Site-to-site VPN, can only connect one direction to appliance
-
Hi,
I have 2 XG-7100 pfense appliances in a site to site VPN using OpenVPN. Let's call them Site A with Appliance A, and Site B with Appliance B.All hosts from Site A can ping Site B and vice versa. However, I'm not able to connect to the LAN interface of Appliance B from Site A. I am able to connect to the LAN interface of Appliance A from Site B, and I'm also able to connect to Appliance A using the using the openvpn tunnel IP.
I know there are some other similar postings, but I didn't find those applicable to this specific case.
I checked the firewall logs, and don't see anything in there. Any other ideas on what I can check to debug?
Thanks!
-
Please share your OpenVPN Configuration, Firewall Rules and LAN Interface Configuration via Screenshots.
ATM we know nothing about your setup, not even which OpenVPN server mode you are running.-Rico
-
@rico said in Site-to-site VPN, can only connect one direction to appliance:
Please share your OpenVPN Configuration, Firewall Rules and LAN Interface Configuration via Screenshots.
ATM we know nothing about your setup, not even which OpenVPN server mode you are running.-Rico
Hi,
Please find screenshots here: https://imgur.com/a/Wgumzm3Let me know if there's any other info, I can provide.
Thanks
-
192.168.96.0/19 overlaps your tunnel network 192.168.121.0/24
Why do you use /19 as Remote Networks and not your 192.168.33.0/24 and 192.168.97.0/24 to be more specific?
BTW, you can upload pictures directly into the forum.-Rico
-
@rico said in Site-to-site VPN, can only connect one direction to appliance:
192.168.96.0/19 overlaps your tunnel network 192.168.121.0/24
Why do you use /19 as Remote Networks and not your 192.168.33.0/24 and 192.168.97.0/24 to be more specific?
BTW, you can upload pictures directly into the forum.-Rico
Shouldn't the tunnel be part of the of the network to be routed? i.e. part of site B, given site B is acting as the server?
I've used /19 so I can add more VLANs to each site without having to reconfigure anything.
-
No, the tunnel network is used internally by OpenVPN between tunnel endpoints.
Pick a network that it is not in use locally or at any remote site.-Rico
-
Informational:
https://community.openvpn.net/openvpn/wiki/AvoidRoutingConflicts -
@rico said in Site-to-site VPN, can only connect one direction to appliance:
No, the tunnel network is used internally by OpenVPN between tunnel endpoints.
Pick a network that it is not in use locally or at any remote site.-Rico
I've changed the tunnel network to: 192.168.224.0/30 (on both appliances), but still seeing the same issue.
-
Did you try to be more specific with the Remote networks?
For the box with pfSense LAN IP 192.168.33.1/24 set the OpenVPN Remote network to 192.168.97.0/24
For the box with pfSense LAN IP 192.168.97.1/24 set the OpenVPN Remote network to 192.168.33.0/24-Rico
-
@rico said in Site-to-site VPN, can only connect one direction to appliance:
Did you try to be more specific with the Remote networks?
For the box with pfSense LAN IP 192.168.33.1/24 set the OpenVPN Remote network to 192.168.97.0/24
For the box with pfSense LAN IP 192.168.97.1/24 set the OpenVPN Remote network to 192.168.33.0/24-Rico
Just tried that as well, unfortunately no luck.
-
Could there be something else overlapping, like an IPsec tunnel?
What exactly is not working? You can't ping 192.168.97.1 from that 192.168.33.1 pfSense Box?-Rico
-
@rico said in Site-to-site VPN, can only connect one direction to appliance:
Could there be something else overlapping, like an IPsec tunnel?
What exactly is not working? You can't ping 192.168.97.1 from that 192.168.33.1 pfSense Box?-Rico
Correct, the issue is that I can't ping 192.168.97.1 from anywhere in Site A. So I can' t ping 192.168.97.1 from 192.168.33.1 or from any other hosts like 192.168.33.2, etc.
