Problem updating Alias native hourly
-
Hello,
First of all, let me thank for this amaizing tool which is pfBLockerNG. It's not the only reason but for me is the most important one, to use pfSense.
I've been dealing with an issue with the auto Alias update from quite some time. Because I've added this new Alias Native after upgrading to version 3.0.0.X, I dont know if the problem was inserted with this version or if it existed before (or if it is a problem actually...)
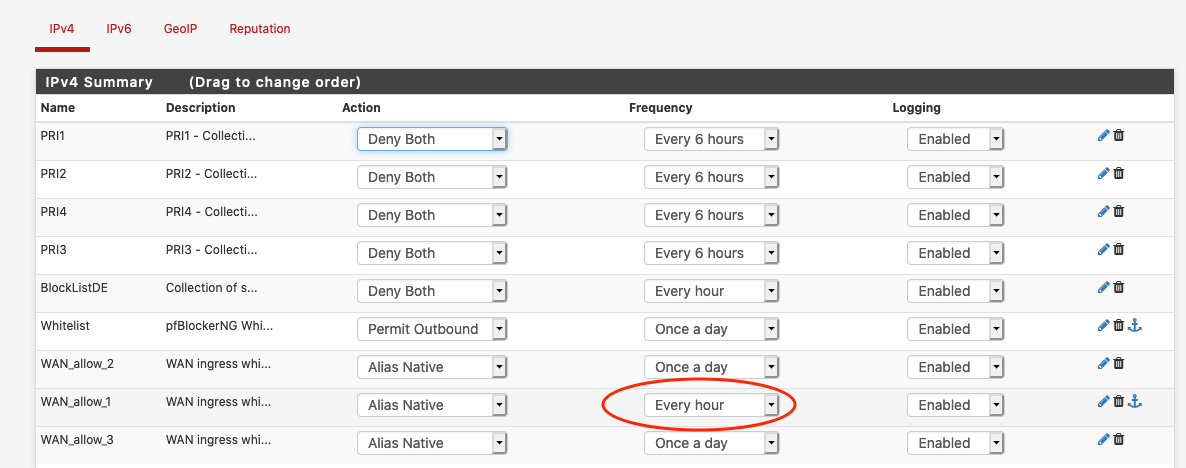
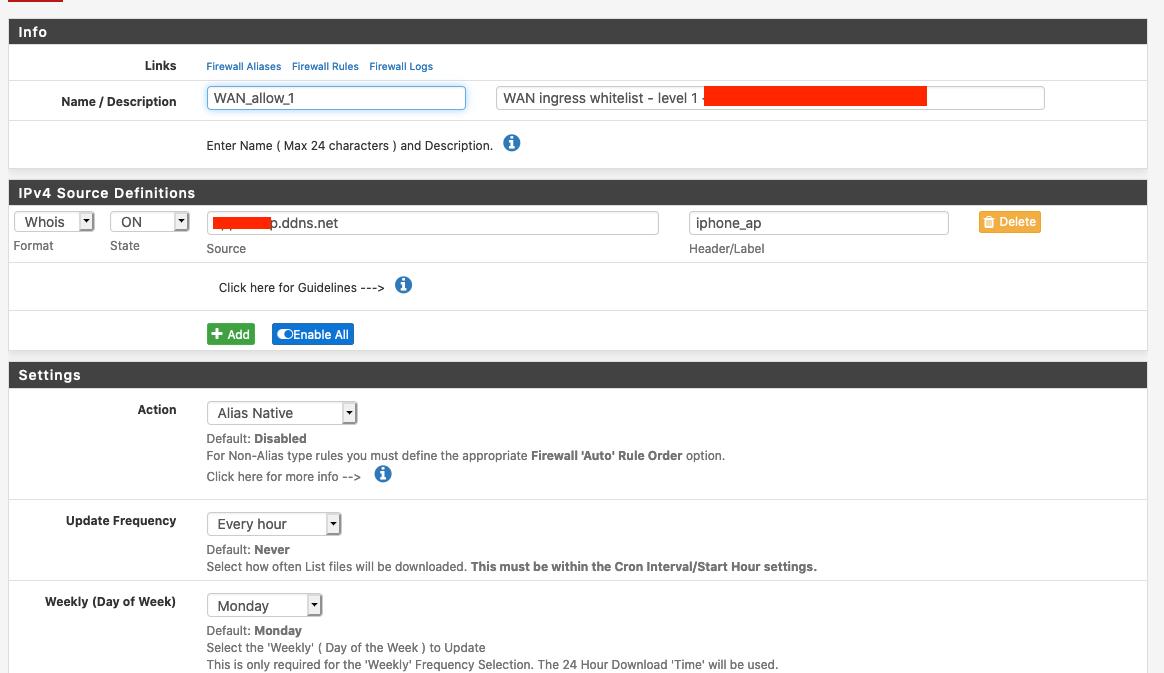
So I'm using an WAN ingress Alias Native firewall rule, that requires and hourly update, because the idea behind it is to allow my mobile phone IP to access some ports that need to be open, but I dont want to expose them to any other IP other than my phone (yes I do have OpenVPN setup, but this is different please try to understand it :) ).
