pfblockerNG and HomeKit
-
Hi guys,
I am the owner of a new SG-2100 and I have this installed at home for around two months. I am really new to pfsense and also to pfblockerNG but I work as a network engineer and have a lot of experience in other products/manufacturers.
I open this thread to try to clarify how to correctly "whitelist" multicast addresses from PfBlockerNG.
I am using Firehol list that include private addresses and I have read a lot of posts where BBcan177 is asking you not to do that for "outbound traffic" :) So I used the suppression part of PfBlockerNG to allow traffic between my private interfaces.
I am using a multi-vlan setup where I have 5 different VLANs for this purposes:
- Management
- LAN Home
- IoT Network
- Guests
- Servers Network
So I am using 192.168.10/24, 20, 30, and so on. I used the suppression part of the PfBlockerNG and configured the alias as follows:
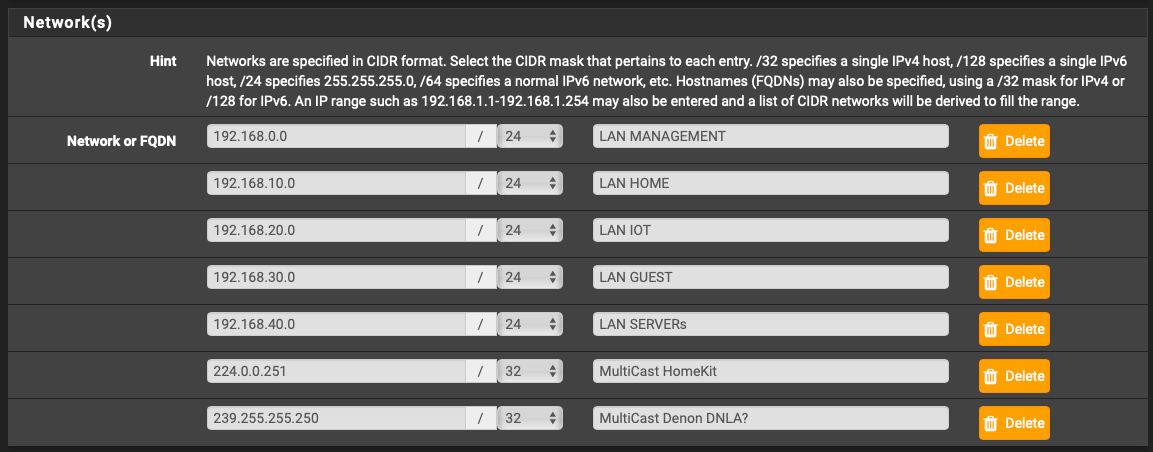
Since I did that, all the traffic between VLAN's started working again and "by-passing" the FireHol blacklist, but the 224.0.0.251 it's still not working and it is still matching against the 224.0.0.0/3 listed at FireHol. So I continue having "Alerts" at the PfBlockerNG alerts section for that IP address matching against Firehol. Before applying the suppression, I had alerts for all the private addresses, but now just the multicast ones.
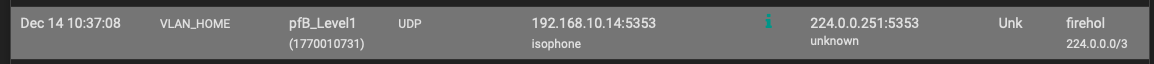
My main concern is if I disable FireHol in "outbound" direction, if this could be a potential problem because I will permit traffic to a bunch of public ip addresses from the inside.
I also don't want to allow the "full" 224.0.0.0/3 in a whitelist because there are tons of IP addresses reserved for multicast and in reality I only need this 224.0.0.251 and maybe another IP address used by my denon av receiver for ¿DLNA?
Is it something why the multicast address is not working? Is it maybe not possible to set an slash 32 to a multicast address? or is it something that the pfsense is not parsing correctly?
And another question, with this suppression enabled, am I permitting traffic from "every" interface to my private addresses? I know that I would have to configure a NAT and publish a service to "allow" traffic from the outside into the private addresses but I don't know really if this suppression alias is working in "any" direction.
