Would anyone be interested in testing a tool for converting pfSense FW rule XML exports into a Google Sheet and back for re-importing into pfSense?
-
I am not a fan of the pfSense rule editor. I like having all of my rules in one table.
I wrote a little Google Apps Script that:
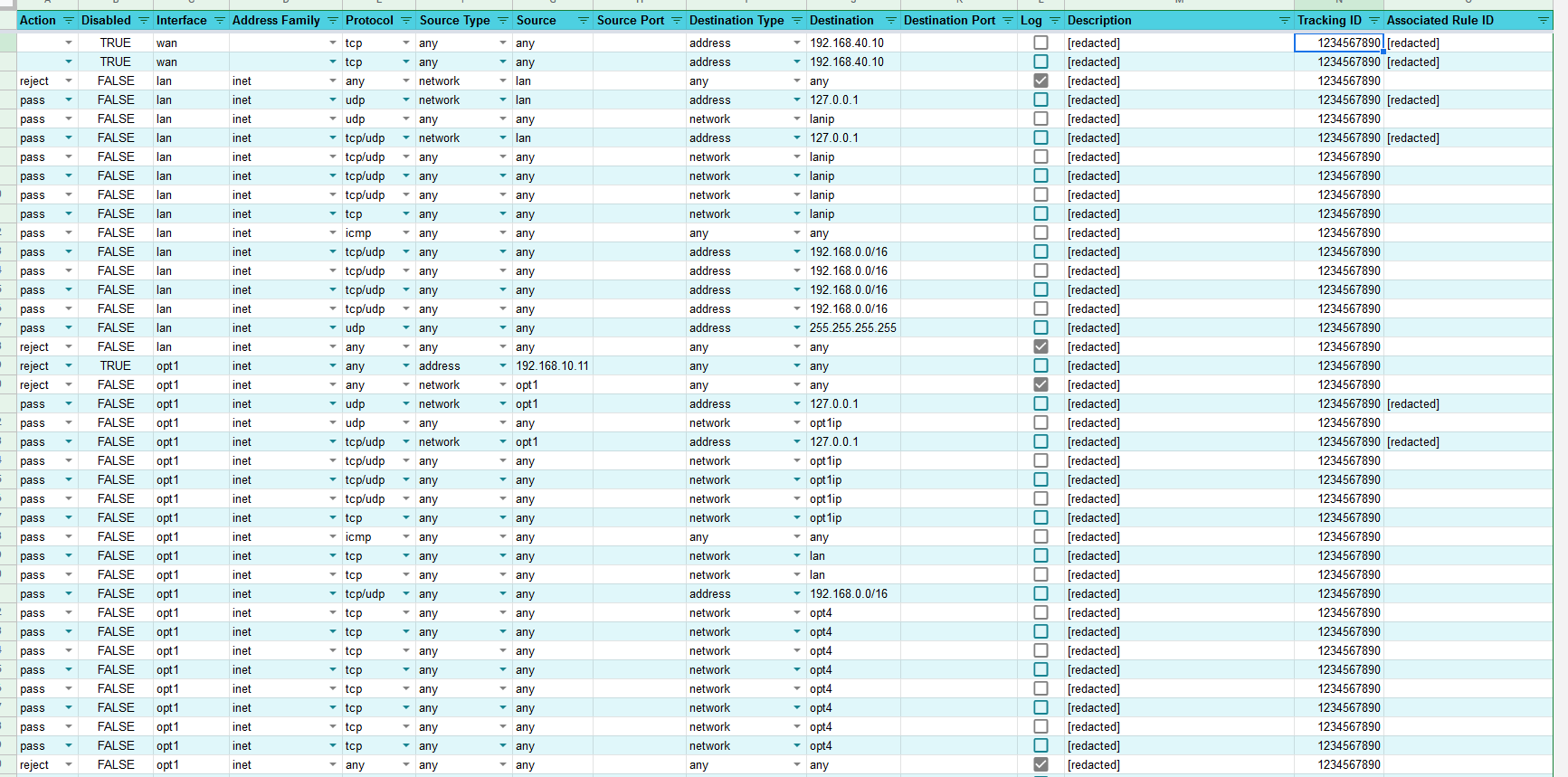
- Converts an XML export of FW rules (from Backup & Restore) into a Google Sheet (example screenshot below)
- Converts a Google Sheet back into XML that can be imported back into pfSense
It is not perfect:
- Google Sheet is not aware of your pfSense setup so doesn't have helpful drop-downs with your network information. But I am using it to view my current rules, add more by copying another rule, and then importing -- so it will work for my needs.
