Nginx Messages
-
Hello.
System logs are showing repetidly messages about some error concerning to nginx. Does someone know what does this messagens mean?
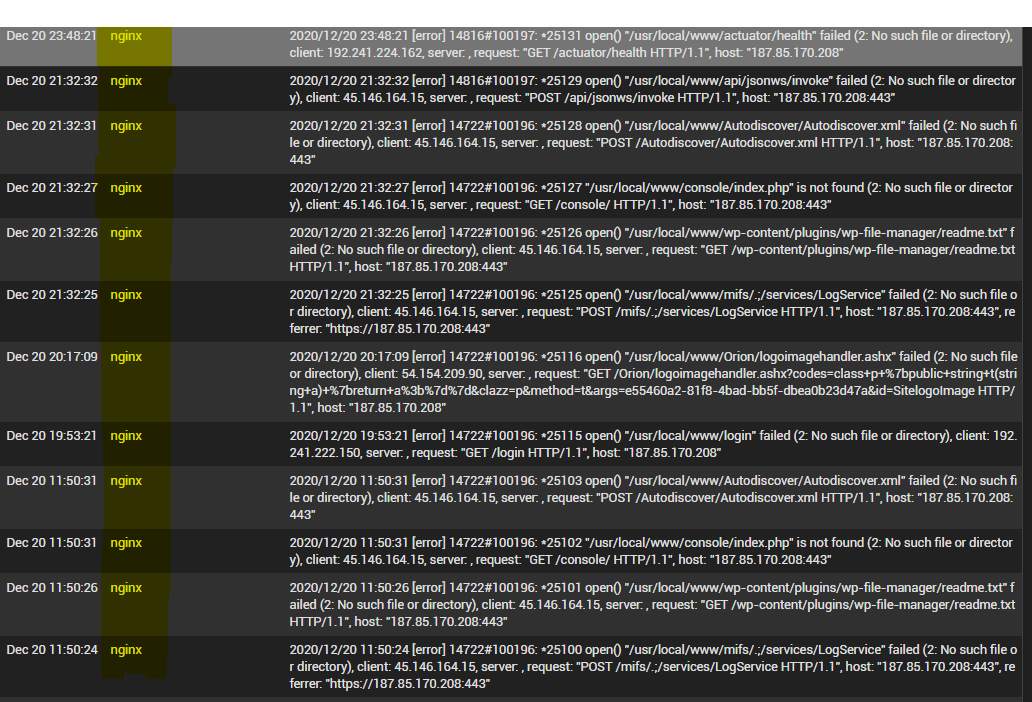
-
NGINX is the web server that serves up the web pages for the admin GUI. Do you have access to the GUI open to the internet? Because I see at least three different IP's from around the internet - one from Amazon, one from DigitalOcean, and one from the country of Cyprus - that are trying to request different pages/files.
-
@virgiliomi Thank you for your answer.
Yes. The webGUI is open to the Internet. And yes, my pfSense is under attack in the latters days. They are trying in many different ways to get access.
How do I hide webGUI from the internet? Do you konow?
-
@hugoeyng You should consider your installation compromised. Wipe it clean and start over.
-
I wouldn't consider it compromised, as those are just automatic scans looking for vulnerable software. (note the different urls for Spring Actuator, wordpress file manager, etc)
But it's best to not have the admin GUI open to the whole internet.
Also, it's critical you have a complex password and keep your PfSense up to date with any new versions just in case the old versions are discovered to be remotely exploitable.
You should have it only accessible to a narrow range of IP addresses, say your home IP or work ip address ranges.
There's likely a way to connect to it via a VPN I would think, but just limiting the external IP addresses allowed to connect remotely would narrow your attackers significantly if you can't close remote access completely.
-
@techlw Either way they should wipe it and start over. If he asks "How do I hide webGUI from the internet?" then the best way forward is to scrape it clean and reinstall. Kinda want to know how those ports were opened in the first place, or is there an any to any pass rule on the WAN? Second thought. I don't really want to know how it ended up like that...
-
@jwj That would be "safest", but all those logs are saying is that that he's being scanned and nginx is returning 404s due to those not being valid urls within PfSense.
@hugoeyng Is this an up to date PfSense install, and has it just been connected to the internet for a short time? then I don't see that you really need to wipe it.
That being said, if you did use a non-complex password like "password" or "ADMIN", then it could have been brute-forced already.
Regardless of wiping or not, you should setup a:
- Firewall Alias with his Home IP address, and say work IP address.
- Change his existing firewall rule on the WAN side to port 443 (SSL) by changing the "Source" to "Single host or alias"
- Type in the previously created Firewall Alias eg "Home_Work_access" in the host/alias field.
- Save the rule
This should drop any other attempts and your logs should stop showing the attempts.
-
@hugoeyng It looks like this is likely related to your other cross-post:
https://forum.netgate.com/topic/159166/firewall-log-attack-warning
I would work with them in that thread, as these logs are related to https (port 443) traffic.
-
@techlw I will turn disabled rules concerning 443 port that allow access from unrestricted IP´s.
Thank you for your answer.
-
@techlw I disabled rules concerning 443 port that allow access from unrestricted IP´s and NO MORE log messages like above.
I will keep paying attention.
I still want to find out how to have access to webGUI over Internet without oppening th 443 port to any IP.
-
@techlw said in Nginx Messages:
@jwj That would be "safest", but all those logs are saying is that that he's being scanned and nginx is returning 404s due to those not being valid urls within PfSense.
@hugoeyng Is this an up to date PfSense install, and has it just been connected to the internet for a short time? then I don't see that you really need to wipe it.
That being said, if you did use a non-complex password like "password" or "ADMIN", then it could have been brute-forced already.
Regardless of wiping or not, you should setup a:
- Firewall Alias with his Home IP address, and say work IP address.
- Change his existing firewall rule on the WAN side to port 443 (SSL) by changing the "Source" to "Single host or alias"
- Type in the previously created Firewall Alias eg "Home_Work_access" in the host/alias field.
- Save the rule
This should drop any other attempts and your logs should stop showing the attempts.
I have the alias containg my home IP´s address. But this doesn´t help when I am not at home, or when I using my smartphone (4G/5G).
When I am not at home and I have acces to my laptop I can use a VPN connection, but in some cases I have to access the webGUI from "strange" machines.
-
@hugoeyng said in Nginx Messages:
How do I hide webGUI from the internet? Do you konow?
The question is wrong, and scary.
When you installed pfSense, its GUI could not be visited from the outside, from the WAN side.
Then the admin did something that changes this.
And now the admin asks why it happens ??@hugoeyng said in Nginx Messages:
When I am not at home and I have acces to my laptop I can use a VPN connection, but in some cases I have to access the webGUI from "strange" machines.
One solution exists : stick to your laptop, or better : use your phone.
Like : your phone shares the network acces, and your laptop connects to the phone (wifi) so it uses its broadband connection.
Using "not your devices" from "not known IPs" is just NOT done.If you really have to, create a bootable USB with an OpenVPN client pre set up. this way you can use any device - without risking that device neither your own home set-up.
About the NGINX logs you showed : these are normal. I see the same lines on all the web servers on all my public IP's on my 'public' servers (dedicated servers). Hundreds, probably thousands per hours. They are all fail2ban food.
-
@gertjan The question was not about "why it happens". The question was "how to avoid it happens".
I deactived the firewall rule that pass all connection to the 443 port. This avoid the webGUI being visited from outside.