DynDNS and host (rdp)
-
Good morning,
I have a problem with accessing a host on my LAN from outside.
I would like to connect by name DynDNS to an internal host (server).
Enabling the rules etc: I can't connect in any way.
I state that it is a new firewall.
Can you help me and suggest me how to do it (besides enabling the OpenVPN-Server server)?thank you so much.
-
@pietro-morre Make a vpn server. Otherwise show the Rules and NAT and IPv4 connectivity check from outside.
-
@pietro-morre said in DynDNS and host (rdp):
I state that it is a new firewall.
That doesn't matter.
The technic you will have to sue is called NAT. That's a very old router functionality (somewhere in the end of last century) that maps incoming connection on a port on WAN, to an internal, LAN type device, using a port.
NAT hassle will be over as soon as IPv6 can deal with everything, and IPv4 starts to fade out.Because traffic has to comin in on WAN, the pfSense firewall should also have a firewall rule on the WAN interface that let the traffic enter. It's typically a "from everybody, to port X" rule.
You could should change the "everybody"here to "somebody" if yoy know what IP will be used to connect to your local device.RDP : as Microsoft states : use it on a LAN, from device, to a device, or use it over in trusted networks.
Never - ever - over the Internet period. Only fools do so, and they all entered the "I'm so sorry phase". Don't become a member of that club.Since the beginning of 2020 half the planet has become an OpenVPN expert, so, good new, just join them. It permitted millions to keep on working - or at least trying to do so.
So, I advise you to :
Youtube. Look for the Netgate page. They have videos (!). Look at the two Initial and Advanded OpenVPN video. There is also the style, mini, recent video. Do look the big ones. Your video host, jimp (without the @ now) explains the entire thing step by step.
Now set up OpenVPN server. The GUI is quiet daunting, but still better as creating yourself a openVPN server config file (see example below).
As soon as it runs, and you have this :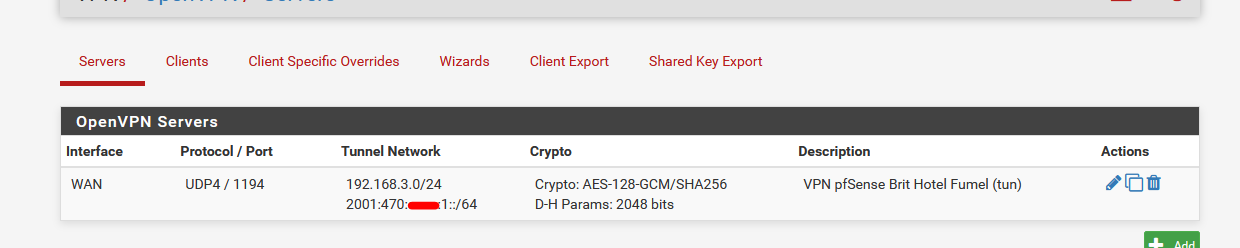
(note : the ipV6 in my image is purely optional)
If you used the pfSense OpenVPN server setup wizard, the needed firewall rule will get auto created.
if not - and I advise you to set up the OpenVPN server manually, you will have to create a rule like this :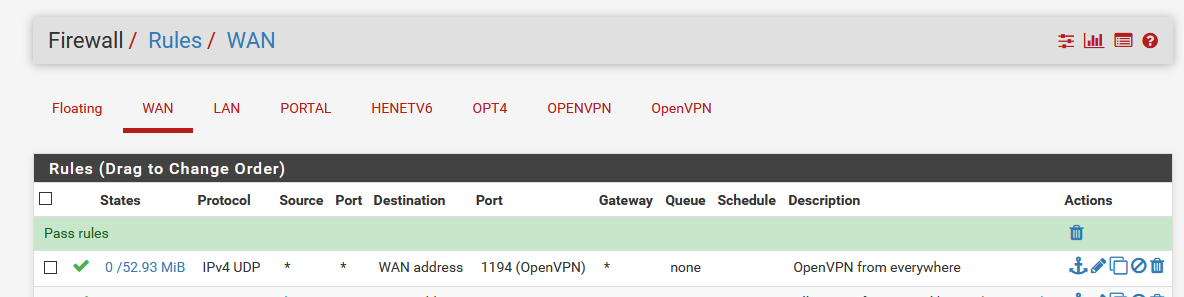
( pretty easy, right ?! )
Now, a small pause and no brainer : install the OpenVPN client export pfSense package.
See again the official videos, and learn how to set up users or even better : certs and how to export a client OpenVPN config file.
