Getting error on "data-ciphers" line on OVPN client
-
Hi all,
Trying to set up an OpenVPN connection on pfSense 2.4.5-RELEASE-p1. I am using the SSL-TLS+user auth method. I have a Apple Macbook with Tunnelblick 3.8.4 (build 5600), where I have imported the .ovpn config file generated from the pfSense OpenVPN client conf exporter plugin.
When I try connecting, it fails, with this error:
1606165530.305305 b000 Options error: Unrecognized option or missing or extra parameter(s) in /Library/Application Support/Tunnelblick/Users/will/pcol-gw-wdennis.tblk/Contents/Resources/config.ovpn:4: data-ciphers (2.4.9)I have set the NCP Algorithms on the pSense server to include all of the AES-* algo's. The
data-ciphers*lines in the client config are:data-ciphers AES-128-CFB1:AES-128-CFB8:AES-128-OFB:AES-192-CBC:AES-192-CFB:AES-192-CFB1:AES-192-CFB8:AES-192-OFB:AES-256-CBC:AES-256-CFB:AES-256-CFB1:AES-256-CFB8:AES-256-OFB data-ciphers-fallback AES-128-CBCThanks for any help or info you can provide.
-
I found that the latest OpenVPN client exporter updates generates OpenVPN 2.5 configs even on pfSense 2.4.5-p1 and when the OpenVPN server is still version 2.4x
I had to check don't include 2.5 config options
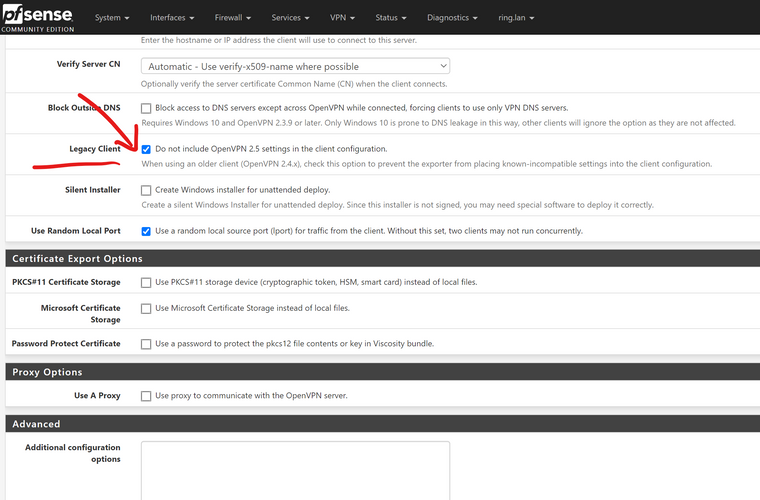
-
You shouldn't blindly include all the AES algorithms. Stick to the GCM and CBCs. Most likely explanation is that your client platform doesn't support one or more of the ciphers.
The client export generates OpenVPN 2.5 configs because it exports OpenVPN 2.5 installers, so that's probably OK (provided your client platform is running OpenVPN 2.5...)
Your log message does say your client is OpenVPN 2.4.9, though, so you probably do need to update the client to one that uses OpenVPN 2.5.0 or tick the Legacy box and export again.
-
yea, the error message said,
... config.ovpn:4: data-ciphers (2.4.9)so I assumed his client was 2.4.9 and not 2.5, but yea, that is a lot of ciphers as well to enable... yea, easiest just to stick GCM/CBC like @jimp said
-
Thanks for the help, folks!
I upgraded Tunnelblick to 3.8.5beta01 (build 5610), which has OpenVPN 2.5 (also had to set "OpenVPN version" drop in Settings to "Latest", which is OpenVPN 2.5.0 w/ OpenSSL 1.1.1h)
Also edited my client config, it is now:
dev tun persist-tun persist-key data-ciphers AES-128-CBC:AES-192-CBC:AES-192-CFB:AES-192-OFB:AES-256-CBC:AES-256-CFB:AES-256-OFB data-ciphers-fallback AES-128-CBC auth SHA256 tls-client client resolv-retry infinite remote vpn-gw.mycompany.com 1194 udp4 verify-x509-name "vpn-gw.mycompany.com" name auth-user-pass remote-cert-tls serverNow I do get connected, but I do not have a route to the remote LAN, just one for the VPN network itself (local LAN is 192.168.100.0/24, OVPN network is 192.168.5.0/24, and remote LAN is 192.168.10.0/24):
mymac:~ me$ netstat -nr -f inet | grep -v -e I -e "/32" Routing tables Destination Gateway Flags Netif Expire default 192.168.100.1 UGSc en0 127 127.0.0.1 UCS lo0 127.0.0.1 127.0.0.1 UH lo0 169.254 link#4 UCS en0 ! 192.168.5 192.168.5.2 UGSc utun6 192.168.5.2 192.168.5.2 UH utun6 192.168.100 link#4 UCS en0 ! 224.0.0/4 link#4 UmCS en0 !The end of the Tunnelblick log has:
13:05:17 *Tunnelblick: Start of output from client.up.tunnelblick.sh WARNING: $route_vpn_gateway is empty 13:05:19 *Tunnelblick: NOTE: No network configuration changes need to be made. 13:05:19 *Tunnelblick: WARNING: Will NOT monitor for other network configuration changes. 13:05:19 *Tunnelblick: WARNING: Will NOT disable IPv6 settings. 13:05:19 *Tunnelblick: DNS servers '192.168.100.1' will be used for DNS queries when the VPN is active 13:05:19 *Tunnelblick: NOTE: The DNS servers do not include any free public DNS servers known to Tunnelblick. This may cause DNS queries to fail or be intercepted or falsified even if they are directed through the VPN. Specify only known public DNS servers or DNS servers located on the VPN network to avoid such problems. 