Unable to redirect the gateway to another local IP in the OpenVPN
-
@really2002 said in Unable to redirect the gateway to another local IP in the OpenVPN:
for some reason, I have to set above, which will let all data in my home lan firstly go to 192.168.2.247, then the gateway server will handle these data and send them to the real gateway(192.168.2.248) to the internet
Very interested which reasons you have for doing this.
This is a bad setup. If you need to go over another gateway from your LAN and then go over pfSense, set up an additional network between the routers, maybe a VLAN, and diconnect pfSense from LAN.
But it won't work well if both are within the LAN. You will have asymmetric routing issues and some connections will fail.@really2002 said in Unable to redirect the gateway to another local IP in the OpenVPN:
BUT, how to set the gateway to 192.168.2.247?I need this function.
You can route the traffic to it by a policy routing rule on the OpenVPN instance interface. However, this only will work if you do masquerading on that router, otherwise you will also get an asymmetric routing problem.
-
@viragomann said in Unable to redirect the gateway to another local IP in the OpenVPN:
Very interested which reasons you have for doing this.
why? The reason is that I am in china, I can't visit some outside country's domains and IPs directly, I need to install a server in the 192.168.2.247 device, which will check the DNS and ip , if it is outside, the device will encrypt the data and pass through the 192.168.2.248 , finally send it to the proxy server in USA, and if it is inside ip, the device will direclty send it to 192.168.2.248 and let the pfsense handle it, which will be more quickly than the usa proxy.
-
@really2002 said in Unable to redirect the gateway to another local IP in the OpenVPN:
I need to install a server in the 192.168.2.247 device, which will check the DNS and ip , if it is outside, the device will encrypt the data and pass through the 192.168.2.248 , finally send it to the proxy server in USA
I see. So the device 192.168.2.247 does a sort of VPN or proxying. So the outbound of that device may logically be in another subnet or it does masqerading.
So yeah, this way it may work.However, it makes your setup complicated. Does this device anything you can't do on pfSense itself?
For GeoIP filtering you can use the pfBlockerNG package. For instance it can generate an alias for China networks, so you can use this for policy routing.@really2002 said in Unable to redirect the gateway to another local IP in the OpenVPN:
BUT, how to set the gateway to 192.168.2.247?I need this function.
Or the openvpn can not have the function to set the gateway to another local ip in the home lan? the gateway must be itself?Yes, the gateway for the VPN clients has to be the VPN server. However, as mentioned above you can do policy routing on pfSense to direct the traffic to your gateway.
To do so you have to add 192.168.2.247 as gateway to pfSense in System > Routing > Gateways.
Then edit the firewall rule(s) allowing the upstream traffic from the OpenVPN client, expand the advanced options, go down to Gateway and select the 192.168.2.247.
Now pfSense directs any traffic from the clients to this gateway.
However, consider that you may need additonal firewall rules for local access like DNS. -
@viragomann said in Unable to redirect the gateway to another local IP in the OpenVPN:
I see. So the device 192.168.2.247 does a sort of VPN or proxying. So the outbound of that device may logically be in another subnet or it does masqerading.
So yeah, this way it may work.Yes, similiar, it is a kind of proxy or VPN, it use SSR/V2ray/Torjan to connect the certain VPS, so I can visit the ips I want by these vps.
and I think pfsense can not do this work.
I resolve the above problem by install another pfsense (192.168.2.246)special for openVPN in the home lan, and in this pfsense, I only set 1 interface(wan), and I set upstream gateway 192.168.2.247 and DNS 192.168.2.247 in the gernal setup. In the main pfsense router(192.168.2.248), I pass through the openvpn data(1194) on the wan. It can work. However , I still want to cut down this 1 port pfsense and i try to use the main pfsense to redirect to 192.168.2.247
-
@viragomann said in Unable to redirect the gateway to another local IP in the OpenVPN:
Yes, the gateway for the VPN clients has to be the VPN server. However, as mentioned above you can do policy routing on pfSense to direct the traffic to your gateway.
To do so you have to add 192.168.2.247 as gateway to pfSense in System > Routing > Gateways.
Then edit the firewall rule(s) allowing the upstream traffic from the OpenVPN client, expand the advanced options, go down to Gateway and select the 192.168.2.247.
Now pfSense directs any traffic from the clients to this gateway.I tried, in the system >routing , I can't add the gateway on the WAN to 192.168.2.247 . I can only add this IP on the LAN.
in th rule of firewall, WAN interface, I modify the 1194 data(generated by vpn wizard), and add the gateway 192.168.2.247. no use.
in th rule of firewall, openvpn interface, I modify the . data(generated by vpn wizard), and add the gateway 192.168.2.247. no use.
