Deleted rule persists.
-
I had allow all traffic on a wireless VLAN I created, with a Unifi AP. When testing the firewall rules I then created a rule to block all traffic to LAN, to see how separate the VLAN would be. It worked, and I couldn't ping anything on LAN, but still had internet access.
When I deleted the rule it persisted. It's stuck and I can't get that VLAN to see anything on LAN again. I deleted states and rebooted. What else can I do?
-
Without seeing your rules its impossible for anyone to guess what you might have done wrong.. Wrong order, wrong protocol (tcp) and trying to ping to test..
Did you actually reload the rules?
You can always force that with.
And watch status that they actually reload.. You can always debug rule via looking at the rules.debug
cat /tmp/rules.debug
-
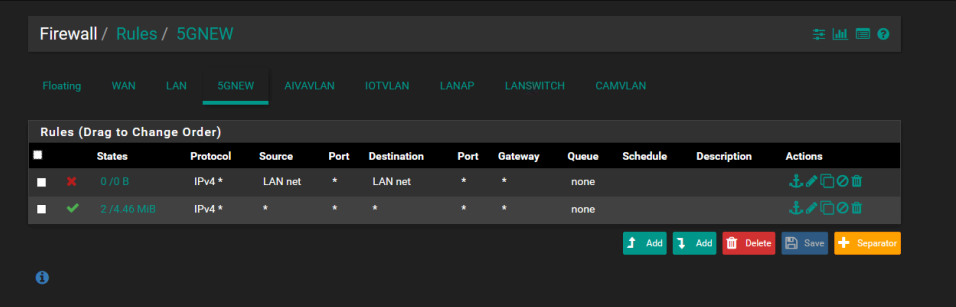
This is a fresh install so only one rule on every interface which was allow all. All protocols. The block LANnet rule was added so I could test rule making. Disabling or deleting doesn;t seem to remove it. I can't ping anything on LAN and I can't even ping PfSense itself.
-
I did filter reloading during troubleshooting.
-
Well that rule would never trigger on the 5gnew net.. Since source would never be lan net..
So it would never do anything.. Notice the 0/0 - means it was never even evaluated.
If you have the default any any rule and you can not get to lan net devices - the number one issue with this is firewall rule on your device on lan your trying to get to.
Can you ping pfsense 5gnew IP? Can you ping lan IP of psfense?
If you can not ping pfsense 5gnew IP from 5gnew device - you sure your even on 5gnew? Clearly you have some traffic hitting this any any rule, and currently 5 states open on this rule.
Do you have any rules in floating?
edit:
Do you have bridges setup.. Names for interfaces/vlans with lanAP and lanswitch getting me thinking you have some bridge setup and are trying to put multiple interfaces in the same L2 network? -
Sorry for the picture, I remade the rule to demonstrate after deleting, and didn't plug in the right source.
I can ping the DHCP server for 5GNEW, but not the PfSense gateway. I will go home tonight and wire everything into a proper switch and have all interfaces (VLAN, LAN) coming off the LAN port on the router.
The dummy bridge I was talking about in the other post has been removed for all this troubleshooting.
And no, no floating rules. Firewalls are also disabled on each PC I am trying to ping to from LAN to 5GNEW.
-
@nerlins said in Deleted rule persists.:
I am trying to ping to from LAN to 5GNEW.
Then you would allow that on your LAN interface rules.. Which would be allowed by the default any any rule on lan.
I can ping the DHCP server for 5GNEW, but not the PfSense gateway.
If you can not ping the pfsense 5gnew IP from a device on 5gnew network. And you have a any any rule on the 5gnew interface or you have rule that allows you to ping the pfsense 5gnew address.. Then you have something wrong in your connectivity on your 5gnew network.
But if you have a rule that allows it, and you can not ping it from 5gnew - then no how would anything talk from lan to 5gnew, if devices on 5gnew can not talk to 5gnew on pfsense to answer..