Thank you!
BR!
-
I’ve got all my IOT stuff on an IOT vlan that can only access the internet all the homekit stuff is available from the other subnets due to having an Apple TV.
My IOT kit thinks i’m away from home and just works.
No need to touch pfBlocker.
-
This post is deleted! -
@nogbadthebad Thanks for your answer! Problem with that setup you propose is that all the traffic has to go through Apple servers and, based on the country you live, maybe this could be 300-500ms of delay, and this is not always the ideal situation :) I have several lights activated by motion sensors and this delay could end in you passing through a corridor, and the light turning on when you are no longer on this corridor :)
the process is explained in this web, I copy the text from there and quote the original source:
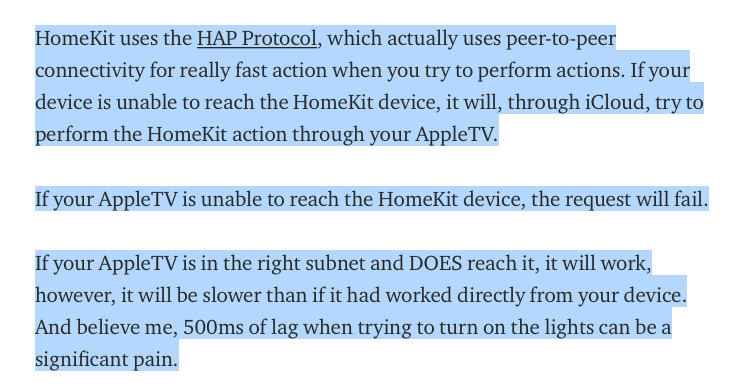
https://medium.com/@gepeto42/using-homekit-devices-across-vlans-and-subnets-aa5ae1024939
So yes, in my setup now everything is working, but I would love to permit multicast if possible :)
BR!
-
Create your own outbound firewall rules, allow what you want and place it above the pfblocker rules.
-
@nogbadthebad said in pfblockerNG and HomeKit:
Create your own outbound firewall rules, allow what you want and place it above the pfblocker rules.
Thanks! It is a way to go :) but I was asking why the suppression is working correctly with private addresses /24 ranges and not with the /32 multicast ones ¿? It is maybe unsupported to do that?
Also the other question was, if I add the suppression for all those ranges, what is happening in the background? Am I permitting traffic from the Internet to my private addresses? Obviously I would have to configure a NAT translation from my public IP address but I was wondering if I suppress all my LAN addresses and ranges, maybe if I open a service later in the future, if this could be a bad configuration because of this suppression, because maybe I am "opening" bad guys to my services while doing this.
Thank you! :)
BR!
-
So I have multiple subnets, as follows:
VLAN30 (10.27.200.0/24) - LAN (Servers, no DHCP)
VLAN202 (10.27.202.0/24) - IoT
VLAN204 (10.27.204.0/24) - DHCP (Clients, non-server devices)All my devices that are not servers connect to VLAN204, except my AppleTV and any IoT devices (including IP Cameras), these are on VLAN202.
I have an ANY* rule from VLAN30 and VLAN204 to all other VLANS. VLAN202 can only talk out of the WAN interface and are blocked from communicating with VLAN30, but can talk to VLAN204, with the exception of DHCP, DNS, and mDNS, those can talk to VLAN30. I have pfBlocker Outbound rules set for VLAN30, 202, and 204, and Inbound for WAN. I have no NAT to the IoT network. I also don't use this firhol, which is most likely a huge difference.
So, one thing is that since my iPhone, on VLAN204 can talk to my Phillips Hue on VLAN202, and vice versa, and I have mDNS reflection enabled, I think that is the key. The Homekit hub is only needed when the client device (iPhone) cannot directly talk to the IoT device, it then routes through iCloud.
I'm not sure where you are applying the alias to, I will try to duplicate you setup if possible and see if I break things (the wife would be happy for sure).