13:05:19 *Tunnelblick: Flushed the DNS cache via dscacheutil 13:05:19 *Tunnelblick: /usr/sbin/discoveryutil not present. Not flushing the DNS cache via discoveryutil 13:05:19 *Tunnelblick: Notified mDNSResponder that the DNS cache was flushed 13:05:19 *Tunnelblick: Notified mDNSResponderHelper that the DNS cache was flushed 13:05:19 *Tunnelblick: End of output from client.up.tunnelblick.sh 13:05:19 *Tunnelblick: ********************************************** 2020-11-24 13:05:19.792773 Initialization Sequence Completed 2020-11-24 13:05:19.792939 MANAGEMENT: >STATE:1606241119,CONNECTED,SUCCESS,192.168.5.2,71.xxx.xxx.xxx,1194,, 2020-11-24 13:05:21.018480 *Tunnelblick: Routing info stdout: route to: 192.168.100.1 destination: 192.168.100.1 interface: en0 flags: <UP,HOST,DONE,LLINFO,WASCLONED,IFSCOPE,IFREF,ROUTER> recvpipe sendpipe ssthresh rtt,msec rttvar hopcount mtu expire 0 0 0 0 0 0 1500 1116 stderr: 2020-11-24 13:05:21.018824 *Tunnelblick: Warning: DNS server address 192.168.100.1 is not a public IP address and is not being routed through the VPN. 2020-11-24 13:05:26.193775 *Tunnelblick: This computer's apparent public IP address (71.zzz.zzz.zzz) was unchanged after the connection was madeSo it seems I may be missing some needed entries yet on the pfSense (server) side? I made the OVPN config on pfSense via the wizard.
-
I know its 20 min long these days, but worth a watch and goes over all this settings, including routing to your local network: https://www.youtube.com/watch?v=PgielyUFGeQ
Are you probably missing server settings for
IPv4 Local network(s)andIPv6 Local network(s) -
I'm having this problem even with the 2.5.0 client on windows.
2021-05-12 08:13:40 OpenVPN 2.5.0 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Oct 28 2020 .... 2021-05-12 08:13:54 OPTIONS ERROR: failed to negotiate cipher with server. Add the server's cipher ('AES-128-CBC') to --data-ciphers (currently 'AES-128-GCM') if you want to connect to this server.the generated ovpn file has
data-ciphers AES-128-GCM data-ciphers-fallback AES-128-CBCif I mark the "legacy client" option it changes to
cipher AES-128-CBCand the client can connect.
It seems the client is ignoring the data-ciphers-fallback option. -
Command line pfSense :
openvpn --helpThe first line tells you that the latest pfSense (2.5.1) is using
OpenVPN 2.5.1 amd64-portbld-freebsd12.2 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Apr 5 2021I only export settings from pfSense, not the 'executable Windows OpenVPON Installer package', I download the latest OpebVPN client from OpenVPN (it's also open source).
Get it from here : https://openvpn.net/community-downloads/
Like pfSense, don't stay on "2.5.0". OpenVPN had issues to, so they went to 2.5.1 to stabilised, for now, on 2.5.2.
The 2.5.2 client works fine with the OpenVPN server 2.5.1 on pfSense.Btw : It's just pure coincidence that OpenVPN uses nearly identical version numbers as the CE version of pfSense.
-
@gertjan thank you, but for me and my users the all in one installer is more convenient. I didn't know that openvpn 2.5.0 had issues.
-
@gertjan said in Getting error on "data-ciphers" line on OVPN client:
Get it from here : https://openvpn.net/community-downloads/
I just tried with the 2.5.2 openvpn client and it has the same problem:
Wed May 12 10:14:28 2021 OpenVPN 2.5.2 i686-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Apr 21 2021 .... Wed May 12 10:16:22 2021 OPTIONS ERROR: failed to negotiate cipher with server. Add the server's cipher ('AES-128-CBC') to --data-ciphers (currently 'AES-128-GCM') if you want to connect to this server. -
maybe it's because I'm still with pfSense 2.4.5p1 that has openvpn 2.4.9 (I cannot upgrade to 2.5.1 due to its problems with NAT and multi WAN)
-
@olivluca said in Getting error on "data-ciphers" line on OVPN client:
openvpn 2.5.0 had issues.
As pfSEnse, they have a FAQ, manual, forum etc.
Yes, they have issues - like any other huge (OpenVPN is huge ....) (software) product.The shift from 2.4.x to 2.5.x has special help pages, with all the details about these changes.
If you use OpenVPN, don't hesistate. Bookmark this one - and use it.
-
@gertjan said in Getting error on "data-ciphers" line on OVPN client:
Yes, they have issues - like any other huge (OpenVPN is huge ....) (software) product.
Sure, but I didn't mean it like that, I was referring to the interaction with the "client export" generated settings. Anyway, the latest release of openvpn has the same problem.