one you have tested? So maybe its ok.
Only LAN needs access to the VPN
- Try to access an internet host by its IP to exclude possible DNS issues.
Your rule directs the whole traffic from the alias group to the VPN, so they cannot use pfSense for DNS resolution anymore as long as there is no other (floating) rule allowing it.
If ping a public hostname when connected to the VPN it resolves to a public IP so I assume DNS is working but the request times out
- No idea, what you need the outbound NAT rule on "OpenVPN" for.
OpenVPN is my pfsense OpenVPN server
- The "STRONGVPN net" rule on LAN is gratuitous, since there will be no packet entering the LAN interface from that source.
The same is true for the "LAN net" rule on the STRONGVPN interface.
I didn't have that originally but only tried it for troubleshooting to see if it would make a difference
- Do you really want to allow traffic from the STRONGVPN to your LAN subnet?
I don't plan on having this rule but was trying it for troubleshooting. I have disabled the Allow StrongVPN to LAN subnet rule under the LAN interface and the same rule under the StrongVPN interface.
Am I missing something in terms of rules?
-
You should know, which DNS your client is using. I pointed out the things caught my eye.
Do you have floating rules defined?
-
@viragomann Thanks for all your feedback so far, I appreciate it. Under the DNS server settings I specified a certain DNS server and the StrongVPN gateway for that server. Is that how I should do it?
I have no floating rules.
-
@silverh22a said in Strongvpn connects but firewall blocking incoming traffic:
@viragomann Thanks for all your feedback so far, I appreciate it. Under the DNS server settings I specified a certain DNS server and the StrongVPN gateway for that server.
This settings is only used in forwarder-mode, if using the DNS Forwarder or the Resolver if it's in forwarder-mode.
There are different other ways to handle the DNS for the VPN clients. Basically you may want to avoid DNS leaking.
- You can configure the clients to use an external DNS server. So with your firewall rule, DNS requests are directed over the VPN.
- Also possible to use the pfSense DNS Resolver for resolution and only enable the VPN interface for outgoing requests.
However, this applies to all DNS requests of the resolver.
So if you say, the DNS is working on the client and is not the issue here, do some troubleshooting with the Packet Capture tool from the Diagnostic menu.
Pick a public IP for access testing purposes via ping or http, enter this IP at Host Address, select the VPN interface, start the capture and try to access the address from the client.
If you don't see any packets, select the LAN interface and try again. -
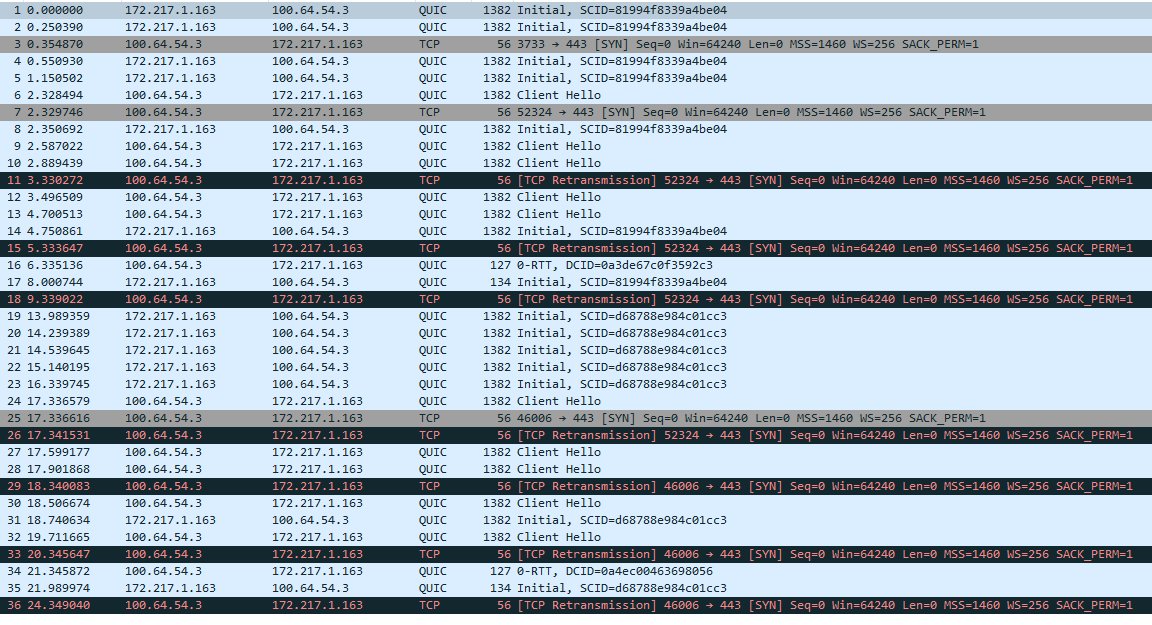
So I ran Packet Capture tool with the VPN interface selected, saved the file and loaded in Wireshark. I can see the VPN virtual IP as the source sending TCP packets to the destination Public IP but all the TCP packets are flagged as bad. I can also see some packets from the destination Public IP as the source sending to the VPN IP as the destination (not as many though). Since packets are being sent to the destination IP, does that mean firewall rules are okay, otherwise they would not be showing, is that correct?
When I ran the packet capture for the LAN interface with VPN client up it shows bad TCP packets as well.
-
@silverh22a
Without getting a view to the result and knowing details of your VPN connection it's hard to say, if the communition packets are correct.
Possibly there is an asymmetric routing somewhere, since packets are flagged as bad. You can enable logging and check if you get unexpected blocks.There should be no secrets in the capture result. So it will be save to post it here.
-
Here is packet capture. Could there be an issue with the actual VPN connection itself, perhaps an issue with the client configuration?