The mobile IP address does not change that frequently (I was quite surprise to maintain the same IP address sometimes for more than 24h) but eventually it does change.So I've made a Native Alias, of whois type, so that a given domain (ddns) is converted in a IP address, and then with the respetive firewall allow rule, the phone has access to the services in my LAN.
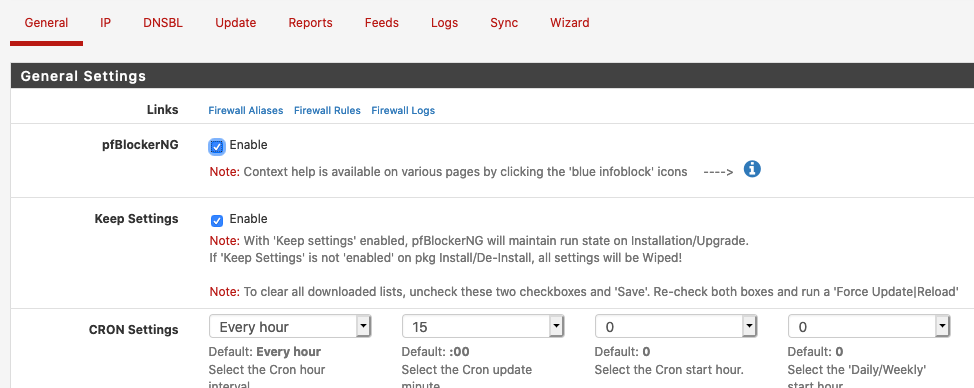
What i've detected is that when my phone IP changes, and of course, after updating the DNS (dynamic dns - theres an app that detects that the IP changes and does updates the domain), even though the CRON settins in general tab are set to Hourly updates, and the Alias it self are also set up to hourly refresh, the Alias does not get updated with the new IP address, even when more that 2 ou 3 hours has passed, but only when I force Reload the IP.
I'll try to show it in pictures, first my settings, that the Cron log:
General:
IP -> IPv4:
Alias details (pic 1):
Alias details (pic 2):
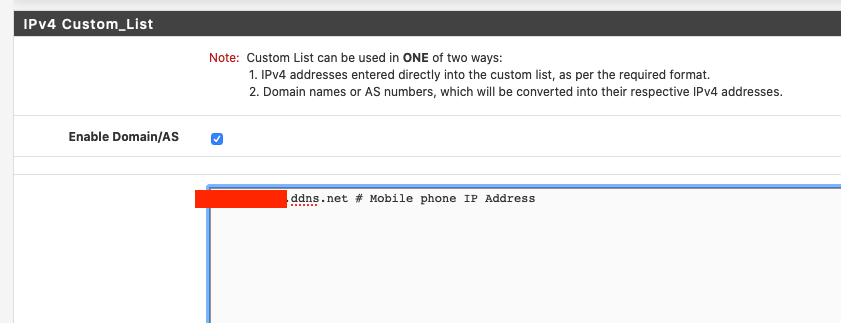
Alias on /var/db/pfblockerng/native:
Alias on /var/db/aliastables:
exert of the log:
===[ Aliastables / Rules ]========================================== No changes to Firewall rules, skipping Filter Reload Updating: pfB_PRI1_v4 794 addresses added.837 addresses deleted. Updating: pfB_PRI2_v4 1 addresses added. Updating: pfB_PRI4_v4 112 addresses added.2 addresses deleted. Updating: pfB_PRI3_v4 no changes. Updating: pfB_BlockListDE_v4 5 addresses added.10 addresses deleted. Updating: pfB_Whitelist_v4 no changes. Updating: pfB_WAN_allow_2_v4 no changes. Updating: pfB_WAN_allow_1_v4 no changes. Updating: pfB_WAN_allow_3_v4 no changes. ===[ Kill States ]================================================== Firewall state(s) validation for [ 87 ] IPv4 address(es)... No matching states found ====================================================================== ===[ FINAL Processing ]===================================== [ Original IP count ] [ 62451 ] [ Final IP Count ] [ 27227 ] ===[ Permit List IP Counts ]========================= 11 /var/db/pfblockerng/permit/Whitelist_custom_v4.txt ===[ Deny List IP Counts ]=========================== 27229 total 12226 /var/db/pfblockerng/deny/CINS_army_v4.txt 3700 /var/db/pfblockerng/deny/BBC_C2_v4.txt 2974 /var/db/pfblockerng/deny/ET_Comp_v4.txt 2337 /var/db/pfblockerng/deny/BlockListDE_Apache_v4.txt 1494 /var/db/pfblockerng/deny/Abuse_Feodo_C2_v4.txt 1099 /var/db/pfblockerng/deny/CCT_IP_v4.txt 986 /var/db/pfblockerng/deny/ET_Block_v4.txt 611 /var/db/pfblockerng/deny/ISC_1000_30_v4.txt 595 /var/db/pfblockerng/deny/Talos_BL_v4.txt 457 /var/db/pfblockerng/deny/BDS_Ban_v4.txt 342 /var/db/pfblockerng/deny/Alienvault_v4.txt 239 /var/db/pfblockerng/deny/MaxMind_BD_Proxy_v4.txt 