Suricata Rule management
-
Hi,
I am looking for a way to activate all the rules of the rule sets at once.
Furthermore, I am looking for an overview of how many are active on the respective controllers.
Is there a possibility for the two especially for the first point?
-
@deleted said in Suricata Rule management:
Hi,
I am looking for a way to activate all the rules of the rule sets at once.
Furthermore, I am looking for an overview of how many are active on the respective controllers.
Is there a possibility for the two especially for the first point?
There is no "activate all" feature -- and for good reason. It is a very bad idea. No serious IDS/IPS admin would ever consider activating every single rule in every single category of the vendor rule packages. You would very likely bring your network to its knees.
And why would you want to waste CPU and RAM resources loading up rules that detect threats to exposures you may not have on your network? For example, if you do not have an external facing DNS server handing public DNS requests from the WAN, then why run the DNS Server rules? Ditto for email. If you don't have a public facing mail server why run the SMTP rules? And if you don't have a public facing web server, why run the web server rules? And I could keep going with other examples.
You should learn to manage your enabled rules so that you cover threats to the attack surfaces your network actually presents. Your firewall will run smoother and so will your network with likely fewer false-positive blocks.
-
@bmeeks said in Suricata Rule management:
There is no "activate all" feature -- and for good reason. It is a very bad idea. No serious IDS/IPS admin would ever consider activating every single rule in every single category of the vendor rule packages. You would very likely bring your network to its knees.
And why would you want to waste CPU and RAM resources loading up rules that detect threats to exposures you may not have on your network? For example, if you do not have an external facing DNS server handing public DNS requests from the WAN, then why run the DNS Server rules? Ditto for email. If you don't have a public facing mail server why run the SMTP rules? And if you don't have a public facing web server, why run the web server rules? And I could keep going with other examples.
You should learn to manage your enabled rules so that you cover threats to the attack surfaces your network actually presents. Your firewall will run smoother and so will your network with likely fewer false-positive blocks.
Whew. Be that as it may. Anyway!
Does anyone else have a workaround for me?
-
@deleted said in Suricata Rule management:
@bmeeks said in Suricata Rule management:
There is no "activate all" feature -- and for good reason. It is a very bad idea. No serious IDS/IPS admin would ever consider activating every single rule in every single category of the vendor rule packages. You would very likely bring your network to its knees.
And why would you want to waste CPU and RAM resources loading up rules that detect threats to exposures you may not have on your network? For example, if you do not have an external facing DNS server handing public DNS requests from the WAN, then why run the DNS Server rules? Ditto for email. If you don't have a public facing mail server why run the SMTP rules? And if you don't have a public facing web server, why run the web server rules? And I could keep going with other examples.
You should learn to manage your enabled rules so that you cover threats to the attack surfaces your network actually presents. Your firewall will run smoother and so will your network with likely fewer false-positive blocks.
Whew. Be that as it may. Anyway!
Does anyone else have a workaround for me?
Just so you know, I am the creator and maintainer for the Suricata package. I am offering you sage advice from an experienced IDS/IPS admin - not trying to berate you. Your request indicates perhaps you are new to IDS/IPS administration, so I was offering some advice.
However, if you want to activate all the rules anyway, then the only method is to go to the CATEGORIES tab and check every category there and save the change. Next, go to the RULES tab and then do the following steps:
-
Select a category in the drop-down selector.
-
Click the Enable All button to force enable all rules in that category.
-
Click Save to save the edit.
-
Rinse and repeat for each category.
Your
config.xmlfile for the firewall will now get larger due to the huge list of forced-enabled GID:SID pairs, your RAM consumption will increase substantially, and you should start getting a boatload of alerts (a good many of which will likely be false positives). If you have blocking enabled, that boatload of alerts will translate into a boatload of blocked IPs. I'm betting a lot of those blocked IPs will be things you actually want to access.There is a reason the rule vendors ship a lot of their rules default-disabled (commented out). It's because not all networks have the same attack surfaces, and several of those rules are very prone to false positives in most networks. Thus the vendors comment them out for general use. If you want to see an example of this, open up and examine the
snort_protocol-dnsrules category (if you have the Snort Subscriber Rules enabled for download). Quite a number of those rules are default-disabled by the rule authors (the pound sign "#" in front of a line comments out that rule so it does not get loaded by Suricata or Snort). -
-
All good. I also did not mean to insult you or devalue you as incompetent.
If you are the creator and maintainer for the Suricata package I would like to formally thank you for the work. It was among other things the good implementation of Suricata in pfsense that made me choose Netgate.
To be honest, in the first moment I found it strange how someone knows what services are running in my network based on my question.
You are right with your listings. However, these have already been included in the design of the firewall.
The config.xml will indeed be filled with a lot of rules. However, the write access as it ends up in the ram and to users accessing it will be limited. I think there is still room for maneuver even if you use a lot of entries until you have to replace the file with another solution.
The Ram consumption increases in fact also. However, a problem only arises on the hardware side.