-
@really2002 said in Unable to redirect the gateway to another local IP in the OpenVPN:
I tried, in the system >routing , I can't add the gateway on the WAN to 192.168.2.247 . I can only add this IP on the LAN.
That's as expected, since 192.168.2.247 is connected to LAN.
@really2002 said in Unable to redirect the gateway to another local IP in the OpenVPN:
in th rule of firewall, WAN interface, I modify the 1194 data(generated by vpn wizard), and add the gateway 192.168.2.247. no use.
in th rule of firewall, openvpn interface, I modify the . data(generated by vpn wizard), and add the gateway 192.168.2.247. no use.The second one should do the job. The first just allows the OpenVPN clients to connect.
It should direct the tunnel traffic coming in from the client to the stated gateway.
You may also need a static route on the gateway for the VPN tunnel network pointing to pfSense LAN IP to direct the response traffic back to pfSense. -
If you want a downstream router to do vpn or not, it needs to be connected to pfsense via a transit network. Or as already mentioned your going to have a asymmetrical problem.
Please draw up what your trying to accomplish. But a downstream router be it does vpn or not needs to be connected via a transit..
If you have some client on our local lan that you want to push out a vpn client connection that is on pfsense - then that is a simple policy route.
BUT, how to set the gateway to 192.168.2.247?I need this function.
So want a vpn client of pfsense, to connect to the vpn of pfsense. And then route out some downstream vpn client server?
So you want this?
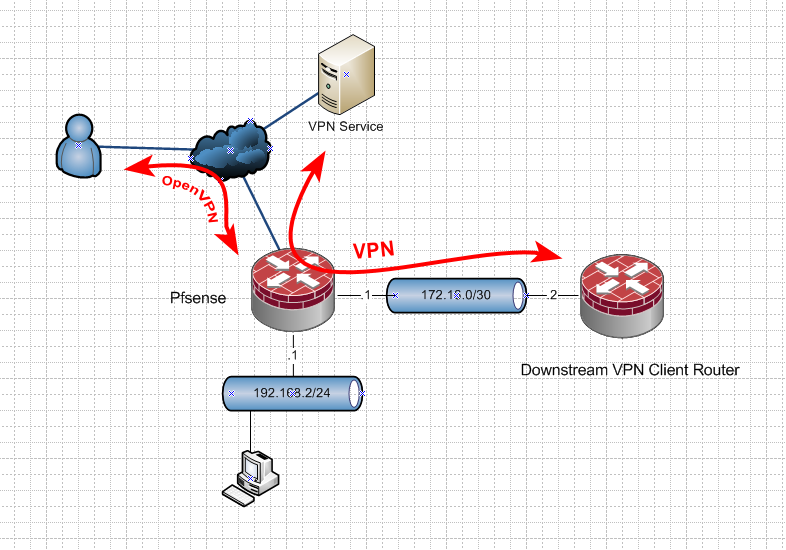
And then you want the openvpn client out on the internet to connect to pfsense vpn, and then be routed out your downstream vpn client server?
Like this - the green arrows.
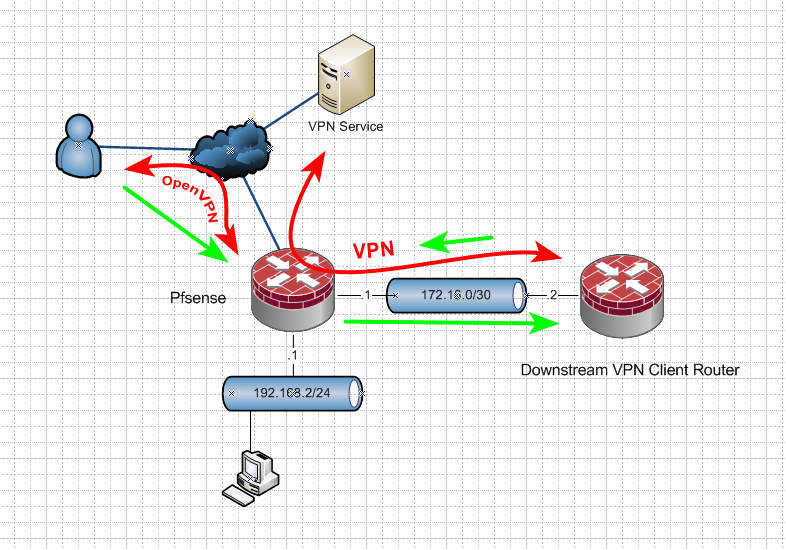
Is that what your trying to accomplish?
