OpenVPN gateway behaviors
-
I'm hoping someone can shed some light on this behavior, since I can't seem to find anything in the documentation on it. I know that TLS/SSL OpenVPN (site-to-site) behaves differently than shared key, but why do the gateways behave differently?
I have created two OpenVPN servers on one pfsense box, and two OpenVPN clients on another pfsense box. They are configured with the same encryption, route, and gateway parameters, except one is SSL/TLS OpenVPN and the other is shared key. I have created the VPN interfaces on both servers and both clients, and enabled the firewall rules on both servers and both clients.
Why does the shared key gateway get a "dynamic" gateway and the certificate based VPN gets assigned an address and the gateway comes online?
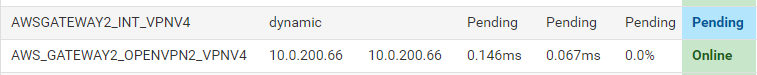
Certificate based OpenVPN is Online, whereas the shared key version is Pending
This has been happening whether I configure the OpenVPN server tunnel network as a /30 network or anything larger than that.
I would like to be able to use the shared key VPN for it's simplicity with two firewalls, but the lack of gateway monitoring is just not good for routing and rules.
Thank you.
-
@meaglerick
I suspect you're missing the Tunnel Network setting on the client. Use a /30 mask and enter the network on both sites. -
@viragomann Ok, I tried adding the tunnel network on the client VPN device, using both a /29, and a /30, and now the gateway shows up and configures itself. Question now is...why do I not have to configure the tunnel network on the SSL/TLS based VPN client, but on the shared key version, I do? I was under the impression they operated very similarly.
Thank you.
-
@meaglerick
I think, that is the wrong place to ask this. Possibly you have luck in the OpenVPN community forum.We are just following here the guides provided by Netgate:
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-psk.html
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html