Basically you are also right, you don't need to load SMTP rules if you don't have a Public Mail Server.
However, my thought goes further at this point.
I think it is possible to increase the security of the network with a little more ram.
In case of a hybrid attack I expect significant advantages.
Furthermore, I can control exactly which IP's are excluded, then it only hits unauthorized ones.
(I hope you could read my bad english and know how that means.)
-
While I still disagree with the strategy of enabling every rule in every category, if you want to proceed with it the most efficient way will be to use the functionality on the SID MGMT tab to achieve the goal. That will result in less storage consumption in the
config.xmlfile.Enable the automatic SID management feature on that tab (check the box to enable and save that change), then create a custom
enablesid.conffile using the examples from the sample files available on that page. You can list all the category names, and then follow that with a very wide SID range. That should result in all rules being enabled. Read through the sample files on that tab to get an idea of how the feature works. It uses Perl regular expression logic (regex) to select rules. -
I just wanted to copy an interface where many rules are already activated.
This was not possible. Without error message. Was there a change, I am sure to have done this before?
Otherwise I will have to take the time to activate all of them. Or I will implement your suggestion.
One last question. Is there anywhere to see how many rules are currently active and how many are not?
Thanks for your help!
-
@deleted said in Suricata Rule management:
I just wanted to copy an interface where many rules are already activated.
This was not possible. Without error message. Was there a change, I am sure to have done this before?
What was the error message?
One last question. Is there anywhere to see how many rules are currently active and how many are not?
Thanks for your help!
You can see how many are active by going to the RULES tab and then choosing "Active Rules" in the drop-down selector there. It may take a very long time to finish populating the page if a lot of rules are selected. There is no way to easily see "not active" rules.
-
@bmeeks said in Suricata Rule management:
What was the error message?
There is no error message. Also no entry in the log.
I have pressed the button to copy.
Then edited and saved the interface and the description.Then I was back on the overview page. However, no copy was made.
However, since I used the function for the last time in another patch version, I wanted to see if there were changes and I have overlooked something.
-
What information / logs do you need?
I tried again, a copy is still not possible. There is no entry in the Suricata logs.
-
@deleted said in Suricata Rule management:
What information / logs do you need?
I tried again, a copy is still not possible. There is no entry in the Suricata logs.
I've put this issue on my "TO DO" list for the next upgrade. I will test and fix anything I find not working. There have been more hands than just mine in the Suricata GUI code over the last couple of years, so very possible something got messed up. That feature is not routinely tested, and is apparently seldom used.
-
@deleted said in Suricata Rule management:
What information / logs do you need?
I tried again, a copy is still not possible. There is no entry in the Suricata logs.
I just tested the interface copy feature in a virtual machine and it worked as designed. Here is a screenshot. I copied the existing LAN interface over to OPT1.
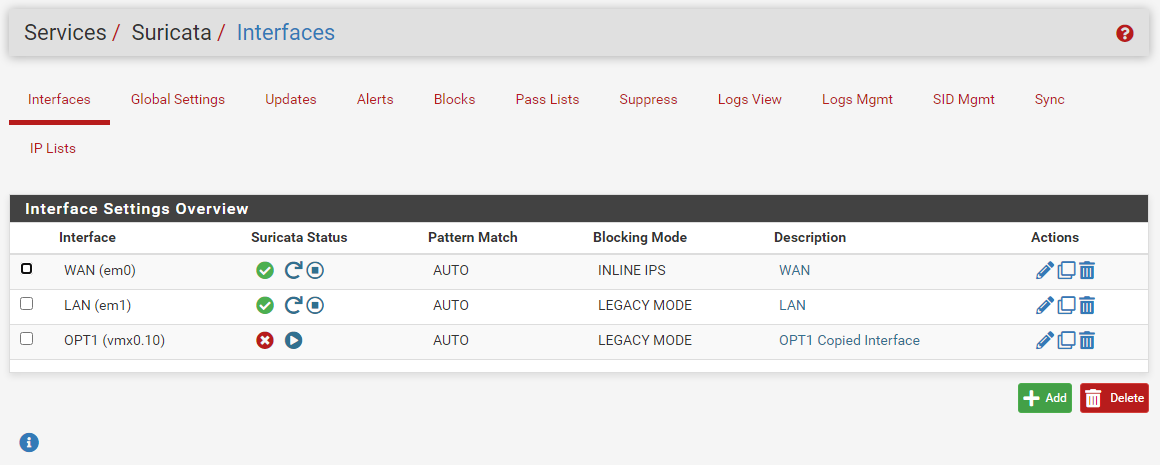
You can only copy interfaces when an existing open and enabled interface exists in pfSense itself. So maybe you do not have any available enabled interfaces in pfSense?
-
This post is deleted! -
Sorry.
My example was disabled.
With this it works and I can save myself the work of activating everything.
Then I only have to look at what is newly added and disabled.
Thank you very much for your help.