OVPNS1 + LAN->WAN Blocked Firewall Rules
-
Hi all,
I am new to pfSense, and am a little confused by some of the blocked log entries on my dashboard. There are two instances I am not sure about, and was hoping someone could help me to clear it up!
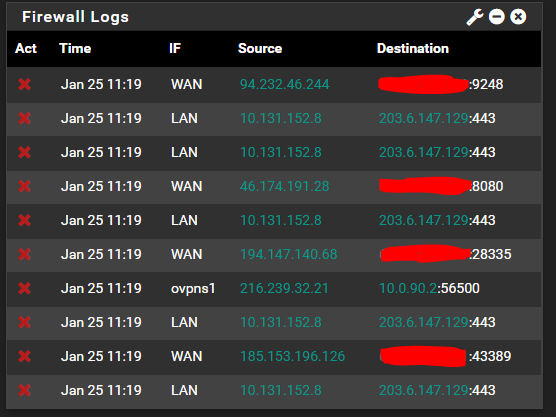
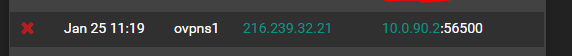
Firstly, I have set up an openvpn server, and it works with my phone no worries at all. However I noticed an interesting blocked entry that is seemingly related...
The log entry on the 'ovpns1' interface, is originating from an IP address in the US (I am in AU). Does this mean that a random IP has scanned/attempted to authenticate with the VPN server? The part that confuses me, is that the Destination IP is within the range that the VPN is specified to allocate. How can someone on WAN specify a LAN IP?Secondly, There are a lot of odd blocked entries going from LAN to WAN. This is confusing me because my LAN range is 10.0.0.0/16, so how can there be an IP in my LAN outside of that range? I have checked the DHCP leases table, and there are no corresponding entries. I am also confused as to why it was blocked, when I have no custom rules in the my LAN firewall (just the three standard ones - anti-lockout + allow all ipv4 + allow all ipv6)
Any guidance on the above would be greatly appreciated.
I'm loving pfsense so far - I don't know why I didn't ditch the old consumer router years ago!!!
Thank you! :)
-
Without information about how your VPN is setup, your WAN rules, and your ovpns rules; it will be hard for anyone to help.
-
@hieroglyph Thanks for the reply :)
Fair point! At the time of posting, I essentially had a basic, vanilla installation of the latest version of pfSense. This log was captured with no firewall rules configured, with the exception of the default pfSense (including RFC1918, Bogon & anti-lockout) & OpenVPN rules.
I have since added in a few rules for pfBlockerNG + Forced DNS + Port Forwading, however this behaviour was observed before those changes, and still continues. (to help give context to some of the following screenshots!)
The OpenVPN server is pretty much a cookie-cutter setup:
OpenVPN Server:
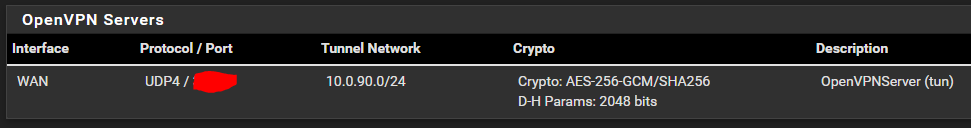
Firewall (WAN Interface):
Firewall (OpenVPN Interface):
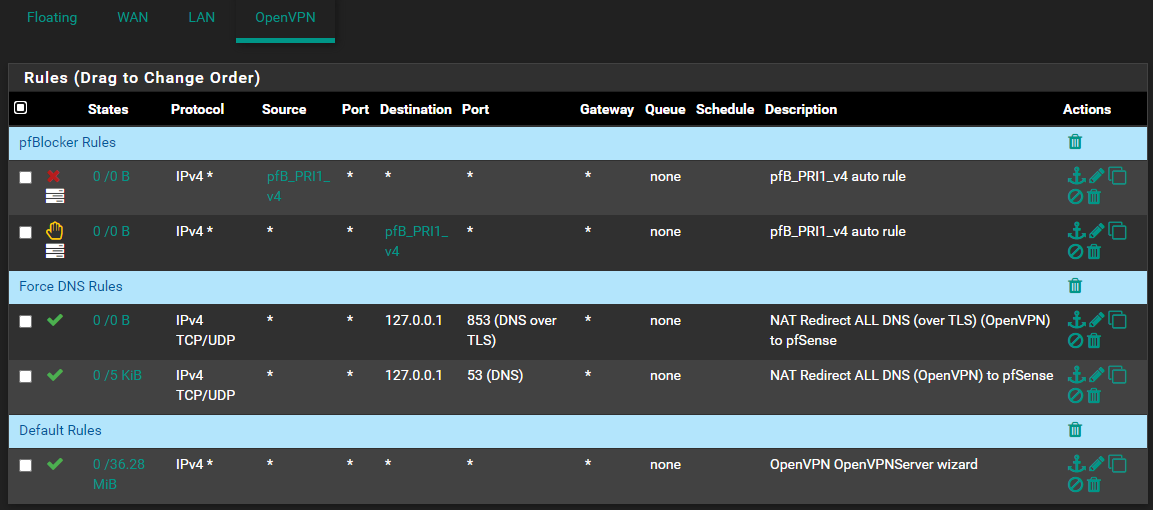
Note: There are no floating rules
-
What I do'nt understand : "ovpns1" is not something that can be listed as an interface.