Site A doesn't have any ipsec tunnels. Site B (192.168.97.0/24) has an IPSec tunnel to Site C which is an Azure gateway (not pfsense). Here's the configuration:
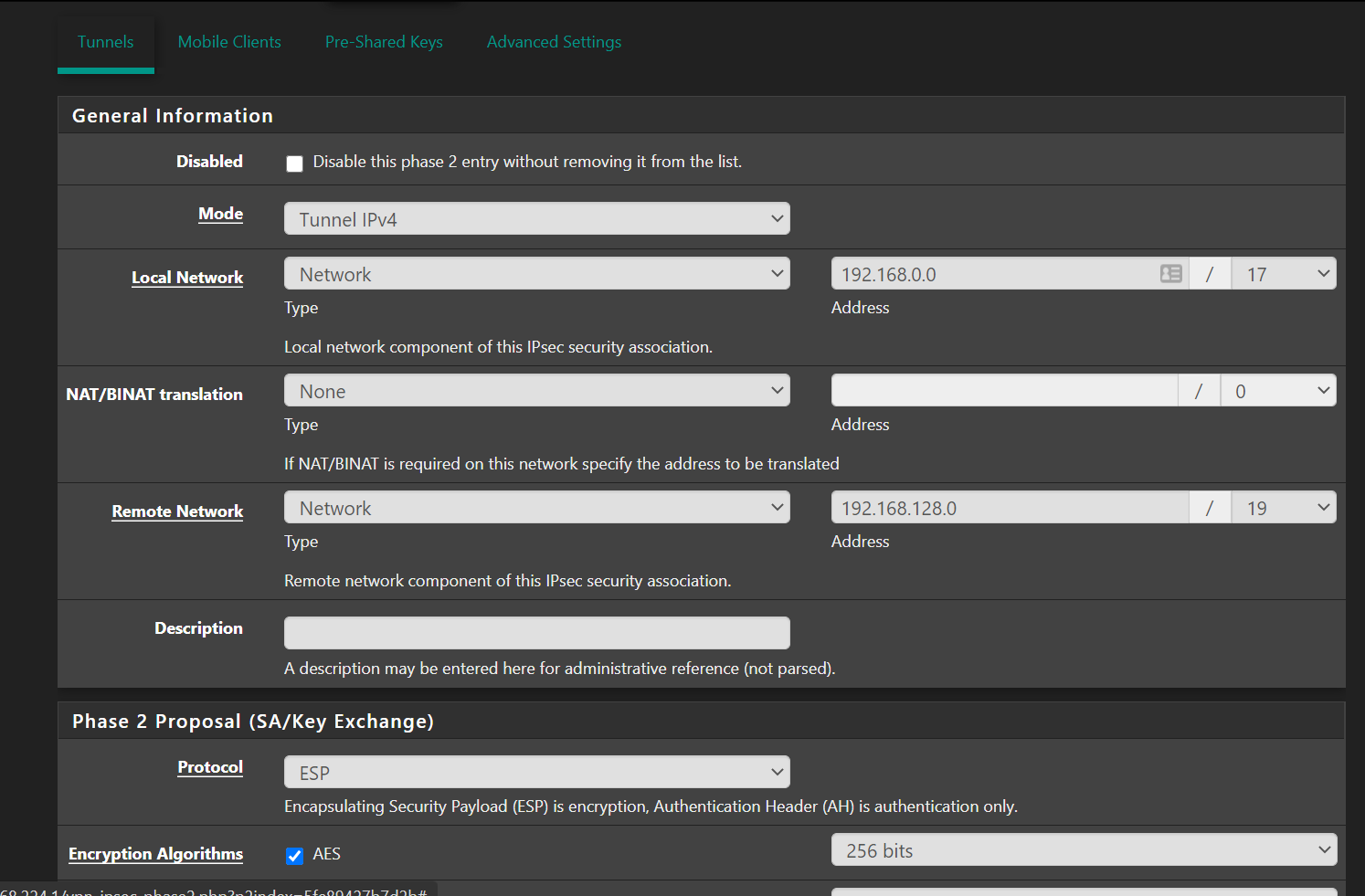
-
Your IPSec Local Network overlaps 192.168.97.0/24 and 192.168.33.0/24
I'm not really into IPsec, but pretty sure it could grab that OpenVPN traffic.
TBH, I lose track a bit about your whole setup, it is not easy to follow which site is which Configuration, Rules or even local/remote networks.
It could help to sketch up your network layout.-Rico
-
@rico said in Site-to-site VPN, can only connect one direction to appliance:
Your IPSec Local Network overlaps 192.168.97.0/24 and 192.168.33.0/24
I'm not really into IPsec, but pretty sure it could grab that OpenVPN traffic.
TBH, I lose track a bit about your whole setup, it is not easy to follow which site is which Configuration, Rules or even local/remote networks.
It could help to sketch up your network layout.-Rico
Thanks for all your help, but it actually looks like everything was correct in terms of settings, I just needed to reboot the appliance and it worked. I didn't realize rebooting would help here