FW rule misrouting traffic with terminated OpenVPN
-
Hello,
I’ve created two ExpressVPN interfaces that successfully connect and work:
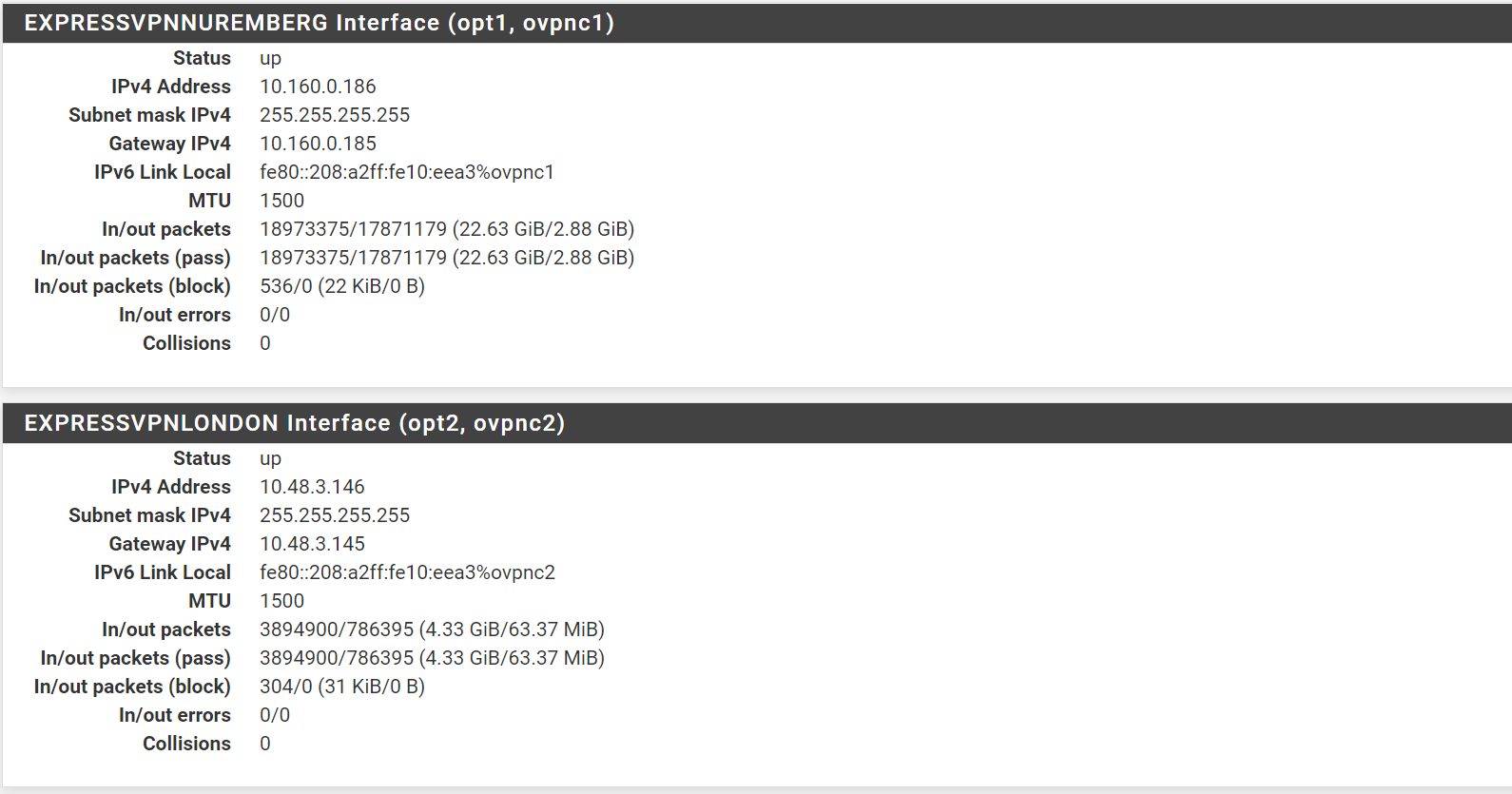
I’ve created firewall aliases to two internal (192.168.x.y) systems:
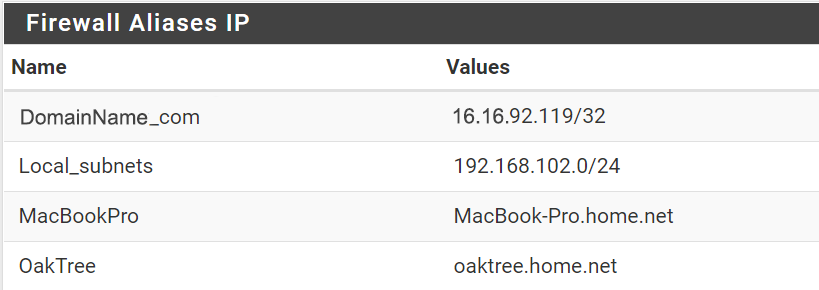
I’ve created firewall rules to assign one alias per OpenVPN interface. I’ve copied the default IPv4 and IPv6 rules to block any traffic from the two aliases except the ExpressVPN interfaces:
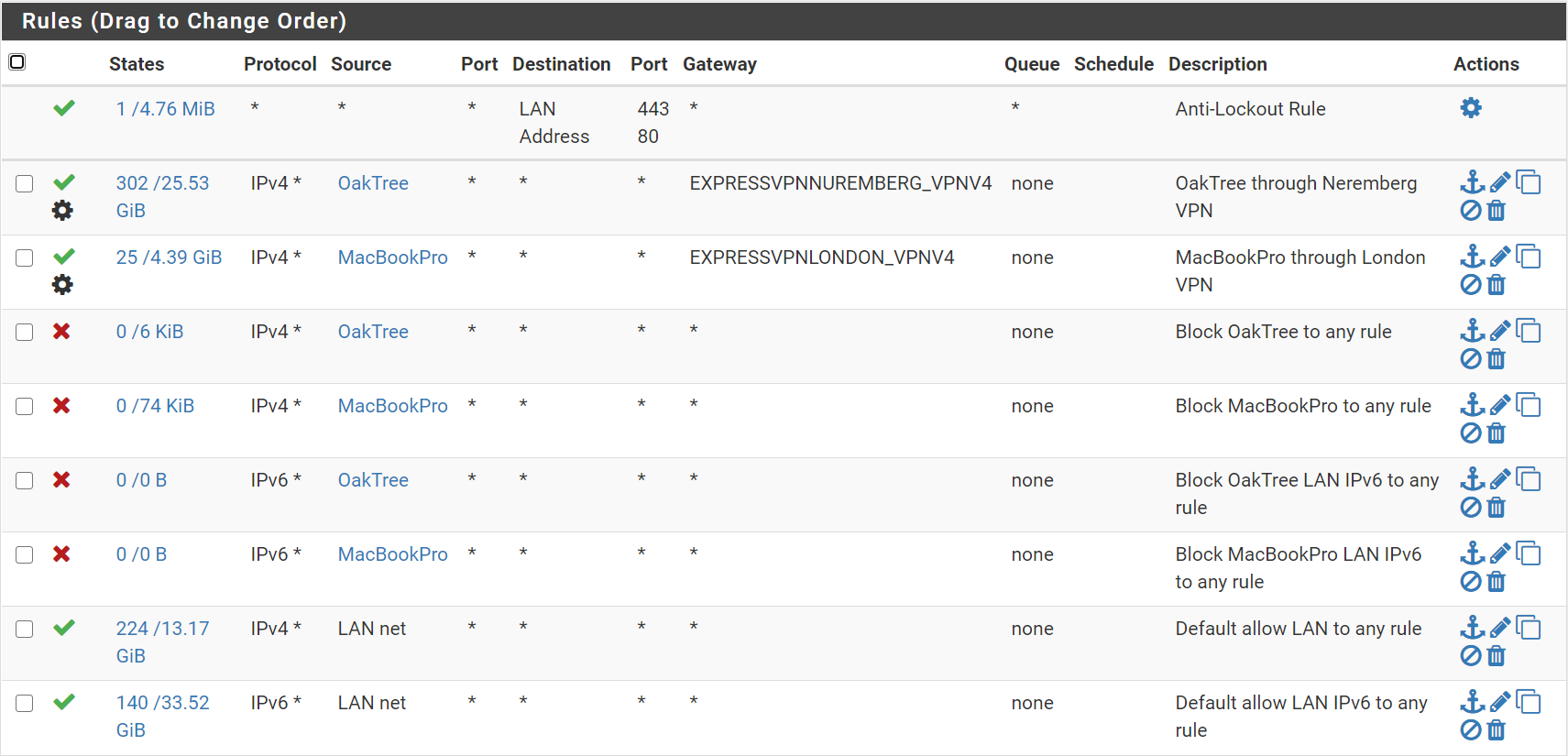
I’ve had now had multiple incidents where OpenVPN seems to crash and the daemon fails to restart. Since the OpenVPN service is down, I would expect all traffic from the two internal systems would be blocked. However, the two systems are being sent to the default network.
When moving my block rules to above the OpenVPN rules, the clients are blocked as expected.
Can anyone explain how this is happening? Any suggestions in creating rules that prevent this scenario?
Thanks -
Additional information.
Well, I'm at a loss. If I disable the OakTree to ExpressVPN rule in the firewall, the client has a couple of ping stallouts and then just keeps on pinging as if nothing changed. Tracing shows it is still using the ExpressVPN route.
At this point, if feels like I have no idea how pfsense firewall rules work. Any suggestion welcome...
-
@thaddeusf As to the last point, did you reset states?
But mostly my question is, are you trying to configure an "kill switch" so that no traffic leaks ?
If so, there's another way. In your "gateway" rules, mark the traffic with a tag.
Something like "No_WAN_Access"
On the floating rules tab, create a rule
Action: Block
Interfaces: All
Address Family: IPv6 & IPv4Source: Invert Match -> THis firewall
Destination: Any
Tagged: No_WAN_AccessAny traffic that matches that tag that "leaks" from the VPN will be blocked.
-
Thanks Griffo. Resetting states is at lease making my test consistent.
I think the problem might be:
System > advanced > Miscellaneous > Gateway Monitoring
Skip rules when gateway is down.It appears this needs to be checked.
Thoughts?
-
@griffo Yes about the prevention of traffic leaks.