Client Export Issue
-
Hello everyone,
i have 3 pfsense boxes on hardware, all running version 2.4.5-p1. (latest)
same Open VPN configuration on all. The client exports are different !!! actually 1-2 are working, 3 is not. All exports is with windows 10 latest export (2.5, not legacy)
The difference is on Cipher lines. i don't know why. Anyone with experience with this ?
Servers and settings and networks are ok , triple checked. If i manually edit the .ovpn pfsense 3 is working. I just want to know what's wrong. Thanks for any suggestions.pfsense1-pfSense-UDP4-1194-config.ovpn
dev tun
persist-tun
persist-key
cipher AES-128-CBC
data-ciphers AES-128-GCM
auth SHA1
tls-client
client
resolv-retry infinite
remote 192.168.2.21 1194 udp4
auth-user-pass
ca makariou-pfSense-UDP4-1194-ca.crt
tls-auth makariou-pfSense-UDP4-1194-tls.key 1
remote-cert-tls serverpfsense2-pfSense-UDP4-1194-config.ovpn
dev tun
persist-tun
persist-key
ncp-ciphers AES-128-GCM
cipher AES-128-CBC
auth SHA1
tls-client
client
resolv-retry infinite
remote 192.168.2.22 1194 udp
auth-user-pass
ca pfSense-client-UDP4-1194-ca.crt
tls-auth pfSense-client-UDP4-1194-tls.key 1
remote-cert-tls serverpfsense3-pfSense-UDP4-1194-config.ovpn
dev tun
persist-tun
persist-key
data-ciphers AES-128-GCM
data-ciphers-fallback AES-128-CBC
auth SHA1
tls-client
client
resolv-retry infinite
remote 192.168.2.23 1194 udp4
auth-user-pass
ca pfSense-client-UDP4-1194-ca.crt
tls-auth pfSense-client-UDP4-1194-tls.key 1
remote-cert-tls serverError from windows client:
2020-12-30 21:48:12 OpenVPN 2.5.0 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Oct 28 2020
2020-12-30 21:48:12 Windows version 10.0 (Windows 10 or greater) 64bit
2020-12-30 21:48:12 library versions: OpenSSL 1.1.1h 22 Sep 2020, LZO 2.10
Enter Management Password:
2020-12-30 21:48:14 TCP/UDP: Preserving recently used remote address: [AF_INET]192.168.2.23:1194
2020-12-30 21:48:14 UDPv4 link local (bound): [AF_INET][undef]:1194
2020-12-30 21:48:14 UDPv4 link remote: [AF_INET]192.168.2.23:1194
2020-12-30 21:48:14 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
2020-12-30 21:48:14 [VPN-certificate] Peer Connection Initiated with [AF_INET]192.168.2.23:1194
2020-12-30 21:48:16 OPTIONS ERROR: failed to negotiate cipher with server. Add the server's cipher ('AES-128-CBC') to --data-ciphers (currently 'AES-128-GCM') if you want to connect to this server.
2020-12-30 21:48:16 ERROR: Failed to apply push options
2020-12-30 21:48:16 Failed to open tun/tap interface
2020-12-30 21:48:16 SIGUSR1[soft,process-push-msg-failed] received, process restarting(and repeats...)
-
@bambos
Look at your ciphers , in the server definitionsThey are not the same on all 3 instances.
Maybe make 3 use the same ciphers as 1 or 2
-
Dear @bingo600 ,
The ciphers are the same on all 3 setups. The issue is that one of them exporting on cipher line an added term of "fallback". This instance is not working, reporting the error on log i have posted before.
data-ciphers AES-128-GCM
data-ciphers-fallback AES-128-CBCIf i edit manually the .ovpn file, is Working ! My question is: what caused this and if it is a bug of the export tool. In that case, how i can export manually ?
-
I have notice that the VPN client export package version was different !
The latest one (1.5_4) adding this fallback AES line causing issues on Latest Windows 10 package. On legacy Windows package is ok !!!
How we can transfer this bug to developers ?
-
-
It's not a bug.
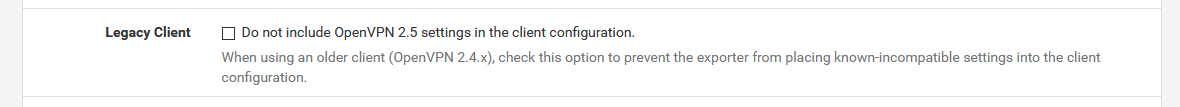
Option 1: Update your clients to OpenVPN 2.5.x
Option 2: Check the legacy box before exporting