OpenVPN Site-To-Site VPN Routing/NAT?
-
Hello,
i have researched a lot and does not found an answer.
My Setup is like this:
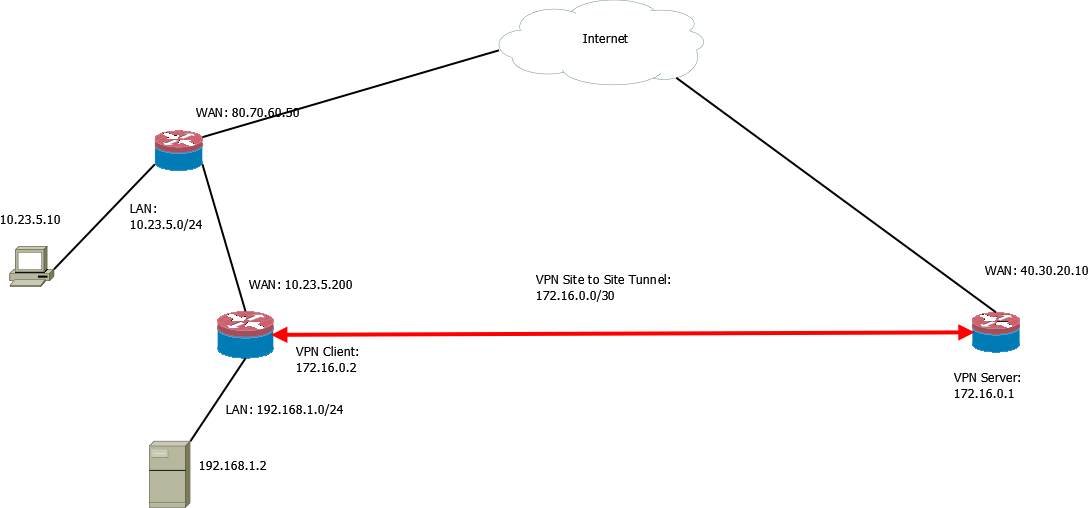
Lets call the VPN Client (172.16.0.2) Site A and the VPN Server (172.16.0.1) Site B.
Both Routers are PfSense instances.
I have established a Site-to-Site VPN connection between them with OpenVPN.
Site A shares the LAN Network through the tunnel, which is accessable via ICMP Pings and ICMP Traceroutes from Site B. (Ping 192.168.1.2 works fine)
Now there is the tricky part.
I want to access the Server at Site A (192.168.1.2) from the Site B with a HAProxy.Because of the static route at Site B pointing at Site As LAN network, i thought the HAProxy resolves this correctly.
I know the Setup with the pfSense inside a LAN Network covered by a FritzBox is not the best start, but i thought due to OpenVPN Client i dont have to route traffic or open ports to establish the direct connection. My point is that i want to hide my private home IP address and access the local server inside the LAN from the WAN at Site B. (Only for traffic from the internet)
Ive read that it is something with outbound NAT to ensure the response from the Server uses the VPN as gateway, but after a lot of "search, try and error" i hope you could help me.
For additional information a ping from 192.168.1.2 to 172.16.0.1 works fine.
-
@kingstoffen
Not completely clear what you want to do here. Let me recap.
On pfSense at B there is a HAProxy running and you want to direct incoming connections from WAN through it to the server behind the remote endpoint. Right?Is the A pfSense the default gateway on the server?
Did you assign an interface to the OpenVPN instance on A?
-
@viragomann
Yes, I want to direct incomming WAN connections at pfsense B through the tunnel to the server at LAN of pfsense site A.Interface configuration:
fritzbox A:
WAN dynamic ip
LAN 10.23.5.254/24 (GW of pfSense A)pfSense A:
WAN 10.23.5.200 (static) (gw)
LAN 192.168.1.1/24
VPNNIC 172.16.0.2/30 (OpenVPN Client)pfSense B:
WAN 40.30.20.10 (static) (gw)
VPNNIC 172.16.0.1/30 (OpenVPN Server)Server:
LAN 192.168.1.2
GW pfSense A 192.168.1.1A suspicious thing is this WAN firewall log at pfSense B:
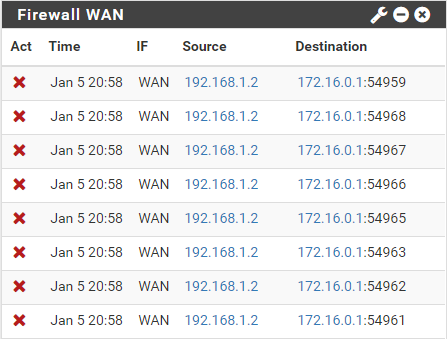
Because of the changing ports. I thought every OpenVPN tunnel connection uses the same port. This looks like dynamic ports.
-
@kingstoffen said in OpenVPN Site-To-Site VPN Routing/NAT?:
A suspicious thing is this WAN firewall log at pfSense B:
Please post the log from Status > System Logs > Firewall
Because of the changing ports. I thought every OpenVPN tunnel connection uses the same port. This looks like dynamic ports.
This is the servers IP behind the client trying to access the OpenVPN server. I suspect, these are response packets which are out of state for whatever reason.
@viragomann said in OpenVPN Site-To-Site VPN Routing/NAT?:
Is the A pfSense the default gateway on the server?

Did you assign an interface to the OpenVPN instance on A?

-
@viragomann
Okay the Firewall logs only include people sniffing at some Ports. IdkThe pfSenseA is the default gateway on the server.
The Gateway of pfSenseA is WAN, and the tunnel is established over WAN. (there is another router in front of the pfSenseA could this lead to problems? I thought the packets are routet through the established site to site connection)