Allowed but blocked
-
Hi all,
Firewall log shows there's blocking.
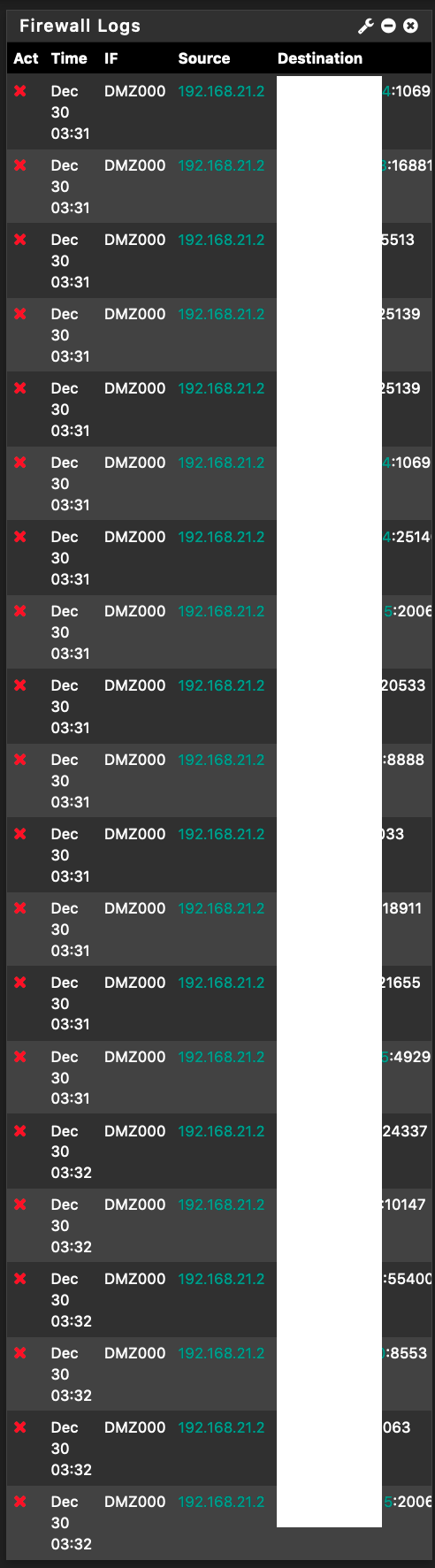
Says the rule that triggered the action is :
@9 Default deny rule IPv4
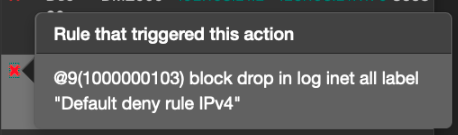
I have no idea where to locate such rule, however I've tried:
- Allow TCP/UDP ServerBT 1024:65535 to !RFC1918 any , at the top of floating rule OR
- Disable PfB and DNSBL
Above makes no difference.
Below are my screenshots, any pointers?
