Routing between Networks behind different WAN IPs
-
Hi all,
I have the following setup:
WAN connection 1: public IP from Subnet A
WAN connection 2: public IP from Subnet B
LAN1: going out through WAN 1
LAN2: going out through WAN 2@WAN1 is a NAT Rule forwarding a certain port to a machine in LAN1.
If I use this connection @WAN1 from wherever in the internet it works.
When I try to connect to this connection @WAN1 from LAN2 it does not work.I did take captures @LAN2, @WAN2 and @WAN1 interfaces. I do see the traffic @LAN2 but neither @WAN2 nor @WAN1. So it seems to me that the pfSense blocks this traffic somehow.
I do not see anything blocked in FW logs.
I did check the rules: LAN2 allows any traffic from LAN2 to any destination.
I do not want to allow traffic from LAN2 to LAN1 directly.
Does anyone know what I am doing wrong?
thanks and best regards
Dabbelju -
What are your LAN subnets?
-
LAN1: 10.203.112.0/23
LAN2: 192.168.32.0/24 -
Have you set up a route to get to the other network? If pfsense on LAN2 doesn't know about LAN1, it can't route to it. Also, I assume you're using a public address and NAT. Of course, this will limit you to a single address at the other end. Is that what you want? Perhaps a VPN might be a better solution.
-
@JKnott said in Routing between Networks behind different WAN IPs:
If pfsense on LAN2 doesn't know about LAN1, it can't route to it.
Both are connected to a single pfSense, so why it shouldn't know?
@dabbelju007 said in Routing between Networks behind different WAN IPs:
@WAN1 is a NAT Rule forwarding a certain port to a machine in LAN1.
When I try to connect to this connection @WAN1 from LAN2 it does not work.So you try to access WAN1 address from LAN2?
You may have to enable NAT reflection (pure NAT) in the NAT rule or if you are accessing the server by hostname, you can set a host override in DNS.Appart from this you have to allow the access by a firewall rule on LAN2.
-
@viragomann said in Routing between Networks behind different WAN IPs:
Both are connected to a single pfSense, so why it shouldn't know?
There was nothing in the original post to indicate that. On the other hand, he mentions traffic through the WANs. If it was all in one pfsense, why would he say that?
-
@JKnott
I'd assume that. True, it's not clearly described. -
Sorry for being not clear in my description. Everything described is connected to one pfSense. I did try to draw it down.
The green way is working. the red way is not.
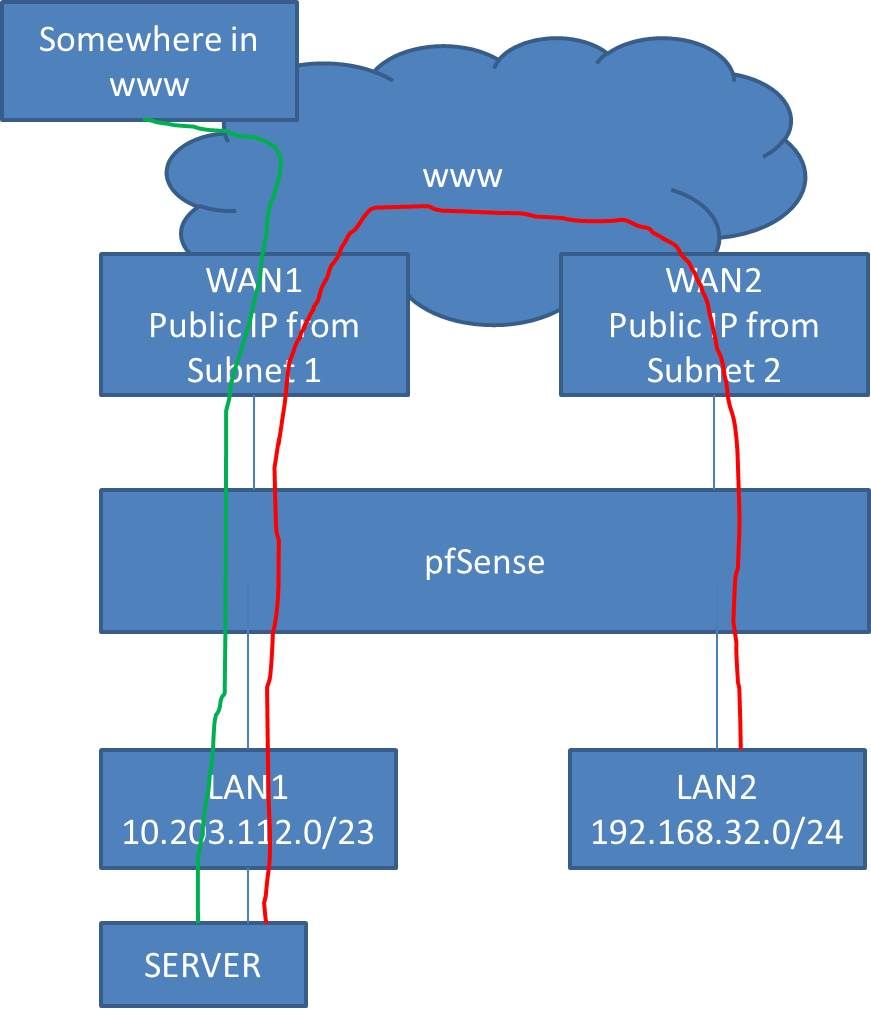
-
@dabbelju007
I assumed that as mentioned above.So either add a DNS host override, when using a hostname to access the server or enable NAT reflection.
