Unexpected behaviour with multinet
-
Let me preface this with... I'm not working on anything mission critical and I am purely using a home lab for learning/general interest networking etc, I am in no way an IT professional just a hobbyist. I don't expect or demand any support, I'm just curious as to why I have this outcome.
It seems that traffic from a secondary subnet in a multinet environment is able to cross the firewall to WAN without any explicit rule allowing it to.
I have an OpenVPN Access Server appliance running on my hypervisor and originally had it set up in the default NAT mode for traversing the OpenVPN client subnet to my private subnet. I was curious about setting up routing mode instead of NAT. I know many do not recommend multinet setups but my thinking is... technically it should work, it's just bad practice, lets see what happens.
Private subnet 192.168.1.0/24 (LAN interface on pfSense)
OpenVPN AS clients subnet 172.27.224.0/20
OpenVPN AS address on Private Subnet 192.168.1.253I followed the guidance on changing from NAT to Routing here:
https://openvpn.net/vpn-server-resources/reach-openvpn-clients-directly-from-a-private-network/
Now for the pfSense bit:
I set up a Gateway on the LAN interface pointing to 192.168.1.253 and a static route to 172.27.224.0/20 using said gateway. Since my outbound NAT is set to hybrid mode, an automatic NAT rule was created letting the 172.27.224.0/20 subnet leave WAN.

At this point I have not set up any rule to allow the 172.27.224.0/20 subnet entering the LAN interface to go anywhere, but I was able to access the internet from it??? This I was not expecting.

I thought this might have something to do with the automatic rule on outbound NAT but as I understand it, outbound NAT is only controlling how traffic leaves an interface and not whether or not it should get there in the first place.
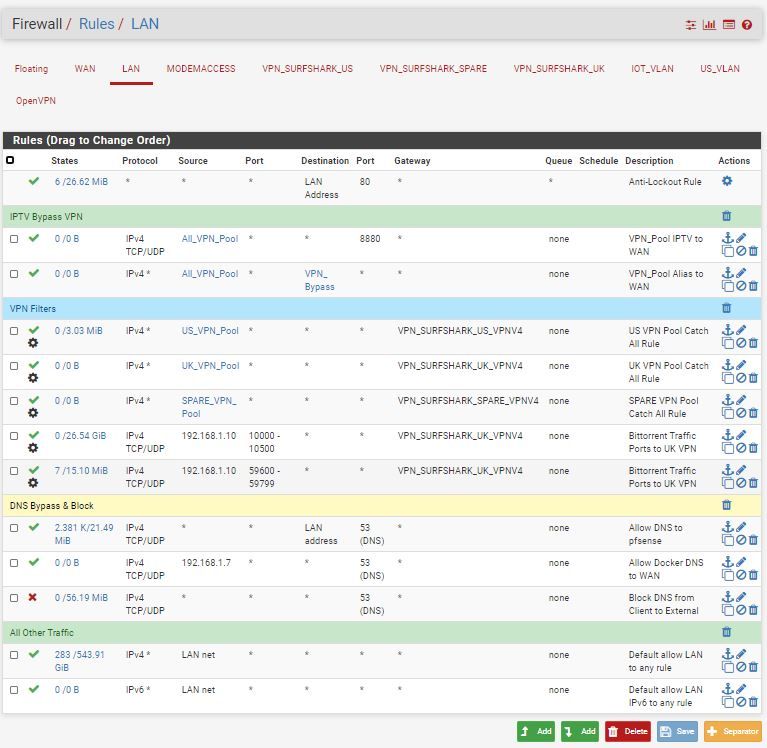
I have also carefully considered all my LAN firewall rules (top down approach) and I can't see any one that would match the traffic and let it through. The bottom "allow all" rules are set to match traffic from source "LAN net" which I assume looks for the LAN subnet 192.168.1.0/24 traffic.
I cannot access any other interfaces without changing this last rule to source "any", which is what I would expect to see.I just don't understand how the 172.27.224.0/20 subnet is managing to get to WAN without a pass rule allowing it.
Can anyone point me in the right direction?
-
pfSense utilizes default deny on the WAN / OPT1 /OPT2 etc etc and default allow on the LAN
the default is that everything out to the Internet from the LAN is permitted
https://docs.netgate.com/pfsense/en/latest/firewall/best-practices.html -
@cabarnacus said in Unexpected behaviour with multinet:
I set up a Gateway on the LAN interface pointing to 192.168.1.253 and a static route to 172.27.224.0/20 using said gateway.
Huh?? You have a downstream router? Doing nat?
Your going to have to layout your network if you want help... Have no idea what your doing.. And sure not going to spend time reading some shit guide on how to do X.. When for all we know you did Y and not what was in the guide at all.
Posting of your rules on lan is a good start.. But we have no idea what are in your aliases you have listed.. And seems you have downstream networks? So your lan is a transit? Can lead to asymmetrical problems, unless this downstream is natting? etc. etc..
-
@kiokoman Perfect, that's the simple explanation I was looking for and explains the behaviour. Thanks.
-
@johnpoz A warm and friendly reply as usual
 . It's been answered to my satisfaction now but I appreciate the reply, I won't bore you with the details of my network layout. Thanks anyway.
. It's been answered to my satisfaction now but I appreciate the reply, I won't bore you with the details of my network layout. Thanks anyway.