Thank you for your time in advance.Order of rules (simplified)
- Floating
- Interface Groups
- Interface
Floating Rules

Interface Group Rules
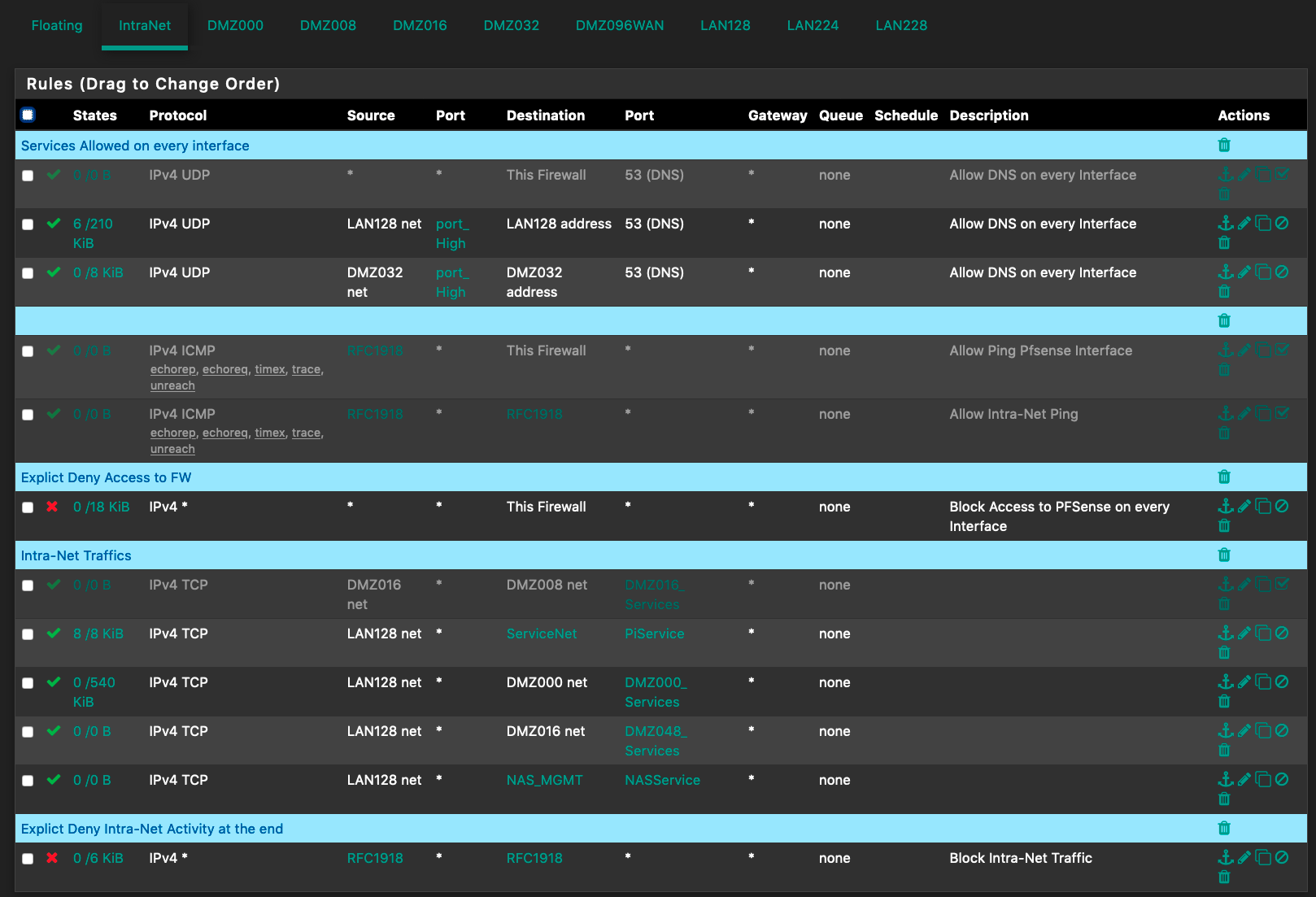
Interface Group Members

Interface Rules
That's Allow TCP/UDP (192.168.21.2 ServerBT) 1024:65535 to !RFC1918 any
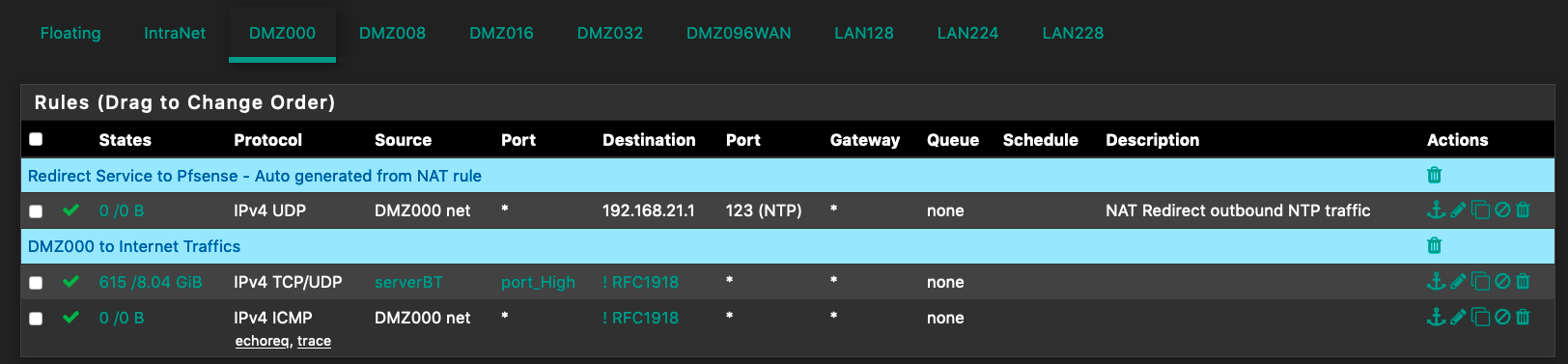
PfB IPv4 Inbound Only
Reload All after every related rule change
-
@ccieneverbe
The "Default deny rule" is what its name imply, it's a default rule on all pfSense interfaces on the very last position, but it is not shown in the rule set.What is the state of the blocked packets? Often it are out of state packets, which are blocked by this rule.