The 'global' OpenVPN server interface is called : "OpenVPN" and you have that one.The config of my OpenVPN server is also called "ovpns1", and I had a look at my remote syslog server : I'm using OpenVPN a lot, but could find a reference within a firewall sys log message.
Some how this "ovpns1" being used in the wrong place ( ?) is part of your issue.Hover the mouse over red cross, you'll see a number.
Like
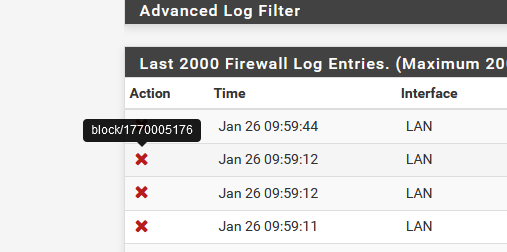
Note this number "1770005176". Now get the "list with firewall rules" to find the rule that is blocking.
You can't use the GUI firewall page now. Use the list with all the rules : it's here /tmp/rules.debug These are the actual firewall rules. -
@theskelly Give this a try...
On the Interfaces > Assignments page, is there an added/saved entry for your VPN server? It would have the name you gave it in the Interface column and say "ovpns1 (OpenVPNServer)" in the Network Port drop down menu?
It would look like this, except with the name you gave it:
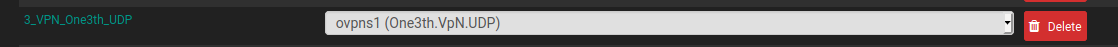
Trying adding that interface if it does not exist. Then name and save it as shown below:
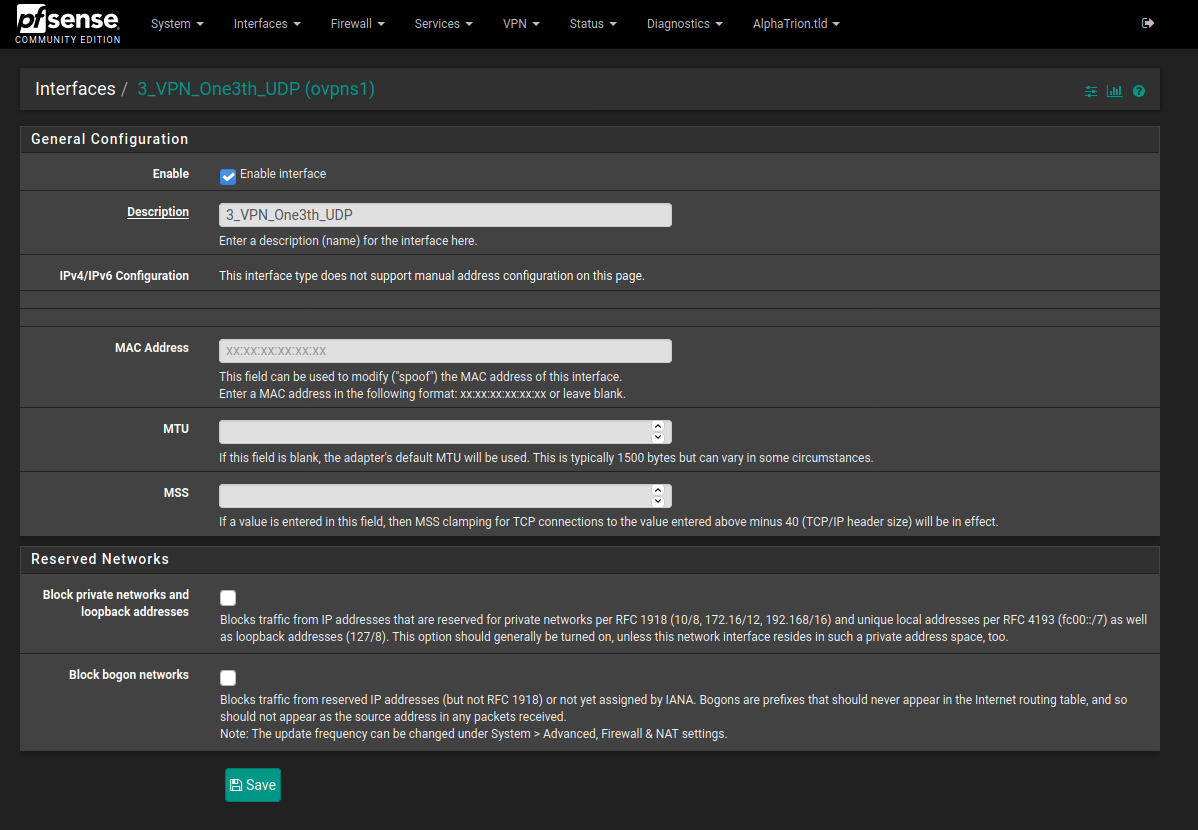
That will create another interface in your firewall rules. You should not have to add any rules to it because the OpenVPN rule is acting like a group rule for your VPN interfaces.
I thinking that may updated the ovpns1 IF entry from the firewalls to whatever name you give it.
-
@hieroglyph ahh yes, you're right on the money with that one!
This page in docs helps to provide some more info regarding it's purpose:
https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/assign.htmlHowever, the one outstanding question I still have on this is: if it wasn't added as an interface in it's own right to begin with, how could the firewall be blocking on it? Attempting to access the VPN from WAN at it's allocated port via a webbrowser just creates a WAN firewall block entry (not the 'ovpns1' type). And attempting to access via LAN doesn't create a firewall entry at all...
