OpenVPN & another pfsense
-
Hi all,
I configured a S2S with OpenVPN apparently with no issue. I can ping and reach the remote lan assuming I added the route to the clients (I do not want to have a single route on the gateway for all the remote client) from OpenVPN server address.The ONLY client I cannot ping or reach is another pfsense (WAN) address on the same lan.
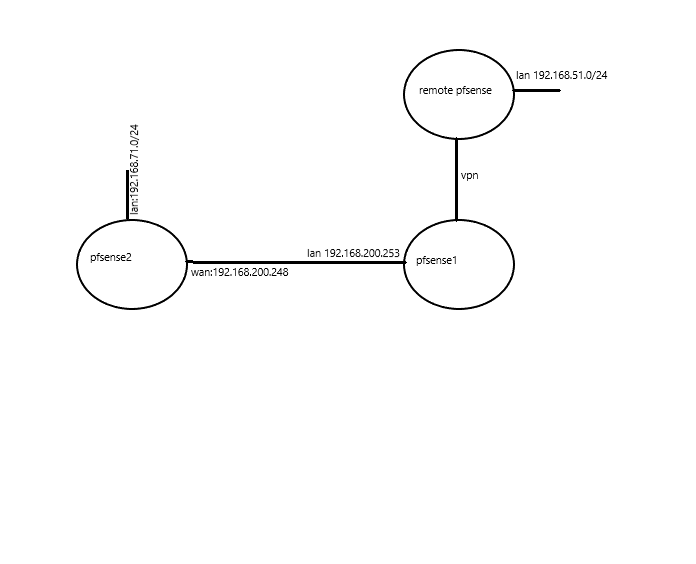
Here my diagram- pfsense1 with OpenVPN S2S server (LAN: 192.168.200.253)
- pfsense2 (WAN 192.168.200.248)
They can ping each other with no problem.
Moreover I can ping from pfsense2 OpenVPN-server interface every ip on the lan when I add the proper routing rule, for example:
PING 192.168.200.11 (192.168.200.11) from 10.3.110.1: 56 data bytes
64 bytes from 192.168.200.11: icmp_seq=0 ttl=64 time=0.302 ms
64 bytes from 192.168.200.11: icmp_seq=1 ttl=64 time=0.490 ms
64 bytes from 192.168.200.11: icmp_seq=2 ttl=64 time=0.252 ms
--- 192.168.200.11 ping statistics ---
3 packets transmitted, 3 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 0.252/0.348/0.490/0.102 msI cannot ping the WAN interface of pfsense2 or test its port and I cannot see any firewall blocking log:
PING 192.168.200.248 (192.168.200.248) from 10.3.110.1: 56 data bytes--- 192.168.200.248 ping statistics ---
3 packets transmitted, 0 packets received, 100.0% packet lossI added two floating firewall out rules to pfsense2 so I can successfully reach the remote lan connected to openvpn (192.168.51.0/24) and the second rule for tunnel network, just for testing purposes.
But the WAN interface of pfsense1 is still unreachable from OpenVPN interface of pfsense2.And here when I enable the packet capture during the failing ping:
18:20:28.977845 IP 10.3.110.1 > 192.168.200.248: ICMP echo request, id 47641, seq 0, length 64
18:20:28.977980 IP 192.168.200.248 > 10.3.110.1: ICMP echo reply, id 47641, seq 0, length 64
18:20:29.988986 IP 10.3.110.1 > 192.168.200.248: ICMP echo request, id 47641, seq 1, length 64
18:20:29.989050 IP 192.168.200.248 > 10.3.110.1: ICMP echo reply, id 47641, seq 1, length 64
18:20:31.008424 IP 10.3.110.1 > 192.168.200.248: ICMP echo request, id 47641, seq 2, length 64
18:20:31.008514 IP 192.168.200.248 > 10.3.110.1: ICMP echo reply, id 47641, seq 2, length 64
18:20:32.019548 IP 10.3.110.1 > 192.168.200.248: ICMP echo request, id 47641, seq 3, length 64
18:20:32.019648 IP 192.168.200.248 > 10.3.110.1: ICMP echo reply, id 47641, seq 3, length 64
...Any help would be very appreciated.
Thanks
-
I manage in solving my issue.
here is my diagram:
I needed mainly two settings:- on pfsense2 I had to check "Bypass firewall rules for traffic on the same interface" option otherwise my WAN routing rules were ignored;
2, defining a NAT outboud rule on pfsense1:
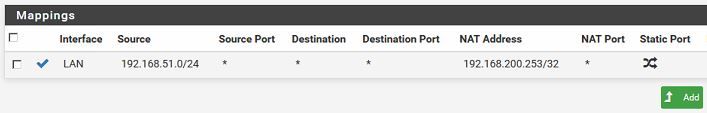
The unwanted aftermath was that the whole traffic between the networks was allowed and I had to design some extra block rulesets to allow only what I really need. But in the end nothing hard.
Now everything works nice and fast!
- on pfsense2 I had to check "Bypass firewall rules for traffic on the same interface" option otherwise my WAN routing rules were ignored;