-
Thank you for your time!
How does one find out the state of the blocked packets if PfSense? Where to click? (I don't know how, I am asking.)Having asking the above, your pointer did steer me towards solving the puzzle.
Was in Aggressive mode
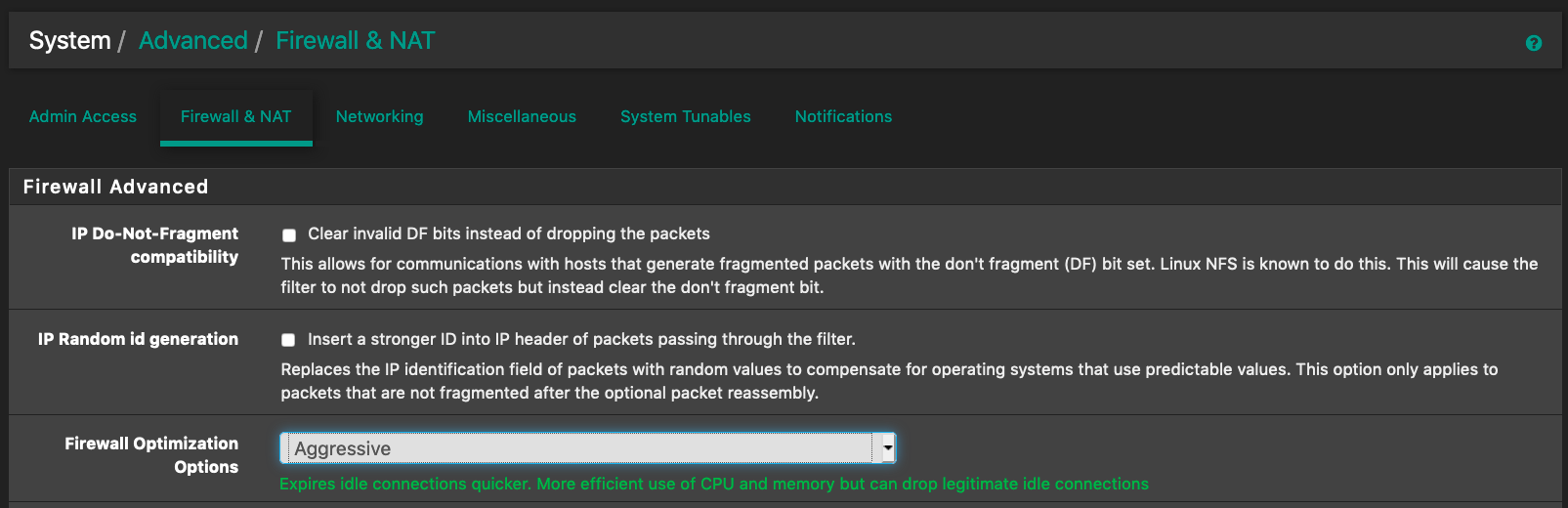
Now switch back to default normal mode
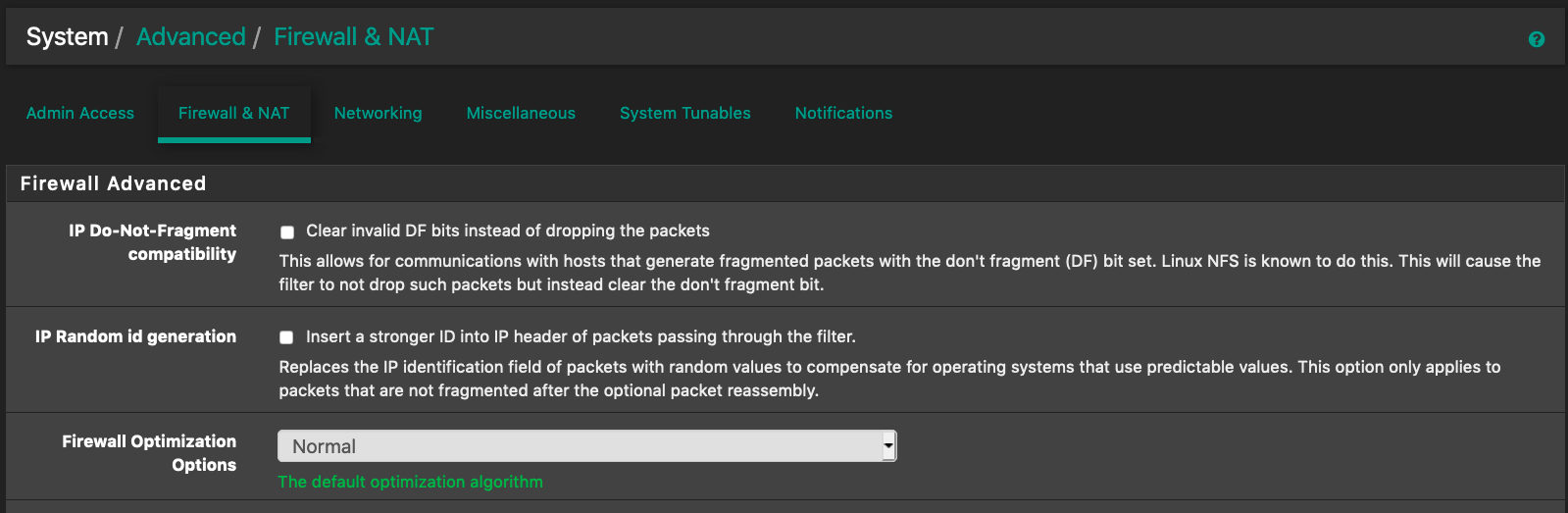
And what the Firewall log looks like now

When in Aggressive mode, log would show multiple same dst:port being blocked in a row in a minute. And multiple IPs are getting blocked.
The port number suggest those are trackers (6969 8888 7777 8080 80...etc).When in Normal mode, log would show mostly different IPs in each row, same IPs still appear, but further apart and happens a lot less say one log every 15 minutes.
The port number (looks to me) are peers (18213 16881 22776 12530...etc).For now, I much prefer the look of the logs in Normal mode than in Aggressive mode.
I would probably try conservative to see the difference.
Thanks @viragomann
-
@ccieneverbe said in Allowed but blocked:
How does one find out the state of the blocked packets if PfSense?
You can see it on the packet flag in the log. The flag is shown in the very right column.
A possible reason for out-of-state packets is an asymmetric routing. If that is the case, the firewall mode is not the right way to fight the problem. Normally in normal mode the state life time should be long enough for the most purposes.
-
Found them and saw them, bunch of TCP:FA and TCP:FPA.
