IOT VLAN Firewall Rules Feedback
-
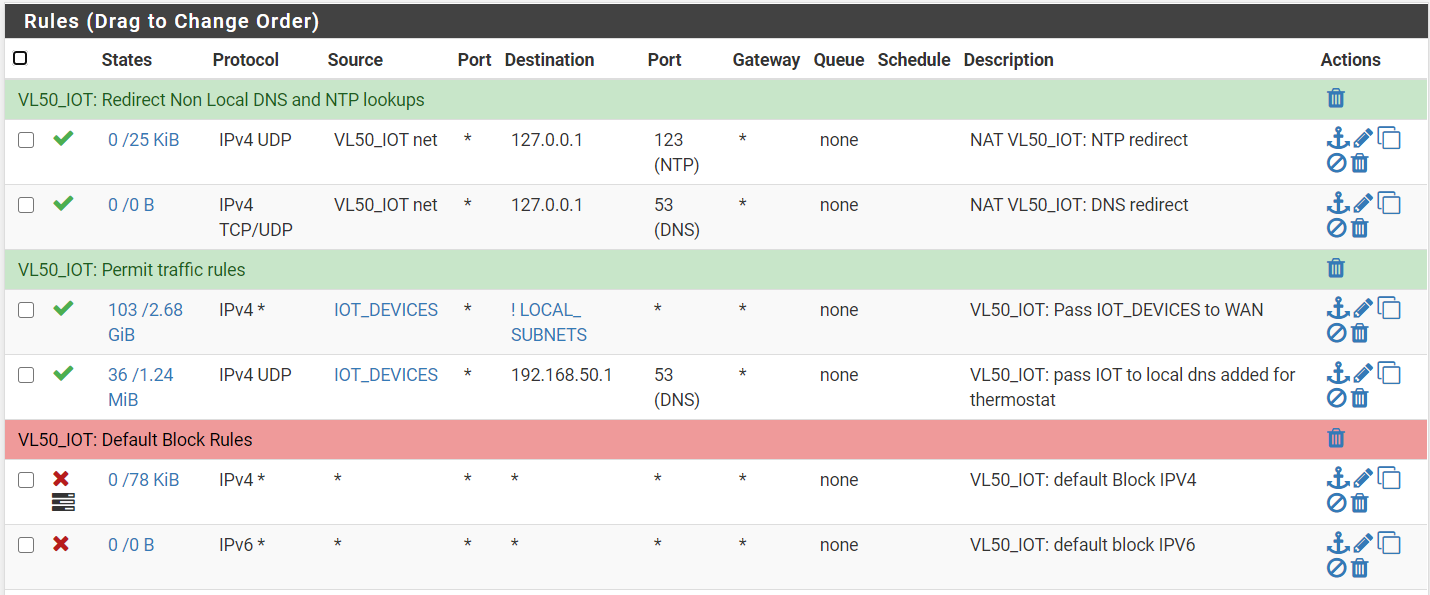
I'm new to router setup and learning as much as possible. Looking for some input on my IOT VLAN firewall rules. I have a honeywell smart thermostat, and I was not able to change the temperature, it would connect but the request would not go through. I checked the firewall logs and it was blocking a request from my thermostat IP to the IOT VLAN DNS PORT 53, using the "Easy Rule" addition from the logs I added a new rule which you can see here labeled pass IOT to local dns added for thermostat and now it works as I expect it to.
Two questions. First is this a safe setup for my an IOT specific VLAN? Is this new rule I've added done anything to compromise this VLAN?
Second question is why is this specific rule required to update the thermostat? Shouldn't the DNS redirect Rule cover what was being blocked?
Appreciate any feedback.
-
The DNS redirect Rule has shows 0/0B under states. Does not look like anything is matching that rule at all.
On the NAT-Port Forward page what does your DNS redirect rule look like?
