Isolate Guest Network on AP
-
Not sure where the OP's security concerns originate. Work from home issues? The kids Chromebooks bother me less than the IoT stuff he alludes to. I'd be defending myself from those items more than the kids stuff. More about that below, in the form of a rant.
TL-SG1024DE is a TP-Link smart switch and the AX1800 is a TP-Link WiFi6 router. The OP should be able to config that stuff to do what he is after, I think. I'm not downloading the specs or user guide... @cburbs have a look at the documentation. TP-Link documentation can be awful but it's a start and you can come back here with specific questions. You'll get help when you do that.
As far as TP-Link is concerned generally I think the warning is true in some cases, but...
If you have WAN, LAN (default vlan, 1) and Guest (some vlan), it doesn't matter if you can't change the default vlan.
I have heard, never seen pcaps to demonstrate, that some TP link switches and AP's leak packets to the default vlan. That's a problem. Question is which switches and AP's have this problem? Has the firmware been updated to fix it for some models. Which ones.
In the end, you get what you pay for. For a lot of people what they want isn't much. Here in pfsense land the average user is more aware and has greater needs that represent maybe 1% (unsubstantiated claim based on no data ;) ) of home networks...
Yes, TP-Link has been sloppy in ways that never should happen.
More than once I've had people I know say they want to this, this, this and that with their home network. I always ask why? A lot of the time I end up pointing them to something like EERO (not so much in the Amazon era of EERO) and maybe a $20 unmanaged switch to hook up their TV and small NAS if that makes sense.
<rant>
I always warn people about cheap IoT crap. Do you need to be able to turn the bedroom lamp off from your phone? That $40 smart bulb may cost you a ton to defend yourself when it is turned into a zombie agent of all things bad. Internet connected door bell and camera? Garage door opener? I just don't get it. $200 dollar solutions to $5 problems. Need a ring because of porch pirates? Better to get your town to stop spending on urban/tactical assault vehicles and all the chattel that goes with that and give the PD new shoes and have them out walking the neighborhoods. Or just have your amazons dropped in a locker at whole foods. All these technology solutions make about as much sense as putting the horse first in a parade. Nothing good will come of it...
</rant>I'm done. Seasons greetings to all and a very happy new year!
-
@jwj In regards to the switch -
Quality of Service
Support Port-based/802.1p/DSCP priority
Support 4 priority queues
Rate Limit
Storm Control
L2 Features
IGMP Snooping V1/V2/V3
Static Link Aggregation
Port Mirroring
Cable Diagnostics
Loop Prevention
VLAN
Supports up to 32 VLANs simultaneously (out of 4K VLAN IDs)
MTU/Port/Tag VLANIt doesn't look like the AP does Vlans. I see that if you do DDWRT etc you can get that option.
So I guess if one was to buy a new wireless router to use as an AP with VLans which would you buy? A couple suggestions on that part would be great.
-
@cburbs That switch will do what you would need.
Can you add additional ssids (wireless networks, what you see when you connect to you wifi) to you access point? If so, do you have a choice to assign a network to that ssid?
Wait a minute... I'll go fetch the guide for that thing and get back at ya in a moment :)
That's a good sign... moment more please.
-
Hi,
Why don't you make an Quest Network, and your kids only use that one.
Here is an emulator of the AX1800.
Make sure you uncheck: Allow guests to see each other and Allow guests to access your local network.https://emulator.tp-link.com/Archer_AX1800v1.20_US_simulator/#guestNetworkAdv
Password: admin
Click Advanced - Wireless - Guest Network
-
OK, spent a minute in the emulator. I didn't see what I was hoping to see. It says you can create a Guest network when in access point mode but there are no settings beyond those simple few things. I do wonder what is a Guest (or other) network on that thing...
So, wish I could offer you more. But sorry to say I have no idea if you bend that router/access point to you will...
DDWRT or openwrt may be an option. I'm not going to say you should do that because you can brick devices when installing it and then you will be mad at me...
Maybe Santa will deliver a shiny new dedicated access point? Ones worth having don't come cheap. Unifi is cheap but the company is a dumpster fire. Netgear can be OK. Splash out some bigger bucks, Ruckus, Aruba, Cisco. I'd want to know a lot more about your environment before pointing you at that kind of money. That said, something like a Ruckus would be a long term item. You'd be very happy with that for many years to come...
-
@jwj Yeah once it goes into AP mode you lose most of its functionality.
So I have an older Asus RT-N66R that I am going to throw DDWRT on it and see if I can play around with it.
Though I need a replacement for the Asus as it was getting old and the signal strength wasn't the greatest in the opposite corner of the house upstairs. The AX1800 helped resolve that issue but now that I am looking to isolate things more I need a different solution.Again any suggestions on one that can do Vlans with ddwrt,openwrt, etc?
Also new to VLANS so is this a good article to follow on getting the Asus setup as a test for now....https://netosec.com/protect-home-network/ and part of this article https://netosec.com/dd-wrt-wifi-vlans/ or is there an easier way to do this?
-
@cburbs I edited my post above with some more thoughts...