Then, take a phone. Disable the wifi ( !!!) and install the 'real' Official OpenVPN client.
Copy the exported Client OpenVPN file to your phione and 'import' it in the OpenVPN official app.
Connect.
When you reached this point, have a look at all the other so called pfSense OpenVPN videos.
See them.
Understand now why the other half of the planet will never have a working VPN.My OpenVPN server pfSense config file. This is what you create with the GUI :
dev ovpns1 verb 1 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_server1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 cipher AES-128-GCM auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown local 192.168.10.3 tls-server server 192.168.3.0 255.255.255.0 server-ipv6 2001:470:ccea:1::/64 client-config-dir /var/etc/openvpn-csc/server1 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'my-local-domain.tld' 1" lport 1194 management /var/etc/openvpn/server1.sock unix max-clients 10 push "dhcp-option DOMAIN my-local-domain.tld" push "dhcp-option DNS 192.168.3.1" push "dhcp-option DNS6 2001:470:xxxx:1::1" push "block-outside-dns" push "register-dns" push "dhcp-option NTP 192.168.3.1" push "redirect-gateway def1" push "redirect-gateway ipv6" client-to-client ca /var/etc/openvpn/server1.ca cert /var/etc/openvpn/server1.cert key /var/etc/openvpn/server1.key dh /etc/dh-parameters.2048 tls-crypt /var/etc/openvpn/server1.tls-crypt ncp-disable persist-remote-ip float topology subnet -
@gertjan said in DynDNS and host (rdp):
Never - ever - over the Internet period. Only fools do so, and they all entered the "I'm so sorry phase". Don't become a member of that club.
Hahah - good way to put it..
Also keep in mind that even once you vpn into your network. You will have to make sure the firewall on the device your trying to RDP allows the access from a non local network.
The only time I could see allowing RDP over the internet, not inside a vpn would be if you needed to let someone in to troubleshoot. And you KNEW their IP they would be coming from, and you could lock down your port forward to their IP, and ONLY their IP..
-
@gertjan great ah! i will use openvpn. beginner question: if I have 2 other pfsense fw can I set them as "client" in order to make them communicate with the same IP class? or use 3 classes of ip (1 in the openvpn server and the other 2 clients) without any problem? (all 3 are set with 3 different DynDns.
-
@pietro-morre said in DynDNS and host (rdp):
I set them as "client"
You're in luck.
The VPN section has also a VPN client.
So you can connect one pfSense to another pfSense etc etc.
And guess what : There are video's about that to ;)@pietro-morre said in DynDNS and host (rdp):
use 3 classes of ip (1 in the openvpn server and the other 2 clients) without any problem? (all 3 are set with 3 different DynDns.
The two clienst don't need an DynDNS. Only the server.
The server is like a ...... server - a web server ! - it waits. Just wait, until some one connect to it.
This "some one" can be a phone with OpenVPN client or a PC with OpenVPN or pfsense with OpenVPN client. These have to know your hostname (your DYNDNS URL), that's all. And that will be the WAN IP of your openVPN server.
So, yes, why not, two or more OpenVPN pfSense could all connect to a OpenVPN server, also a pfSense.Btw : before you ask : No, you won't be able to 'see' all the devices in all the networks on all the sites in the Windows Explorer. But you will be able to use IP's or host names and use these to connect to other devices, local, or remote, all over VPN tunnels.
So, have a look at some serious video's what DNS is really about. Time to leave the state where you think you understood it, now you have to know. Or just stick to IPv4 and it will plain work. Troubles will arise when everything shifts to IPv6....... ;)
Goof to know : interconnecting two networks :
Your LAN network on site A has 192.168.1.0/24
Site B - its LAN, can't be 192.168.1.0/24 - it should be another RFC1918, like 192.168.2.0/24
Site C should have a be different LAN, also 192.168.3.0/24.The tunnel network, used by the VPN server, should be different again like 192.168.254.0/24
You will probably also have to refresh the knowledge about what a router is / does - what routes are.
Example :
On site B you should 'inform' your pfSense that the network 192.168.2.0/24 and 1982.168.2.0/24 goes over the VPN, the rest, by default, goes over the default gateway == your internet access.
Same : on Site be you have to inform the system that the network 192.168.1.0/24 can be reached over the VPN. The rest over the default WAN.
Etc.
Myself, I my VPN just as a road warrior access - never tried to connect to sites together.
That is, I can connect from my home to my work, and then use/connect to all work LAN devices. That's already bad enough.