74 /var/db/pfblockerng/deny/Abuse_SSLBL_v4.txt 65 /var/db/pfblockerng/deny/Spamhaus_eDrop_v4.txt 25 /var/db/pfblockerng/deny/HoneyPot_IPs_v4.txt 2 /var/db/pfblockerng/deny/ISC_Block_v4.txt 1 /var/db/pfblockerng/deny/Spamhaus_Drop_v4.txt 1 /var/db/pfblockerng/deny/MDL_v4.txt 1 /var/db/pfblockerng/deny/Abuse_IPBL_v4.txt ===[ Native List IP Counts ] =================================== 1022 total 988 /var/db/pfblockerng/native/PT_v4.txt 29 /var/db/pfblockerng/native/AS12353_Vdf_PT_v4.txt 1 /var/db/pfblockerng/native/iphone_ap_v4.txt 1 /var/db/pfblockerng/native/WAN_allow_1_custom_v4.txt 1 /var/db/pfblockerng/native/VPS_Ger_dns_v4.txt 1 /var/db/pfblockerng/native/VPS_Bel_dns_v4.txt 1 /var/db/pfblockerng/native/MEO_Belverde_v4.txt ====================[ Empty Lists w/127.1.7.7 ]================== Abuse_IPBL_v4.txt MDL_v4.txt Spamhaus_Drop_v4.txt ===[ DNSBL Domain/IP Counts ] =================================== 1445306 total 1125991 /var/db/pfblockerng/dnsbl/hosts_oisd_nl.txt 83837 /var/db/pfblockerng/dnsbl/Abuse_urlhaus.txt 83036 /var/db/pfblockerng/dnsbl/CoinBlocker_All.txt 38939 /var/db/pfblockerng/dnsbl/anudeepND.txt 33539 /var/db/pfblockerng/dnsbl/AntiSocial_BD.txt 18523 /var/db/pfblockerng/dnsbl/Cameleon.txt 16510 /var/db/pfblockerng/dnsbl/MDS.txt 11612 /var/db/pfblockerng/dnsbl/EasyList.txt 8941 /var/db/pfblockerng/dnsbl/Adaway.txt 6918 /var/db/pfblockerng/dnsbl/SWC.txt 4092 /var/db/pfblockerng/dnsbl/SFS_Toxic_BD.txt 4050 /var/db/pfblockerng/dnsbl/Spam404.txt 2931 /var/db/pfblockerng/dnsbl/EasyPrivacy.txt 1897 /var/db/pfblockerng/dnsbl/D_Me_ADs.txt 1834 /var/db/pfblockerng/dnsbl/StevenBlack_BD.txt 1547 /var/db/pfblockerng/dnsbl/MDS_Immortal.txt 568 /var/db/pfblockerng/dnsbl/CoinBlocker_Opt.txt 359 /var/db/pfblockerng/dnsbl/OpenPhish.txt 69 /var/db/pfblockerng/dnsbl/Yoyo.txt 54 /var/db/pfblockerng/dnsbl/Ponmocup.txt 39 /var/db/pfblockerng/dnsbl/MVPS.txt 18 /var/db/pfblockerng/dnsbl/D_Me_Tracking.txt 1 /var/db/pfblockerng/dnsbl/MoneroMiner.txt 1 /var/db/pfblockerng/dnsbl/EasyList_Portuguese.txt 0 /var/db/pfblockerng/dnsbl/firehol_level4.txt 0 /var/db/pfblockerng/dnsbl/firehol_level3.txt 0 /var/db/pfblockerng/dnsbl/NoCoin.txt 0 /var/db/pfblockerng/dnsbl/MDL.txt 0 /var/db/pfblockerng/dnsbl/ISC_SDL.txt 0 /var/db/pfblockerng/dnsbl/D_Me_Malw.txt 0 /var/db/pfblockerng/dnsbl/D_Me_Malv.txt 0 /var/db/pfblockerng/dnsbl/BBC_Masters.txt ====================[ IPv4/6 Last Updated List Summary ]============== Oct 18 20:16 Abuse_IPBL_v4 Nov 12 22:17 MDL_v4 Dec 13 21:57 VPS_Ger_dns_v4 Dec 13 21:57 VPS_Bel_dns_v4 Dec 13 22:04 MEO_Belverde_v4 Dec 16 23:00 Spamhaus_Drop_v4 Dec 17 03:11 Spamhaus_eDrop_v4 Dec 17 05:30 ET_Block_v4 Dec 17 05:30 ET_Comp_v4 Dec 17 23:45 home_v4 Dec 18 00:47 HoneyPot_IPs_v4 Dec 18 00:47 AS12353_Vdf_PT_v4 