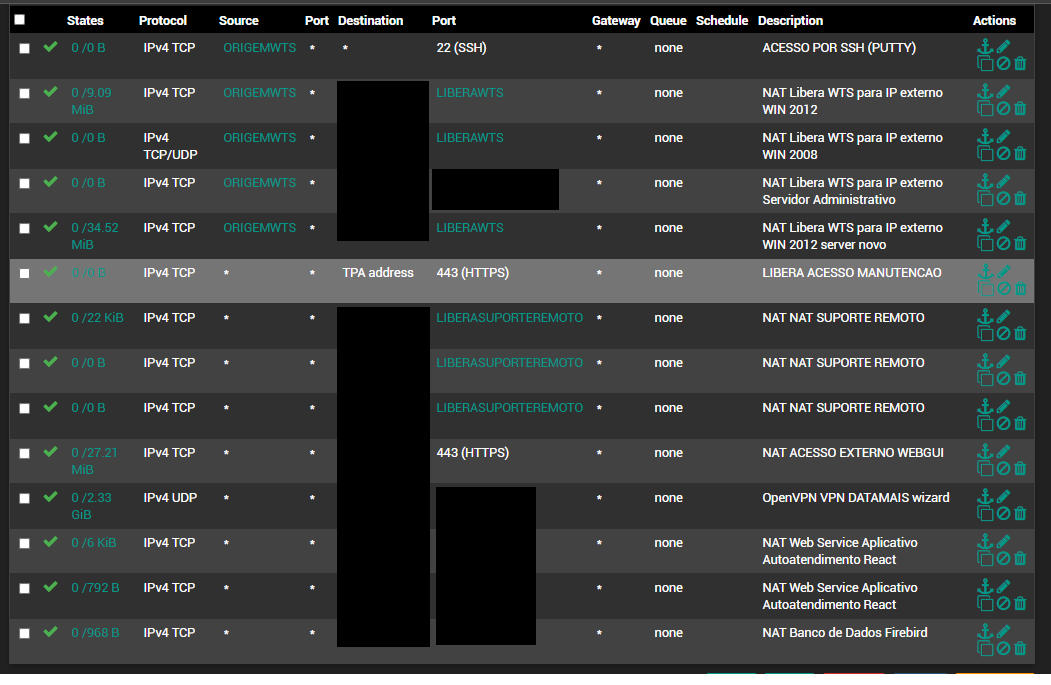
Firewall log - Attack warning
-
Hello.
Since last Friday the firewall log is showing an "attack warning".
The log shows many warning like this.
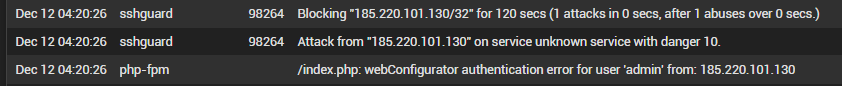
What the best pratice?
Downing the interface? Ignore? Change the passoword? All of those options?
-
Is 185.220.101.130 an address inside your network? If not I would start by not allowing access to SSH or HTTP/HTTPS on the WAN...
I think I've something similar to this when our network probe port scans the router's LAN IP.
-
@teamits said in Firewall log - Attack warning:
185.220.101.130
185.220.101.130 is not an address inside our network and it is not the only one trying to get access to our pfSense. Many different IP´s are trying too.
"not allowing access to SSH or HTTP/HTTPS on the WAN" how the best way to do this and what about my navigation?
-
@hugoeyng said in Firewall log - Attack warning:
"not allowing access to SSH or HTTP/HTTPS on the WAN"
All unsolicited inbound traffic to your wan is blocked out of the box. You must of created a rule to allow access to your webgui port and or ssh as well.
Remove said rules.. Post up your wan rules if you want advice on what is in there that shouldn't be.
The only thing in wan rules should be stuff you want to allow.. But yeah if you allow access to webgui or ssh to the public internet - its going to get hit, multiple times a day, if not per hour or even per minute.. The internet is a noisy and dangerous place to open up services too.
-
@johnpoz Thank you for your answer.
You are right. I allow access to webgui and SSH, but I limited the access only for known IP´s (contained into an alias).
I monitor the logs and this is the first time I saw so much trieds to log/access the firewall. Aparentelly they were trying to connect via SSH or the webgui (HTTPS).
They gave up yesterday. Or, maybe, they were successful yesterday :))
I am not sure.
-
If you were seeing such traffic from IPs that are not in your alias - then your rules are not setup like you think. Or your alias contains more IPs then you think?
-
@hugoeyng said in Firewall log - Attack warning:
You are right. I allow access to webgui and SSH, but I limited the access only for known IP´s (contained into an alias).
If you see that traffic, you didn't. Or your alias or rule is serioulsy borked!
@hugoeyng said in Firewall log - Attack warning:
They gave up yesterday. Or, maybe, they were successful yesterday :))
Then you'd see a successful logged in message. Otherwise 3-5 attempts and sshguard locks them out for a block-time (10m?).
-
The rules on the interface from where they attacked.
-
Not sure how anyone suppose to help you with most of that obfuscated
But this "could" for sure allow access - and has no alias for source.
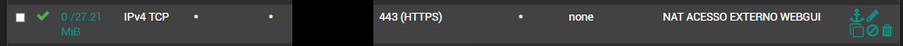
Depending on what the dest is set too?
-
@johnpoz that would not be SSH though...there must be something else or else the alias ORIGEMWTS is incorrect on the SSH rule. Also, not sure why that is marked as "NAT" unless that is a linked NAT firewall rule? NAT wouldn't be necessary for direct access to the WAN IP, though we've set up a different port to NAT to the router's LAN IP in cases where 443 was being NATted to a LAN server.
@hugoeyng Hover your mouse over the ORIGEMWTS alias and see what it is resolving to.
Also, the SSH firewall rule has 0 bytes of traffic so hasn't been used since it started counting.
-
Agreed that is not ssh, but his top ssh rule shows no hits..
But as I stated we are not seeing the whole picture here.. We have no idea what those bottom rules are - they are not using aliases, and they don't show what the port or dest IP are even. But they do have hits.