- I haven't added logic for all of the various FW rule options/settings yet.
Unfortunately I do not have a robust environment I can test in. I only have one pfSense box and I don't wanna go mucking about with it's FW rules -- if the export (Google Sheet to XML) fails then I'd hose something up. I don't have any machines I can run a VM in so I can't set up a test pfSense box.
So I'm wondering if folks are willing to help me test this out. If so then I'll publish this and share it. It is hosted in Google Apps Script -- folks can use my published web-app or publish their own. Once the script is published:
To import:
- Export FW rules from pfSense from Backup & Restore
- Copy/paste the XML into the web-app (I'll add file upload later)
- Submit -- it will import the XML into a Google Sheet
To export:
- Tell the web-app the URL of the Google Sheet (I'll add a file picker later)
- Select the sheet with the data you want to import
- Submit -- it'll convert the data into XML and show on the screen (I'll add file save later)
If you are interested in helping me test it out, please let me know.
-
This seems like a nice function.
But i'd never store (reveal) my rules in anything google (cloud) related.So this is not for me.
But nicely done./Bingo
-
@bingo600 said in Would anyone be interested in testing a tool for converting pfSense FW rule XML exports into a Google Sheet and back for re-importing into pfSense?:
But i'd never store (reveal) my rules in anything google (cloud) related.
May I ask why? I often ask myself what is the risk of someone knowing your FW rules. The way I see it, rules are only relevant when you're in the network. If someone can access the FW then they can get the rules anyway. If they can access a device in the LAN/VLAN then FW rules can tell them lateral paths but so can port scans from the device they are on.
So I'm just not sure what the risk is with someone knowing your FW rules.
-
Your rules could reveal openings that should not be public knowledge.
And there a tonzz of examples of cloud services that have been compromized.I would never do it.
/Bingo
-
@bingo600 So exposing WAN rules, like open ports and all that, right? But even those could be found with a port-scan.
What can someone do with my LAN FW rules?
I know its not recommended, but I cannot figure out why.
Cloud services were compromised because people left things open -- not cause someone knew the FW rules.
-
@imthenachoman said in Would anyone be interested in testing a tool for converting pfSense FW rule XML exports into a Google Sheet and back for re-importing into pfSense?:
@bingo600 So exposing WAN rules, like open ports and all that, right? But even those could be found with a port-scan.
What if you have permitted a specific ip address to access a specific port.
Would not be found by a port scan.
But your rule (sheet) would tell what source ip address to try to spoof.What can someone do with my LAN FW rules?
Prob. not much , if you trust your lan users.
I know its not recommended, but I cannot figure out why.
Do you give out your CC number , and expect it is safe just because they don't have the CVV ?
Cloud services were compromised because people left things open --
not cause someone knew the FW rules.Excactly , or because Google snoops
-
Have a look here.
https://thehackernews.com/2021/01/new-attack-could-let-remote-hackers.htmlAnd imagine you just have given out your internal firewall rules.
-
@bingo600 Sure but that attack vector doesn't need your FW rules. In fact, your FW rules become irrelevant because the attack bypasses them.
But I do hear what you're saying about not disclosing your FW rules. Makes sense to me now.
-
Well, if anyone wants to check it out: https://github.com/imthenachoman/pfSense-Firewall-Rules-Manager.