Cant access Client Lan
-
Hello i hope someone can help me with my problem.
I have pfSense running on a vserver in the cloud. The Firewall should work as a VPN entry point to bypass my DSLite connection at home and let me access my home appliances.
I followed the OpenVPN wizard on the firewall. Exported a client and used the client config on an Unraid server at home.
My home network ist running at 10.11.12.0/24
The VPN Tunnel Network 10.0.8.0
I added a virtual LAN Interface to pfSense at 10.10.10.0/24
This way i was able to set the vpn nic as opt1 on the interface tab. otherwise i could not set any static routes.Now the problem:
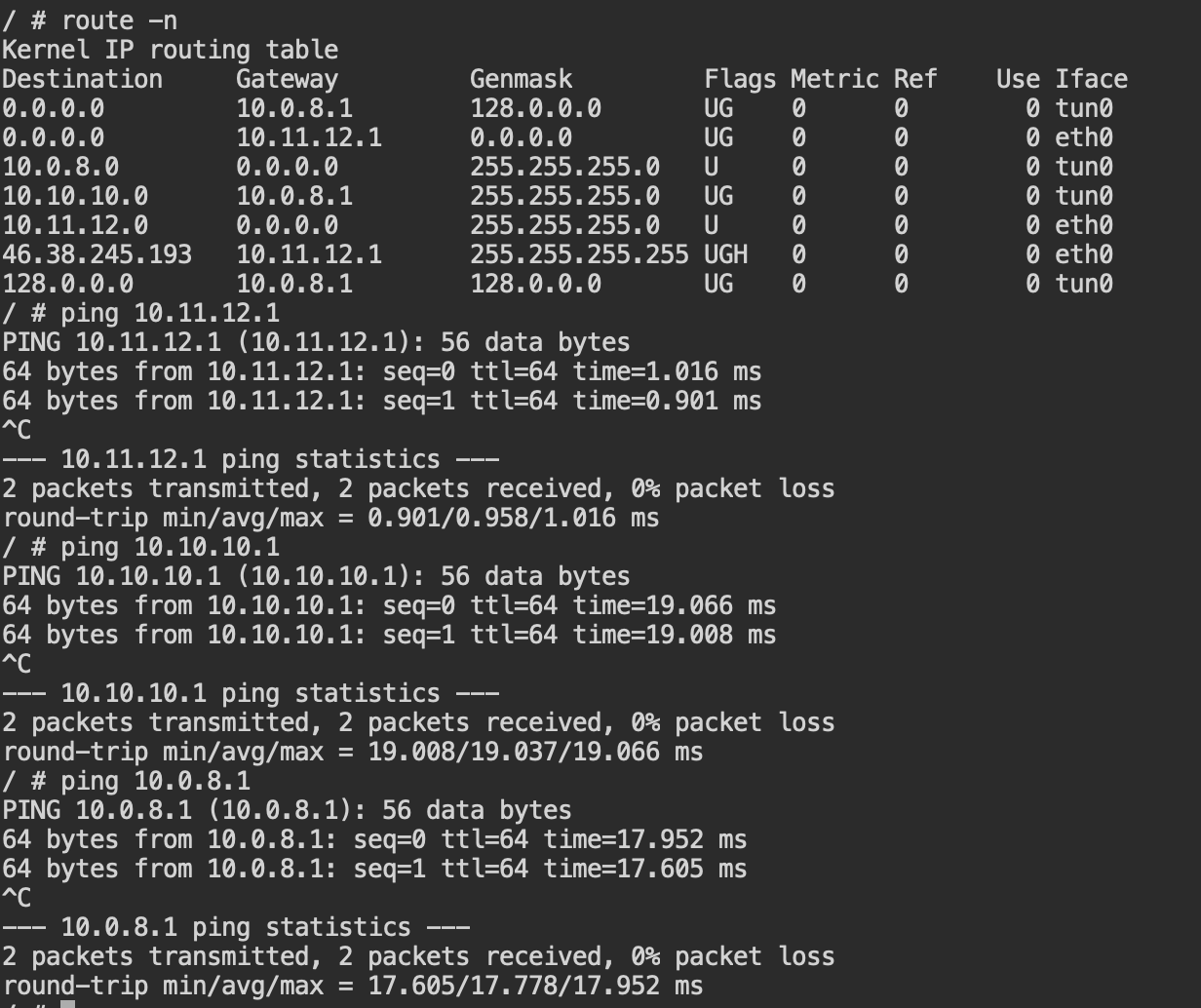
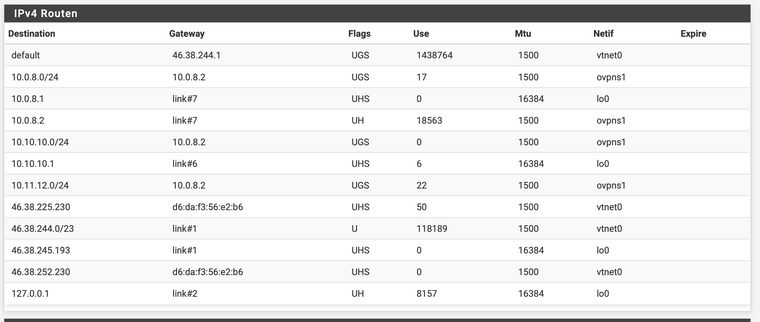
I cant ping from pfSense to my home LAN. Neither can i access my home LAN from another VPN Client on my phone.
BUT i can ping my home appliances, the tunnel interface on the pfSense and the LAN Interface on the pfSense.Screenshot from the client side:
Routes on pfSense:
What am i missing?
-
@dex said in Cant access Client Lan:
Exported a client and used the client config on an Unraid server at home.
You should run the VPN on your home router / default gateway. Don't know what function the Unraid has in you network.
This way i was able to set the vpn nic as opt1 on the interface tab. otherwise i could not set any static routes.
You should not add static routes for device behind a VPN. This should be done by OpenVPN itself by adding your home local networks to the remote networks in the OpenVPN settings.
-
@viragomann my home router cant act as an openvpn client (fritzbox 7590)
the static routes are a result of my 2 day long testing.. there is no difference when i push the routes through the openvpn config
-
Agreed. A site-to-site tunnel between the two edge firewalls would be the best way to address this.
OP, what you're trying to do will technically work but has some requirements, needs extra steps to get it working, and is far from ideal. To make your current setup work... first, the client device needs to have routing enabled and be able to route traffic. Second, PFsense needs to know both what network(s) exist behind the client and how to get there. Third, you have to add a route to the edge firewall on the client-side so devices behind the client know how to reach the network behind PFsense.
-
@marvosa the client has enabled ip forwarding. routing tables on both sides look fine for me too. the client can ping the whole setup. there must be one little checkbox im missing that stops pfSense from routing to the client network.
-
@dex
Yeah, the routes to your home LAN my work, but it is not ideal to set static routes. Instead you should use the Remote Networks box in OpenVPN.However, so the request packets destined to your LAN are directed over the VPN and may reach the LAN devices, but latter will send responses to their default gateway, but not back to Unraid. That's why the default gateway should be the VPN endpoint at all.
If you want to get it work this way, you need to do masquerading on the Unraid on packets destined to your home LAN, so that it translate the source addresses in packets going to LAN devices into its LAN address. Only this ensures that responses are coming back.