-
thanks for mention,I have to set my local net work as below:
when I use my pc in home lan
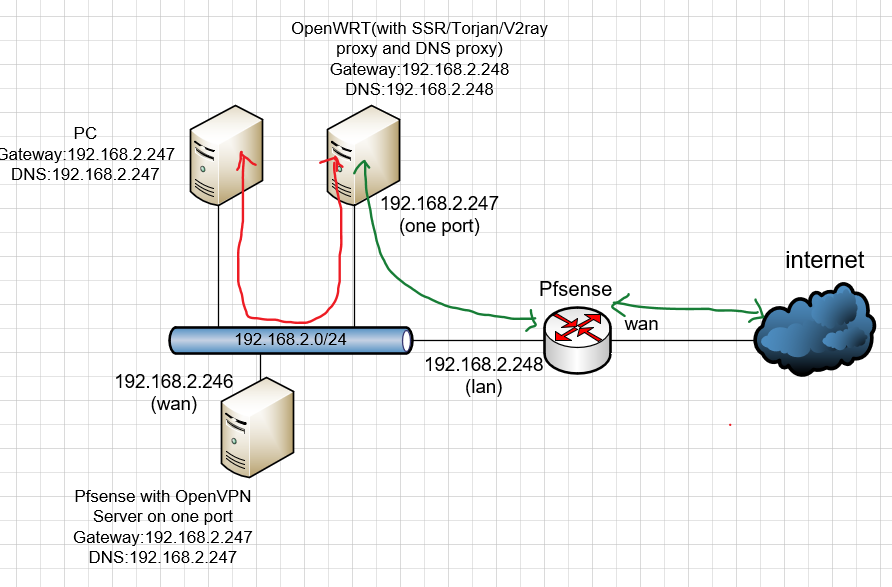
and when I remote access when using openVPN
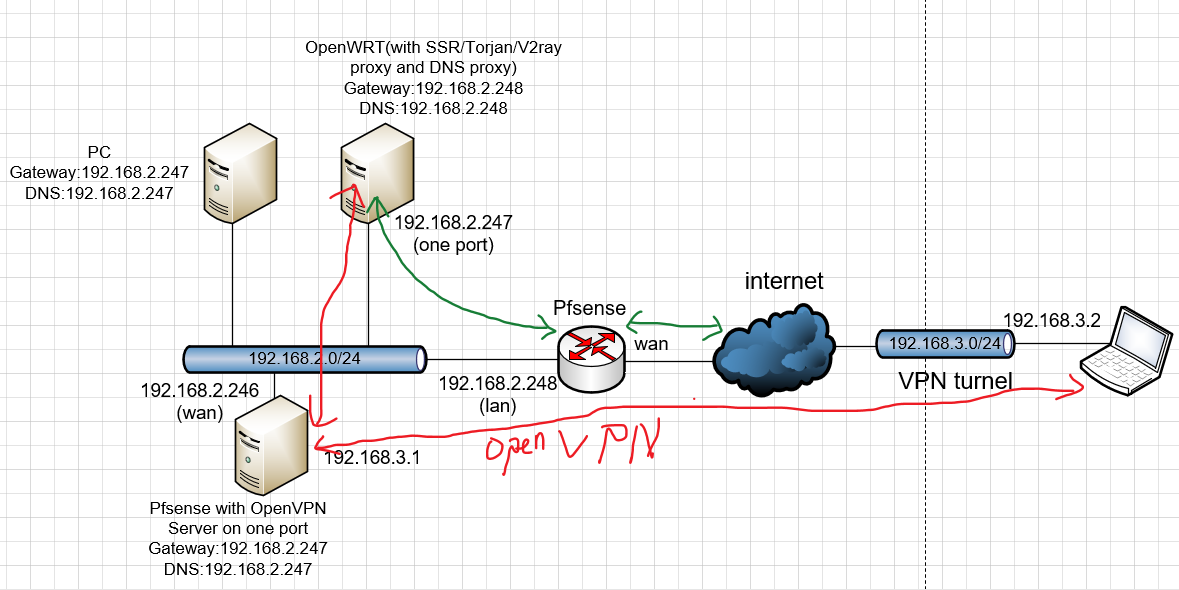
above is OK, and I am usig now.