-
If you policy route, ie send traffic from lan2 out wan2.. There has to be a rule above that in lan2 rules that allows it to get to lan1..
Its all in the multwan doc
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.htmlSee the Bypassing Policy Routing section.
The red way is not how you would do it.. this is the way it would be done.
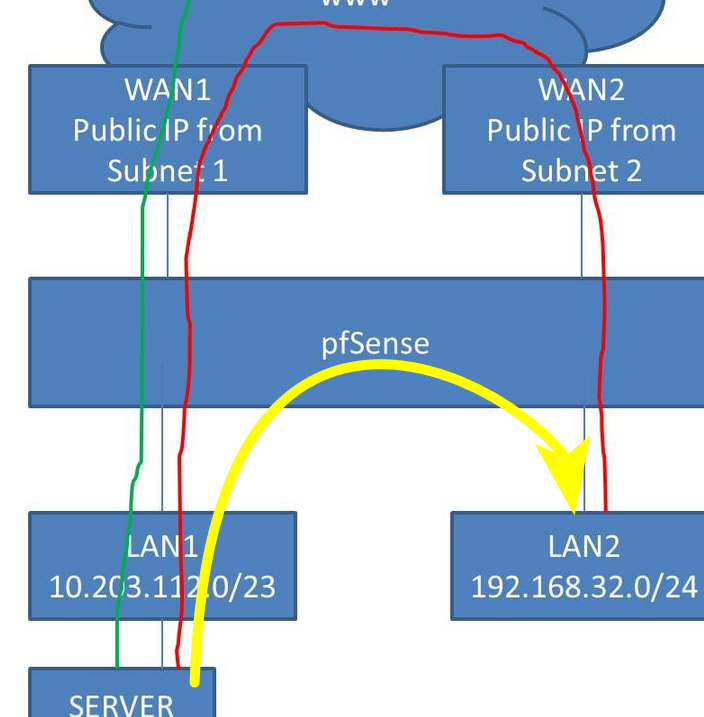
-
@viragomann Thanks for your advice.
Just for a test: Rule at LAN2 allows IPv4 any protocol to any destination. I am using IPv4 addresses.
The NAT Port Forward Rule @WAN1 Interface has NAT refelction enabled, as you said pure NAT.
It is still not working.
I know the Firewall Log, State Log and packet capture. Is there a way in pfSense to see in which steps this reuqest is handeled?
When I do the request and take a look into the firewall log I can see that there is an entry which "allows the request" out from LAN2. There is no entry for the NAT rule @WAN1 (logging in the rules is enabled).
What do I do wrong?
Thanks
Dabbelju -
@dabbelju007
Are you able to access the server by its internal IP?You can sniff the packets on LAN1 using Diagnotic > Packet Capture.
When trying to access from LAN2 you should see the packets here else well as the responds from the server. -
@viragomann
I have access to the server. If I take captures at all four interfaces (LAN2, WAN2, WAN1, LAN1) I do only see the request leaving LAN2 and nothing at the other captures. -
@dabbelju007 said in Routing between Networks behind different WAN IPs:
I do not want to allow traffic from LAN2 to LAN1 directly.
Why?? For what possible reason would you not just let lan2 talk to lan1 via your rule? Sending traffic out wan2 just to come in wan 1 gets you nothing other than non optimal traffic flow.
-
So you can access the server by its IP, but not via the WAN address.
@dabbelju007 said in Routing between Networks behind different WAN IPs:
If I take captures at all four interfaces (LAN2, WAN2, WAN1, LAN1) I do only see the request leaving LAN2 and nothing at the other captures.
As @johnpoz illustrated, the connection doesn't pass the WANs, so you cannot see the packets there.
On LAN2 you only see request packets to WAN1 and nothing else?
So the NAT reflection is probably not working.Do you use a hostname for accessing from outside. If, you can add a host override.
-
Thats whats I will do. I thought it must be possible the other way even if I produce unnecessary traffic.
But how can I use the public IP of WAN1 from LAN2 even if I route it directly? Would that be makeable by another NAT rule?
Background to my question is that I have users using the service from home. Sometimes they come into our office and are connected to LAN2 and want to use the same service.
Ok, if I would use DNS names I would know a way. But is it possible by using the public IP and a NAT Rule?
-
@dabbelju007 said in Routing between Networks behind different WAN IPs:
Would that be makeable by another NAT rule?
That's what NAT reflection should do for you automatically. It implies an invisible NAT rule.
But yeah, you may as well add a NAT rule manuelly to LAN2 if you want that.
source: WAN1 address
dest: server -
Local dns resolution is the whole point of split dns. When the is on some other network they would use the public IP and access via your port forward.
When they are on the site where the server is - the dns on the site would point the them to the local IP.
Where you run into a problem is if the client is not using your dns when they come to your site. And only resolve the public IP. This is where nat reflection would come into play. But the use of dual wan would complicate the use of nat reflection most likely. This should only be an issue if they were hard coding their dns vs using dhcp to get their dns, or they were using doh in their browsers, etc.
You could do maybe just a redirection on your lan 2 interface - if traffic hits lan 2 going to your wan 1 public 1.2.3.4 on port X, you just port forward that to server IP..
-
I would probably just use NAT reflection here if the requirement is only occasional.
https://docs.netgate.com/pfsense/en/latest/recipes/port-forwards-from-local-networks.html#method-1-nat-reflection
Adding a bunch of custom rules is only going to cause you more maintenance time at some point in the future.
Steve
-
However, due to the Multi-WAN setup, maybe you need the NAT reflection with proxy mode.