DoT with openvpn
-
Hi there, i have openvpn clients configured on my pfsense with kill switch, i also configured DNS resolver to use 1.1.1.1 DoT and set outgoing network interfaces to be my VPNs, in floating rules on WAN i block all outgoing traffic on ports 53 and 853(with exception to 1.1.1.1).
I have few questions:
- With plain dns i was able to catch all requests with NAT and redirect them, with DoT i cannot do this due to encryption, right? And so because of this i have to block everything outgoing that is not my 1.1.1.1 dns resolver?
- Setting outgoing network interface to by one/any/all of my VPNs is needed to not show my real ip on the side of the DNS server, right?
- Do my floating rules make sense?
- When i do wireshark scan of active requests on the machine that sits under pfsense, i still see requests being made on port 53, but they are sent to pfsense, so am i right when i assume that the dns chain looks somethings like this pc(port 53) -> pfsense(port 853) -> dns server(port 853)?
-
-
You can redirect plain DNS and DNS over TLS request headed toward say 8.8.8.8 back to pfsense to handle. Copy what you have for your plain DNS redirect NAT and firewall rules and replace port53 with port 853
-
Are you asking, "how do I route traffic thru the VPNs to the outside world"?
-
Without seeing how you have set up your rules it is hard to tell if what you have done makes sense. I used this guide to get me started with setting up an outgoing VPN with DoT. Then moved to the part two of the guide to get multiple outgoing VPNs. Hence my firewall rules look similar to what is shown in the guides. For the most part the guides are pretty well sectioned and you can pick and choose what you want.
-
If you have the DNS Resolver and your plain DNS/DoT NAT redirect rules, and firewall rules set up correctly your DNS and DoT request from LAN will look like you described:
Plain DNS Request
pc(port 53) -> pfsense(port 853) -> dns server(port 853)DNS Over TLS Request
pc(port 853) -> pfsense(port 853) -> dns server(port 853) -
-
- What is more difficult to redirect is DNS over HTTPS (DoH). This is because it uses the standard 443 HTTPS port. If you are using DoT you could block all traffic to a DNS over port 443. But this may not be 100% effective if someone uses a DoH server you are not specifically blocking.
-
This post is deleted! -
i was able to configure dot, but i still don't understand how can i fully block everything coming out port 53, with this rule in floating
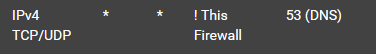
i can block everything when vpn is up, but if i stop and start openvpn client it can't resolve host address, what can i do to fix that? -
@popso2 I am not sure why you are trying to block everything coming out of port53 with a floating rule. From what I have seen, the proper way to prevent devices on you LAN from being able to access their own external DNS is to redirect LAN traffic destined for port53 and an external ip back into pfsense. Please read this. It will show you exactly how to redirect external DNS requests back into pfsense. You can copy the rules you make and change port53 to port 853.
This is a related document on how to block DNS requests headed toward external servers.
-
@hieroglyph
Thanks for help, i was able to configure everything, the reason i was using floating rules in the first place is because i saw them being used in some other guide about DoT