-
@jwj Yeah this has been an interesting adventure and now has me rethinking my whole envrionment. So besides this isolation I want to do some more if possible but need to put all my items in a list and figure out how I want them isolated, etc. That article at netosec is the one that made me rethink everything.
-
As far as how good your WiFi is often has more to do with placement than the hardware itself. Most dedicated access points are ceiling mount. Find the optimal location and it can work miracles for your WLAN.
Unifi stuff uses cheap consumer components in their products. It's just bundled up like enterprise gear. Mount it on the ceiling in a good spot, make sure you set it up to minimize adjacent channel interference and it almost works like enterprise gear. Until you have more than just a few users... That is probably good enough for most home situations. This hits the sweet spot for almost every home network. https://www.ui.com/unifi/unifi-ap-ac-pro/
Find the firmware version that works best, not always the latest stable version and don't upgrade it unless you have a real reason to do so. It's the software that can be terrible with their stuff...
I'm going to upgrade from Unifi soon. 99% sure it will be Ruckus. I hope to find 3 AP's (R710) used for around 3 or 4 hundred a piece. It's a good chunk of change but I know I will enjoy not have to mess with them for a long time...
-
@cburbs Have a look at the vlans section of the pfsense documentation. Good stuff. Also LOTS of good threads here on the forum. You have to sort through the noise a bit, but lots of good advice can be found.
-
@jwj said in Isolate Guest Network on AP:
I have heard, never seen pcaps to demonstrate, that some TP link switches and AP's leak packets to the default vlan. That's a problem. Question is which switches and AP's have this problem? Has the firmware been updated to fix it for some models. Which ones.
In the end, you get what you pay for.I don't know the problem exists with all models, but certainly the low end managed switches and AP have it. You can get similarly priced gear from other makes. The problem I experienced with my AP is that multicasts leaked from the main LAN/SSID to VLAN/2nd SSID. This made it impossible to use IPv6 on my guest network.
-
@jknott Well that is a problem. Goes beyond just sloppy...
I have a couple of unused TP-Link switches in a closet. Kinda want to sell them off but also don't want to pawn them off on someone who will then have problems. I'd just trash them but that's not very responsible either.
-
-
Ok so I now have 2 Wireless networks setup on the DDWRT AP.

On the pfSense box I setup the two Vlans

On the switch I want to plug the AP into port 7.
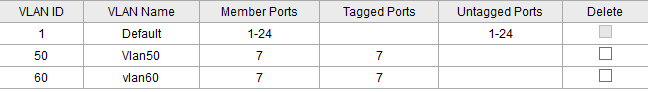
But when I do the above I am still getting an IP from the pfSense DHCP and not from either of the Vlans.
-
Did you set up DHCP servers on each of the VLANs? I assume you have different SSIDs for the VLANs.
-
Correct - Vlan 50, enable DHCP, set IP Range, etc
Different SSIDs for the vlans as well.
can I connect any port from the AP to Port 7 on the switch?
-
The ports connected to both pfsense and the AP have to be able to pass the VLANs. For example, my guest WiFi is on VLAN3. So, I configured VLAN3 on pfsense, my AP and on the appropriate switch ports.
-
In the switch you need those VLANs to be tagged on both the port connected to the AP and the port connected to pfSense.
And you need to remove port 7 from the default vlan, unless you have a third SSID there that's untagged.
However the fact you were still pulling an IP from the LAN subnet also suggests those new SSIDs are now using the VLANs correctly in the AP.
Can we see an ifconfig output from the AP?Steve
-
@stephenw10 Sorry I was wrong on that no IPs while connected to the ddwrt ap wireless.
Something still wrong with my config and trying to look at this as somewhat of a reference point - https://www.tp-link.com/us/support/faq/788/.
This is what I am after as a test ....
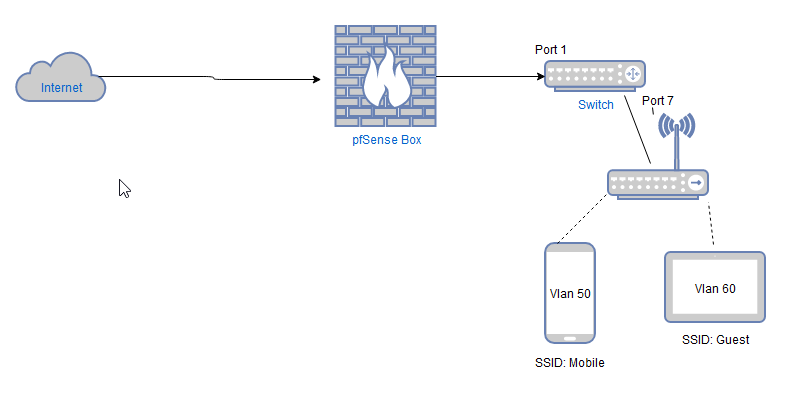
So Pfsense plugs into Port 1 on Switch.
Asus AP(DDWRT) plugs into Port 7 on Switch.Two Vlans setup on DDWRT
SSID: Mobile - Vlan 50
SSID: Guest - Vlan60 -
Yes, so the in the switch config VLAN IDs 50 and 60 need to have both ports 1 and 7 as members and tagged.