-
I keep thinking something went goofy with the Unifi AP when I created the block rule to test, then deleted it. I am actually testing these PCs remotely as each has RealVNC on them. One is on LAN and of course the other on 5GNEW (wireless VLAN). I tried a reboot command from the LAN PC to the AP but not sure if worked. I will physically unplug and replug when I get home.
All in all it's just weird that I had allow any and all as the only rule on both interface and everything worked fine before testing and deleting the block rule.
-
I add and delete block rules all the time - you are hung up on that chasing a red herring.. I can tell you for fact that the block rule you showed was pointless and useless and would never had done anything.
-
The Unifi contoller lost access to the devices last night, would not find them again, so I had to install it on another machine on LAN.
John, is this a case of untagged and tagged traffic issue? I was told that untagged traffic can't flow over tagged. I am not visualizing the LAN this way, but as 'not-tagged' just typical traffic. I couldn't get an answer if the LAN should also be a VLAN.
I am very new to all this, so dumb questions are gonna flow from my mind till I grasp it all.
-
@nerlins said in Deleted rule persists.:
I was told that untagged traffic can't flow over tagged
Huh?? Not sure what your trying to ask.. A physical cable can carry multiple vlans, all tagged or 1 untagged and all others tagged.
No your "lan" doesn't have to be a "vlan" it can be the native network on the interface (untagged) while you also have vlans (tagged) on that same physical interface.
The simple solution for controller and AP is to put them in the same L2 network. Normally this should be untagged network. But not that long ago if your running beta firmware and controller software they did add the ability to do tagged management network.
If your going to put your controller on a different L2, then you need to do L3 adoption.. And sure your firewall rules would have to all connectivity between the IPs and the 2 different networks.
I have my controller and the AP on their own L2 (192.168.2/24) this is untagged at pfsense and untagged going to the controller and the AP.. But is tagged over trunk port for example that connects 2 of my switches.. Because this trunk carries multiple vlans. When a wire connected to a device, or another switch needs to carry more than one network(vlan)... Then they need to be tagged. But you can have up to 1 of those networks untagged.. When a device is only going to be in 1 network/vlan - then the that port would be using the untagged vlan, which can be any vlan.. So for example the port connected to my AP has untagged (vlan 2 on the switch) which is the management vlan that AP ip is in, and also 1 of my SSIDs.. The other SSIDs on that AP are all tagged on the port.. And the SSID is set with that vlan ID..
Step one when wanting to start playing with vlans.
- understand what tag and untagged means ;)
-
Still working through this. Don't have anymore free time till the weekend.
I don't think I'll ever be able to put the controller on a different L2 network because these stupid flex mini switches have no ssh, so no way to set-inform the new location of the controller. I know there is an option in the controller for allowing discovery over L2. I haven't tested that to see if it works.
-
You should be able to use the dhcp method of handing out the controller info that is on another network. ie L3 adoption.
Yeah looks like those minis have no ssh, or even ability to set management to a vlan, has to be a untagged/native network..
L2 adoption should be default.. You shouldn't have to enable that.
-
Had a rough winter storm period a couple of weeks ago, then a hard work week. I'm just now tinkering with pfsense again. I've spent many evenings studying VLANs and subnets, and hopefully have risen above stupid questions to more-informed.
I figured out the 'rule' problem I had. It wasn't rules, but the Proton VPN client on one of the computers breaking the routing from VLAN to LAN. I'm not even sure how it did that. Disabling the program caused all pings and tests to work. Using split-tunneling in the program to allow certain traffic works, while still being able to keep my VPN running.
Honestly, I just thought the VPN masked my public IP, and wouldn't affect internal VLAN/subnet routing. Any words of wisdom why that happened?
-
A vpn client on a machine sends all traffic down the tunnel.. Unless you can setup split tunnel, it won't send any traffic even to your own local network, let alone a vlan on your network.
I have the same issue with my work machine to be honest - it forces login to work vpn. So have no access to even my local printer or nas.. And its pretty much impossible to not get it to log into the vpn ;)