HAProxy : Shared Frontend: SSL and Non-SSL Backends?
-
I have one public IP, and 3 different webservers behind a PfSense router. All 3 webservers are in a DMZ.
One of the webservers is a development server, and it's basically just for toying around with different web designs. I rarely need SSL for these sites, since I'm never accessing them over the internet. Though, sometimes I do want SSL for when I have to login to the site over the internet.
The other 2 webservers (a CRM and a Nextcloud instnace) need SSL and to redirect http to https.
I THINK I want to install the certificates on the PfSense box, and I don't THINK I need encryption form the proxy to the webservers (there's not much of an opportunity to snoop, anyway).
I am getting myself cross-eyed on how to set up the back/front-ends and make everything play nice.
-
Hi oguruma,
I am by no means an expert on the topic but what you described in your post is exactly the kind of setup I have successfully deployed at home.
You are right in assuming that you do not need SSL for the communication between HAProxy and the servers themselves.
It's a home brew setup... you're not a bank with strict security guidelines you have to adhere to.
General outline of my setup on PfSense:
-
ACME Certificates - automatically renews the Lets Encrypt for my domain (Domain Service Provider: DynuDNS)
wildcard dns records are not support by every service but I find it seriously cool
This video helped me with the initial setup: https://www.youtube.com/watch?v=jpyUm53we-Y
I needed to add CAA records for Lets Encrypt and TXT records for both my "root" domain and the wildcard domain (for all subdomains) as part of the verification process during certificate renewal. This is required to prove that you are the owner of the domain. There are alternative verification methods to choose from.
Example CAA records:

-
Dynamic DNS Service - update A records when your public IP address changes if you have a dynamic one.
This is what my cron job to check my IP every 5 minutes looks like:
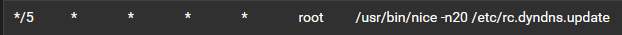
-
HAProxy - use this tutorial to setup a shared https frontend accompanied by an automatic http→https redirect:
https://www.youtube.com/watch?v=7WiZ1i2u-Lc
For added security on the frontend I'd recommend adding these options to "Advanced pass thru" under "Advanced settings":
http-response set-header X-Xss-Protection 1;\ mode=block
http-response set-header X-Content-Type-Options nosniff
http-response set-header X-Robots-Tag noindex
http-response set-header X-Frame-Options SAMEORIGIN
http-response set-header Referrer-Policy same-originThe shared https frontend will then basically be the only contact point with the internet and contain your certificate, so that you never ever again have to worry about updating certificates for each individual server.

If you'd like some more pointers on for instance how to make a server accessible through the reverse proxy via "servicesubdomain.domain.tld" but deny all access to said server from the internet just let me know.
-
-
@clarence
I'm glad I found your post, maybe you can help me too.
I also use Dynu.com and am trying to setup SSL from Let's Encrypt but I can't get it to work and I'm thinking it has to do with authentication through Dynu.I have one static IP address and want to be able to host 2 or 3 websites, all public.
I also like to watch Tom's videos at Lawrence Systems and watched the video you linked before I got started but it wasn't clear enough for me. I found this video which walks the way through the creation of the setup.
https://www.youtube.com/watch?v=FWodNSZXcXsNow I setup essentially the same configuration he put together. In Acme I created 1 wildcard cert from Let's Encrypt for my domain and one specific to one of the websites. They all completed successfully. His setup worked mine didn't. So I did more searching and found your post here.
I did not know CAAs had to be created so I just added them to my Dynu DNS records.
I also added your suggestion for the added security settings to my setup.
Still my websites will connect through HAproxy but they still show "Not Secure".You mentioned you had to create txt records. What are they and where do they go? What infomation needs to be in them? Is this because of the way Dynu works?
Any ideas what I could be missing.