but,I want to delete the openvpn device in the local lan, and let my main pfsense router do this. My ideal network is below:
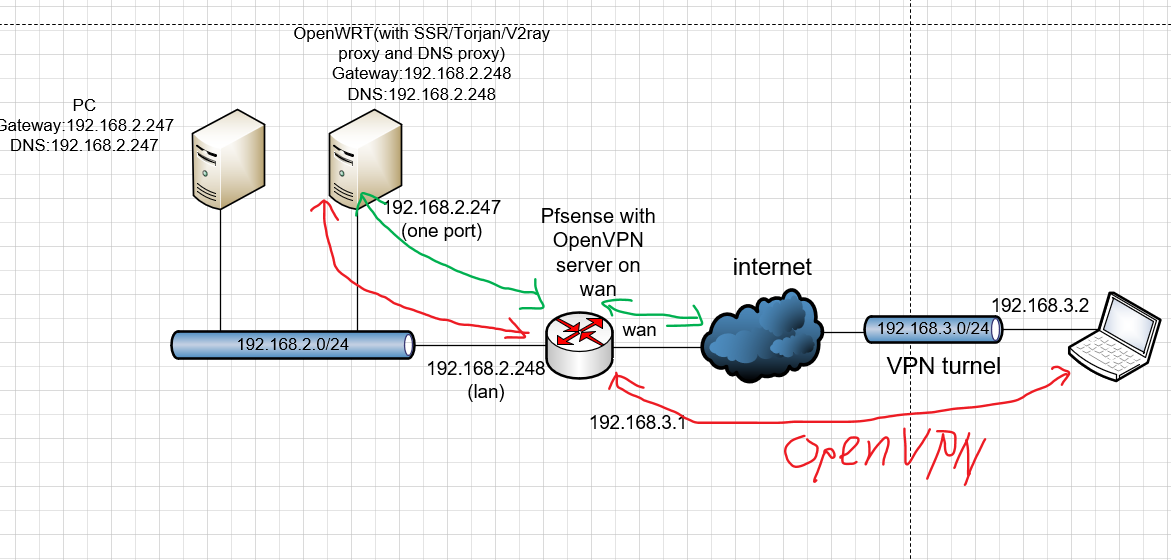
I still dont know how to do this. and still not success
-
@really2002 said in Unable to redirect the gateway to another local IP in the OpenVPN:
I still dont know how to do this. and still not success
Because your trying to run an asymmetrical mess!!
And yeah your going to have a bad day trying to do such a setup.
Connect this openwrt box to pfsense via a transit network.. Doesn't matter if only has 1 interface or not. Also you could just set it up via a double nat as well, single interface can always just use vlans to run more then 1 network on the single interface.
-
My question and problem is when i remote access on the openvpn server on the main router(the third pic), it can not re-direct the data to 192.168.2.247 , the data seems directly go out to the wan, I want to data go through 192.168.2.247 and then go out to wan.
-
Well if you would set it up correctly you would just setup a policy route pointing to the downstream router. Via creating a gateway..
-
and another thing I am always curious, when pfsens downlaod the pakages , the pfblockerNG's rule and snort's rule , what original ip does it use? the ip on the wan, or the ip on the lan?
-
How would it use the IP on the lan? That is a rfc1918 address is not?
Pfsense would use the IP connected to the network it uses to talk to whatever the destination IP is.. Normally that would be your wan IP.
If you have pfsense setup to use a vpn as its default, then it would use its vpn IP..
The IP used would be the of the interface connected to the network the gateway is on, based upon the routing table.
-
Hi everyone,
I hope someone can help with an issue we're facing in our network setup. Here's an overview of our topology:
Edge of the network: A pfSense firewall with an IP address of 10.10.10.1/24.
VPN server: Another device in the network acting as a VPN server with the IP address 10.10.10.2/24.
Gateway distribution: Some of our clients use 10.10.10.1 (pfSense) as their gateway, while others use 10.10.10.2 (VPN server).
Additional details:
We have also set up OpenVPN on the pfSense firewall. The OpenVPN clients are assigned the subnet 10.10.11.0/24.
The second VPN server (10.10.10.2) is configured as a tunnel between two locations: one in our company and the other in Canada.
The goal is to route some traffic through the pfSense OpenVPN and other traffic through the VPN tunnel to the remote server in Canada.
Problem description:
Internally, everything works fine within the network. Clients and peripherals communicate without issues.
The OpenVPN clients (10.10.11.0/24) can successfully access devices and peripherals in the network that use 10.10.10.1 (pfSense) as their gateway.
The issue: OpenVPN clients cannot access devices and peripherals in the network that use 10.10.10.2 (VPN server) as their gateway.
What we need:
We want to configure the network so that OpenVPN clients can access devices on both gateways (10.10.10.1 and 10.10.10.2).
We also want to route some traffic through the pfSense and other traffic through the VPN tunnel to Canada.
Has anyone encountered this issue before? Any advice or configuration tips would be much appreciated!Thank you in advance!
-
@delphi5
Why didn't you open a new topic for your issue?Regarding your issue, why don't you run the peer to peer server on pfSense? You can run multiple OpenVPN servers for different purposes and as well clients concurrently.
Gateway distribution: Some of our clients use 10.10.10.1 (pfSense) as their gateway, while others use 10.10.10.2 (VPN server).
The second VPN server (10.10.10.2) is configured as a tunnel between two locations: one in our company and the other in Canada.Why are the local clients configured to use the second server as default gateway at all?
Just add static routes to them for the remote network.However, more reliable if you want to run this connection on a different server, would be to put it in a different network segment than LAN and route the traffic on pfSense. So all local devices could use pfSense as default gateway.