Setting up for Wyze cam base station
-
@hieroglyph I managed to lock myself out and lose my network completely by making some change. I was able to restore a prior setup at the computer I have pfsense running. So I'm back to where I started. The few tweaks I tried on advice didn't change the off line status of the base station.
-
@hieroglyph Well, I finally got it working by the last thing I tried: dragging the NAT rule above everything else
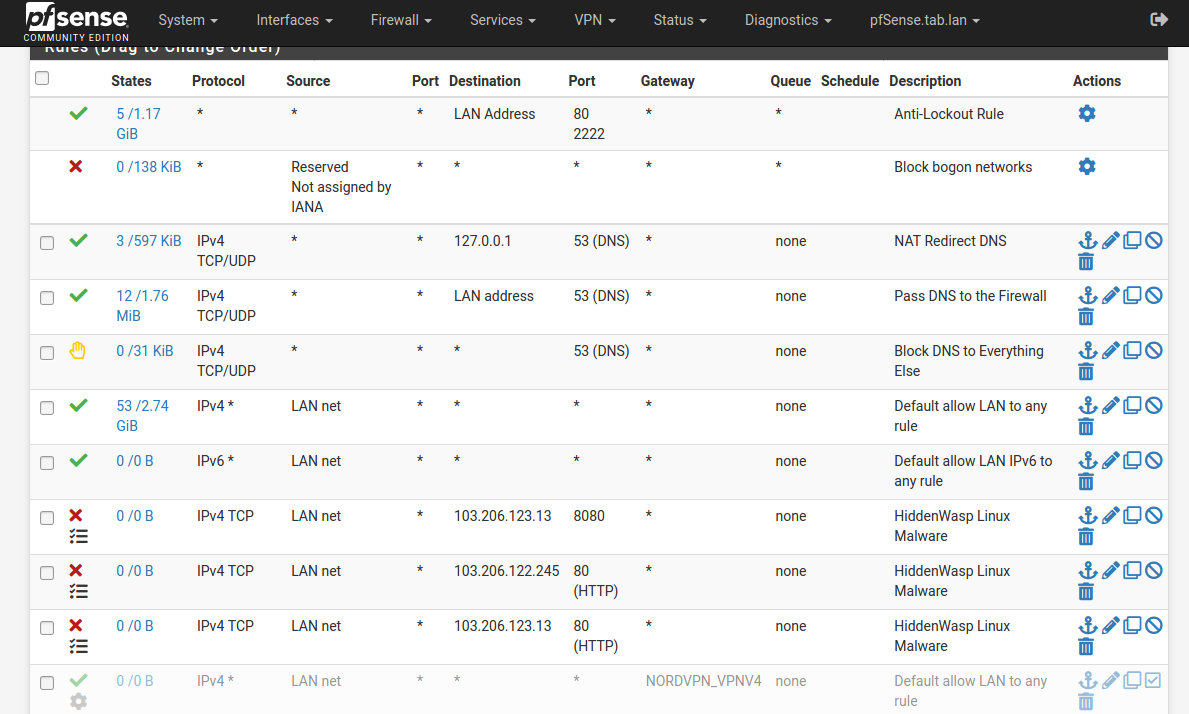
The links provided in this tread showed examples for DNS and NAT, but none I found that showed both, or mentioned order of precedence though I might easily have missed it.
Of course, I'm also not sure I've not set myself up for new and different vulnerabilities through this ruleset either. I'm wondering if there are tools to safely test a pfSense configuration.
I would like to place all such 'IoT' hardware on a VLAN, but reading and watching tutorials all seem to require a managed switch, which I don't have. Having one with POE for a Unifi AP is appealing but the costs aren't insignificant.
I today wondered about just placing IoT stuff on a different subnet, but wouldn't that also require establishing comms between the two subnets (port forwarding)?
-
@lucas-0 Yep. That is how I have my rules ordered.
The x3 block rules for "HiddenWasp Linux Malware" will never be reached because they are below the two allow all rules (Default allow LAN to any rules) for IPv4 and IPv6. Same for the NORDVPN_VPNV4 rule. It will never be reached because LAN traffic will take the "Default allow LAN to any rules).
Rules are processed in a top to bottom order (with an exception of floating rules). I will not get into detail. But this is a good read to explain how to order rules.
If the pfsense box has at least x3 ports it could be set up as follows:
port1: WAN
port2: LAN --> Switch1
port3: LAN_IOT --> Switch2This would give the same result as using VLANs to separate LAN from LAN_IOT. If LAN devices need to access LAN_IOT devices then a firewall rule will need to be put into place. Depending on how the IOT device is configured a NAT Outbound rule may also need to be put into place if the IOT device does not respond to IPs out of its IP address range.
For me, I just set up a generic NAT Outbound rule (allow LAN to LAN_IOT). The NAT rule does not do anything until there is a firewall rule setup which also allows (LAN.deviceX to LAN_IOT.deviceY). Don't be afraid to put pfsense into hybrid outbound NAT mode. It just moves the auto-generated rules to the bottom and allows the creation of custom rules.
But as always; before any changes are made to the pfsense box make sure there is recent backup configuration easily available for restoring in the event a mistake is made during the learning process.
Good luck and have fun!