@Gertjan ah, that's some great insight - thank you! You've exposed to me my need for a syslog server on my network! I'll spin one up in the next few days and report back with my findings based on your methodology

-
@hieroglyph said in OVPNS1 + LAN->WAN Blocked Firewall Rules:
Interface column and say "ovpns1 (OpenVPNServer)"
aaaah : that where the ovpns1 comes from.
Still strange, as all the OpenVPN server instances are stached under the 'fake' interface called 'OpenVPN' s soo as you have one OpenVPN server, or more.
When you assign the existing internal interface (TUN interface ?) to a (example) "MY-VPN-SERVER", and activate "MY-VPN-SERVER", as you have shown, it is possible to create firewall rules per OpenVPN server.
The default OpenVPN interface is uses for all OpenVPN server instances, and can be emptied, as you use now "MY-VPN-SERVER". Or use both, to make live more complicated.
I wonder, why do the logs shows "ovpns1" if its also known as the more logical "OpenVPN" ? -
@gertjan The openvpn interface is just a group interface for all of the my-vpn-serverX interfaces. It is treated the same way any other interface group is treated.
NAT Rules --> Floating Rules --> Group Rules --> Individual Interface Rules
-
I think "ovpns1" is short for "OpenVPN Server #1". If a second openvpn server is created it should be seen as "ovpns2".
OpenVPN Clients should show as "ovpnc1"
-
@theskelly said in OVPNS1 + LAN->WAN Blocked Firewall Rules:
However, the one outstanding question I still have on this is: if it wasn't added as an interface in it's own right to begin with, how could the firewall be blocking on it?
I do not know the answer to that question. My best guess; it is a rule pfsense automatically generates. Maybe as a safe guard when an interface is not created yet...???