-
And what are your VPN connection details? Client-IP, Server-IP?
I expected to see your VPN tunnel is a private range, but I can't see any private IP here.
What is the IP you're trying to talk to? -
The client ip assigned from the StrongVPN OpenVPN server is 100.64.54.3. The public IP I was attempting to connect to is 172.217.1.163 (google). The first column of IP addresses in the log is the source and the second column is destination. You can see that there is some back and forth communication but none if it is sucessful. This is from logging the VPN interface. I'm not very experienced at reading these logs other than I know that black represents a bad transmission.
-
@silverh22a said in Strongvpn connects but firewall blocking incoming traffic:
The client ip assigned from the StrongVPN OpenVPN server is 100.64.54.3
That's a CGN space, strange. Never seen a VPN provider using CGN addresses for the tunnel.
The black marked are retransmissions. Looks to me as your client sends a QUIC packet and as he doesn't get an ACK it tries TCP.
Can you disable QUIC in the browser for testing? -
@viragomann said in Strongvpn connects but firewall blocking incoming traffic:
Can you disable QUIC in the browser for testing?
Here is a snip of the packet capture with QUIC in the browser disabled. Also I noticed under the diagnostics the Gateway log showed a sendto error 55 and Gateway status showed offline with 63% loss
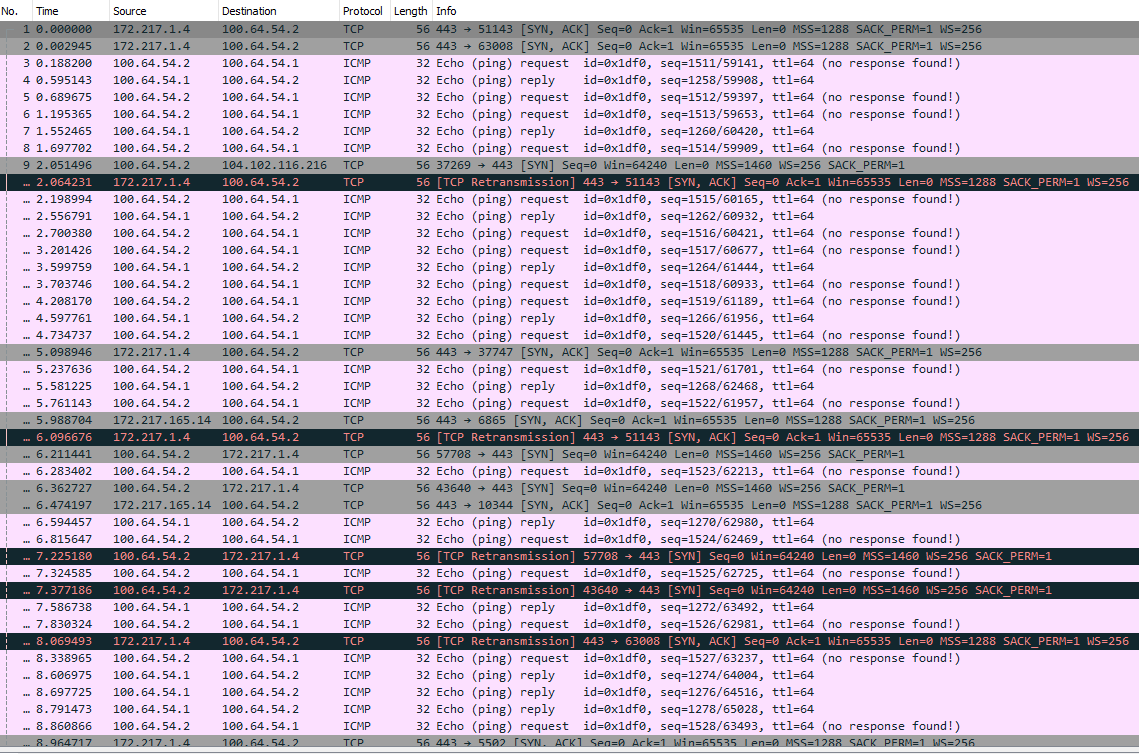
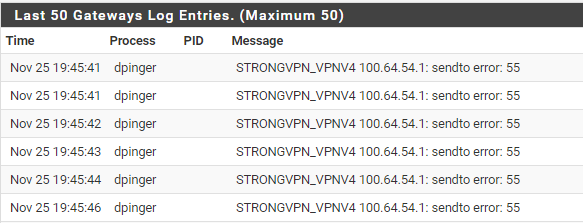
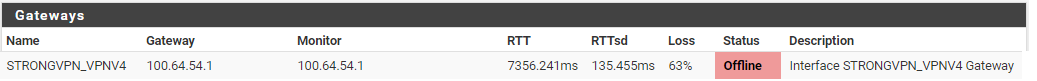
-
@silverh22a said in Strongvpn connects but firewall blocking incoming traffic:
Also I noticed under the diagnostics the Gateway log showed a sendto error 55 and Gateway status showed offline with 63% loss
So there will be another problem you should look for and rectify at first: https://docs.netgate.com/pfsense/en/latest/troubleshooting/gateway-errors.html#sendto-error-55
-
I haven't had any luck troubleshooting the gateway issue. I think it has something to do with the actual OpenVPN config parameters. Every request goes out the VPN interface but doesn't return. StrongVPN tech support has been no help, just advising me to follow the tutorial again.
I'm throwing in the towel on this one. I'm going change providers. It's too bad ibVPN was bought out by strongVPN. My setup worked well with ibVPN.
-
Just an update. I solved my issue. I switched vpn providers and its working. That tells me there was some nuance in the vpn config of strongvpn that didn't work.