Dec 18 00:47 PT_v4 Dec 18 06:45 MaxMind_BD_Proxy_v4 Dec 18 14:28 ISC_Block_v4 Dec 18 16:25 Whitelist_custom_v4 Dec 18 16:25 WAN_allow_1_custom_v4 Dec 18 16:30 iphone_ap_v4 Dec 18 16:58 ISC_1000_30_v4 Dec 18 17:22 CINS_army_v4 Dec 18 17:23 BBC_C2_v4 Dec 18 17:34 BDS_Ban_v4 Dec 18 17:34 BlockListDE_Apache_v4 Dec 18 17:41 Alienvault_v4 Dec 18 18:15 Abuse_SSLBL_v4 Dec 18 18:15 Abuse_Feodo_C2_v4 Dec 18 18:15 Talos_BL_v4 Dec 18 18:15 CCT_IP_v4 ====================[ DNSBL Last Updated List Summary ]============== Jul 31 2015 D_Me_Tracking Oct 21 2019 MDS_Immortal Feb 1 2020 D_Me_ADs Jul 10 23:22 D_Me_Malw Jul 10 23:22 D_Me_Malv Aug 13 23:35 MDS Oct 18 20:15 AntiSocial_BD Oct 18 20:16 Spam404 Oct 18 20:16 MoneroMiner Oct 18 20:16 NoCoin Nov 6 12:09 CoinBlocker_All Nov 6 12:09 CoinBlocker_Opt Nov 12 22:17 MDL Nov 23 00:17 StevenBlack_BD Dec 14 00:46 anudeepND Dec 14 06:39 SWC Dec 15 07:25 Cameleon Dec 15 08:07 MVPS Dec 17 01:59 ISC_SDL Dec 17 09:47 Yoyo Dec 17 18:00 Adaway Dec 17 20:27 Ponmocup Dec 17 23:37 hosts_oisd_nl Dec 18 00:00 SFS_Toxic_BD Dec 18 00:00 OpenPhish Dec 18 00:27 BBC_Masters Dec 18 00:31 EasyList Dec 18 00:32 EasyList_Portuguese Dec 18 00:32 EasyPrivacy Dec 18 00:40 Abuse_urlhaus Dec 18 00:46 firehol_level3 Dec 18 00:46 firehol_level4 =============================================================== Database Sanity check [ PASSED ] ------------------------ Masterfile/Deny folder uniq check Deny folder/Masterfile uniq check Sync check (Pass=No IPs reported) ---------- Alias table IP Counts ----------------------------- 28262 total 22729 /var/db/aliastables/pfB_PRI1_v4.txt 2337 /var/db/aliastables/pfB_BlockListDE_v4.txt 1581 /var/db/aliastables/pfB_PRI4_v4.txt 988 /var/db/aliastables/pfB_WAN_allow_3_v4.txt 342 /var/db/aliastables/pfB_PRI2_v4.txt 240 /var/db/aliastables/pfB_PRI3_v4.txt 32 /var/db/aliastables/pfB_WAN_allow_2_v4.txt 11 /var/db/aliastables/pfB_Whitelist_v4.txt 2 /var/db/aliastables/pfB_WAN_allow_1_v4.txt pfSense Table Stats ------------------- table-entries hard limit 2000000 Table Usage Count 29609 UPDATE PROCESS ENDED [ 12/18/20 18:15:40 ]Am I doing something wrong?
Thanks.
-
@xppx99 Why do you use Alias Native ? You could probably use a regular Firewall Rule instead of using a pfBlockerNG alias.
Did you use the same Domain
redacted.ddns.net in the Source Definition AND the Custom List ? Use one or the other to see if that make a difference. -
Agreed this seems like you're doing it the hard way. A normal firewall alias can use an FQDN:
"Enter as many hosts as desired. Hosts must be specified by their IP address or fully qualified domain name (FQDN). FQDN hostnames are periodically re-resolved and updated..." -
Thank you both for the sugestion. Already implemented it and it's working great!