-
Thanks @hieroglyph, the dns redirect now shows some activity
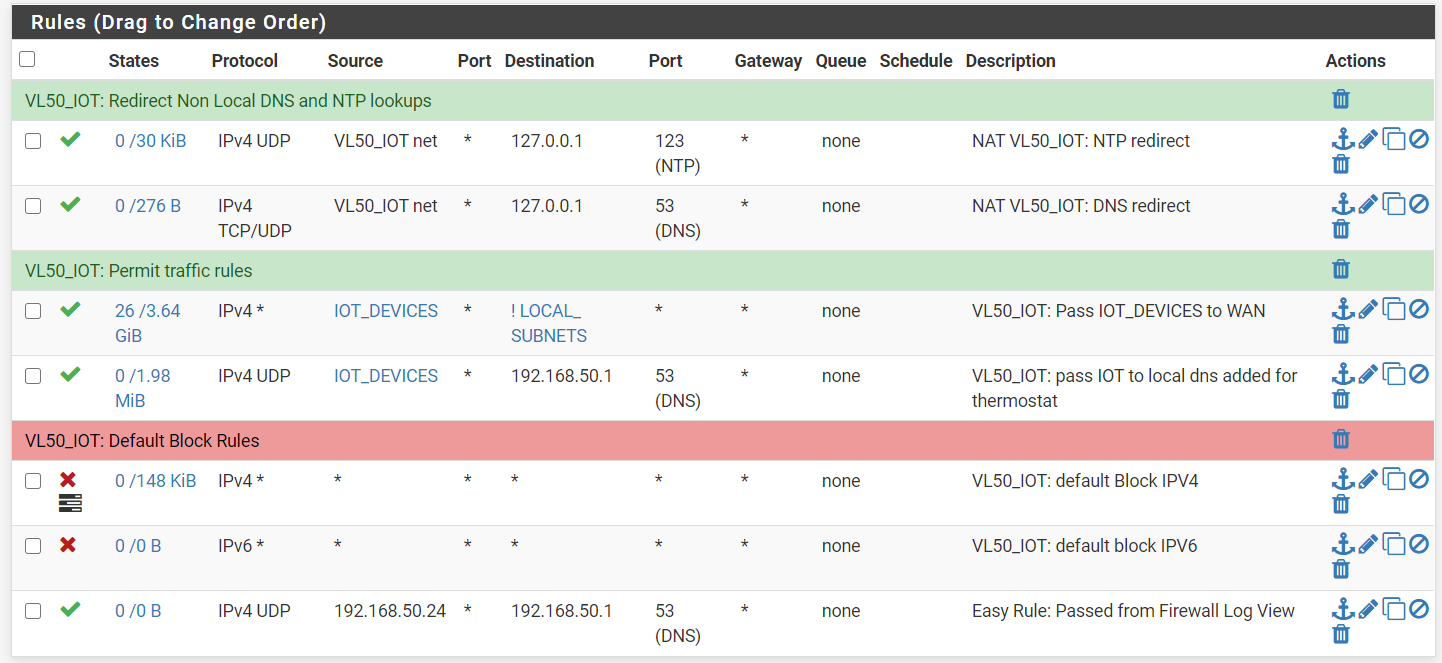
here is the detailed information on the nat port forward page
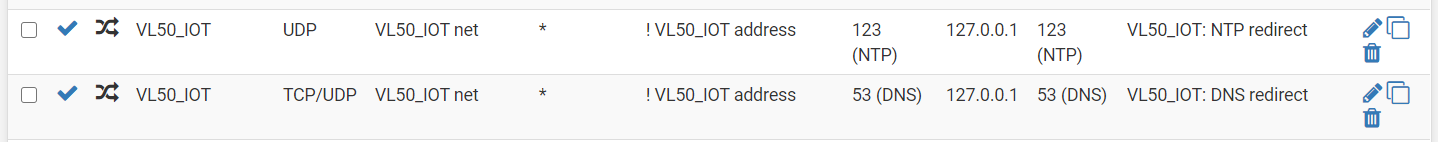
mostly was looking for validation that my newly added rule didn't introduce any vulnerabilities.
-
Your rules do not seem to compromise anything. Devices in the IOT_DEVICES alias can reach the internet and not anything local.
The way it is setup now, only devices who are originally not sending DNS and NTP requests to the router will be redirected back to the router. For instance if a device in the IOT_DEVICES alias is sending a DNS request to 192.168.50.1 the DNS NAT redirect will not match it. Because the redirect is looking for DNS requests not sent to 192.168.50.1.
You need a regular firewall rule above or below "NAT VL50_IOT:DNS redirect" that allows DNS requests from the VL50_IOT net, destined to 192.168.50.1 (or This_Firewall) to pass. Do the same for the "NAT VL50_IOT: NTP redirect" rule.
Example:
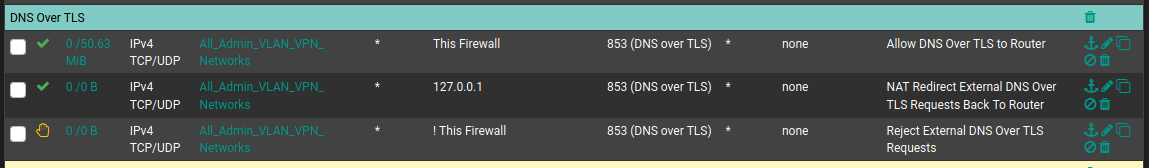
-
Thanks again @hieroglyph . I've added rules for both NTP and DNS for This_Firewall destination. Appreciate the feedback.