From there led me to a similar post, then I did uncheck below box
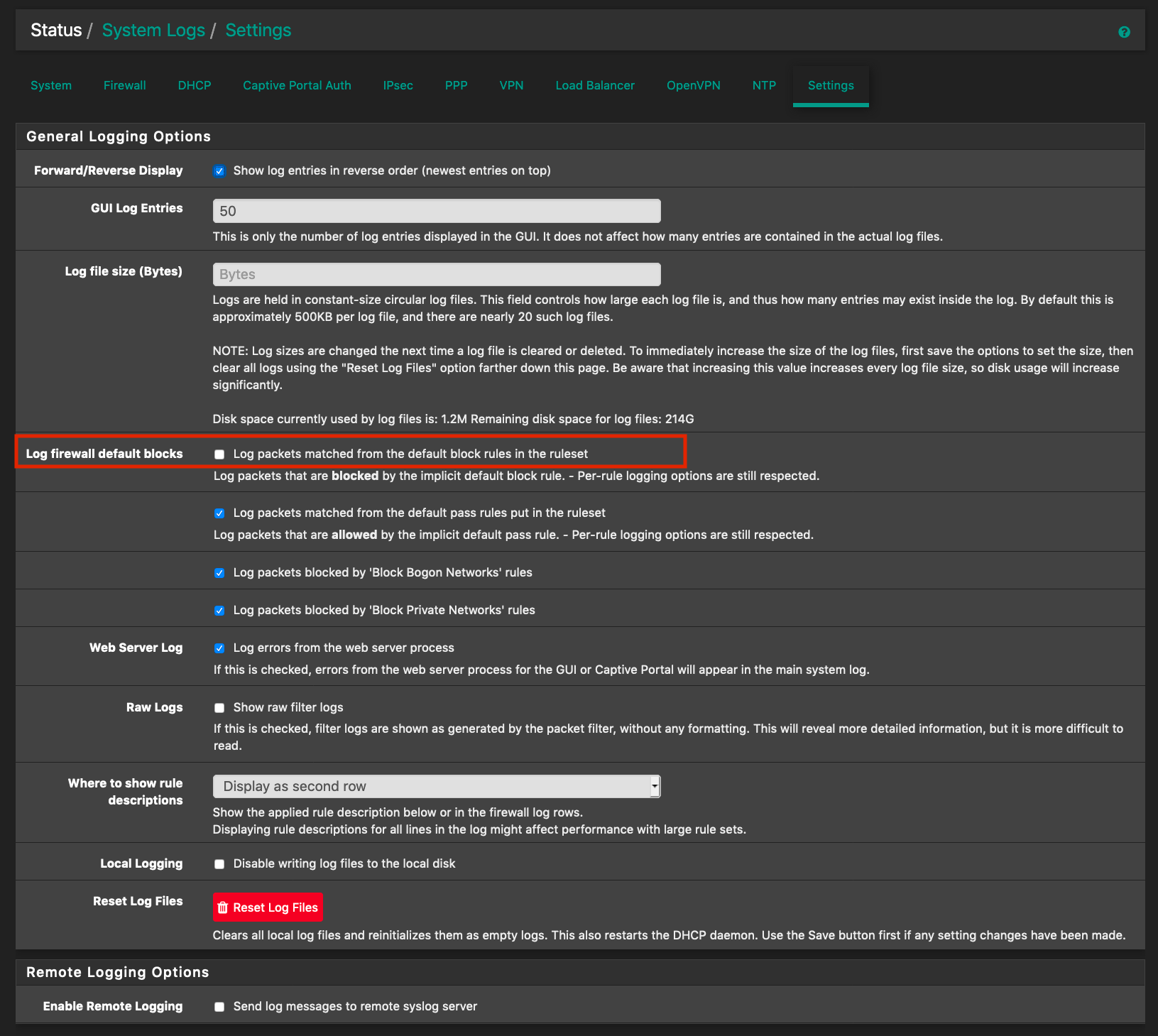
And it's all gone.
Thanks for the tips @viragomann
Now, on next: multi LAN, Pi-hole, Unbound
:-) -
@ccieneverbe
Disabling logging is not a real solution. You'd better solve your asymmetric routing issues.
You have to find which traffic is affected. Seems to me like it are response packets, but without knowing, what kind of traffic it is and how your network is designed, it's a view in the crystal ball. -
Thanks for saying.
I'll keep an eye on this.
For now torrents are downloading. I was bothered by the FW log because it mentioned rule I failed to locate, making me belief actions were performed against my design.
It's interesting of the perspective shifts, from looking to place tech at home capable of filtering traffics at best; to asking on forum why can't the tech just allow it all .