New, often requested Snort feature coming soon!
-
I've found a way to implement an often requested feature in the Snort package on pfSense. Many users over the years have requested the ability to add more custom IP addresses or IP subnets to a Pass List. And many have also asked for the ability to use dynamically updated aliases in a Pass List. A dynamically updated alias is one that becomes a table name in the
pffirewall engine and has its IP content periodically updated by thefilterdnsdaemon. These are popularly known as FQDN (fully qualified domain name) aliases.An upcoming Snort package update will add this new feature. Look for it first in the development snapshots. It's not there yet, but will be soon. I will post an update when the new version with this feature is available. After sufficient testing time there, it will be migrated to the RELEASE branch.
Before everyone starts asking, let me set out the limitations of the new feature.
- No, you can't use firewall aliases in Snort rules! Don't ask for this. It's not possible without rewriting a considerable chunk of the Snort binary.
- This new feature only works with Pass Lists, and you only use Pass Lists in Legacy Blocking Mode. When you use Inline IPS Mode, the custom blocking module is not used and thus Pass Lists are not available.
- You can only use aliases in Pass Lists to prevent those IP addresses from being blocked by Snort. Refer back to limitation #1 above.
- The aliases are not maintained by Snort. Instead, the
filterdnsdaemon in pfSense is responsible for updating the IP addresses in dynamically updated aliases. The default update period is 5 minutes. Sofilterdnswill refresh the table contents every 5 minutes. Snort will check the alias table to see if the IP from an alert is present. If the IP is in the alias table, it will not be blocked. But be aware that many popular sites are behind CDNs (content delivery networks) which use very short TTL values - some as short as 2 or 3 minutes. Thus these sites can have an IP address that changes every 2 or 3 minutes (faster thanfilterdnscan keep up with). In fact, while testing this new feature withgoogle.com, I had one set of IP addresses in my test firewall (from afilterdnslookup and update cycle) and a different set of IP addresses on my Windows workstation from a "nslookup" command one minute later. Some of the IPs matched, but not all of them - thus the problem with large CDNs and their returned round-robin IP addresses. So while useful, this new feature is not a panacea for preventing blocking of desired hosts.
With the ground rules established, let's look at how you can configure the new feature in Snort.
First you will need to create the required firewall aliases under FIREWALL > ALIASES. In the example screenshot below, I have created several aliases. You can see that one of them, the "Workstations" alias, is actually what I call a nested alias. It contains other aliases as its content. Those other aliases then have their own IP addresses they resolve to. Notice that the "Windows_PCs" alias and the "Linux_PCs" alias each consist of normal IP addresses. However, the "Search_Engines" alias is actually a FQDN alias whose content is "www.google.com" and "www.yahoo.com". These domains names will be resolved to IP addresses by the
filterdnsdaemon in pfSense.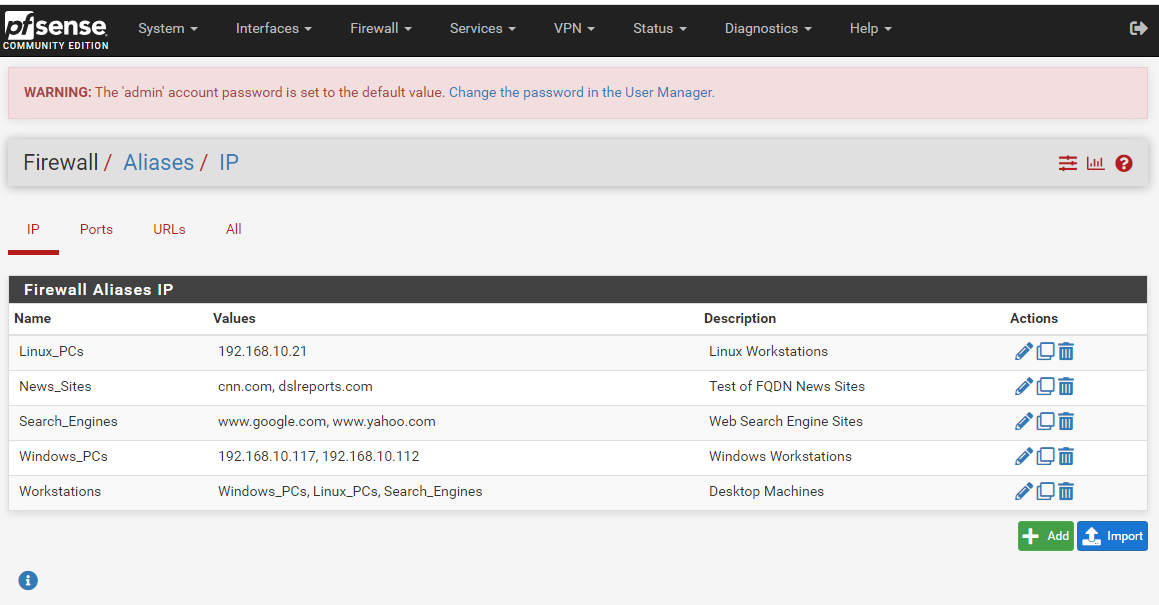
Below is a screenshot from the DIAGNOSTICS > TABLES tab in pfSense showing the "Workstations" alias selected for display after creating, saving and applying changes from the firewall aliases tab.
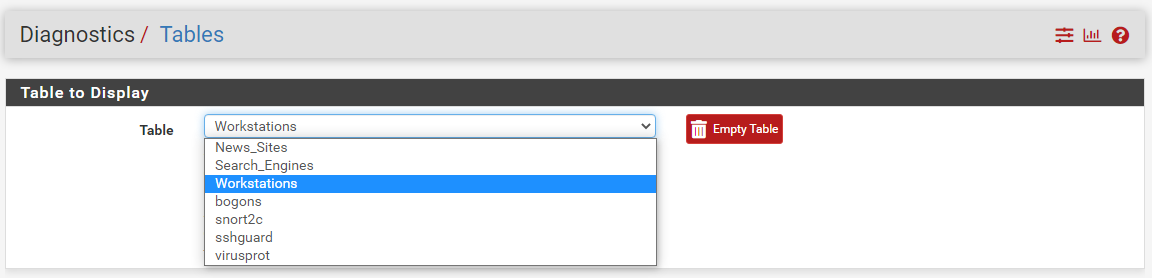
And below is a screenshot of the content in the "Workstations" table. Notice everything is now an IP address, including the
www.google.comandwww.yahoo.comdomain names. Some of the IPv4 addresses, and all of the IPv6 addresses, shown are from the two FQDNs.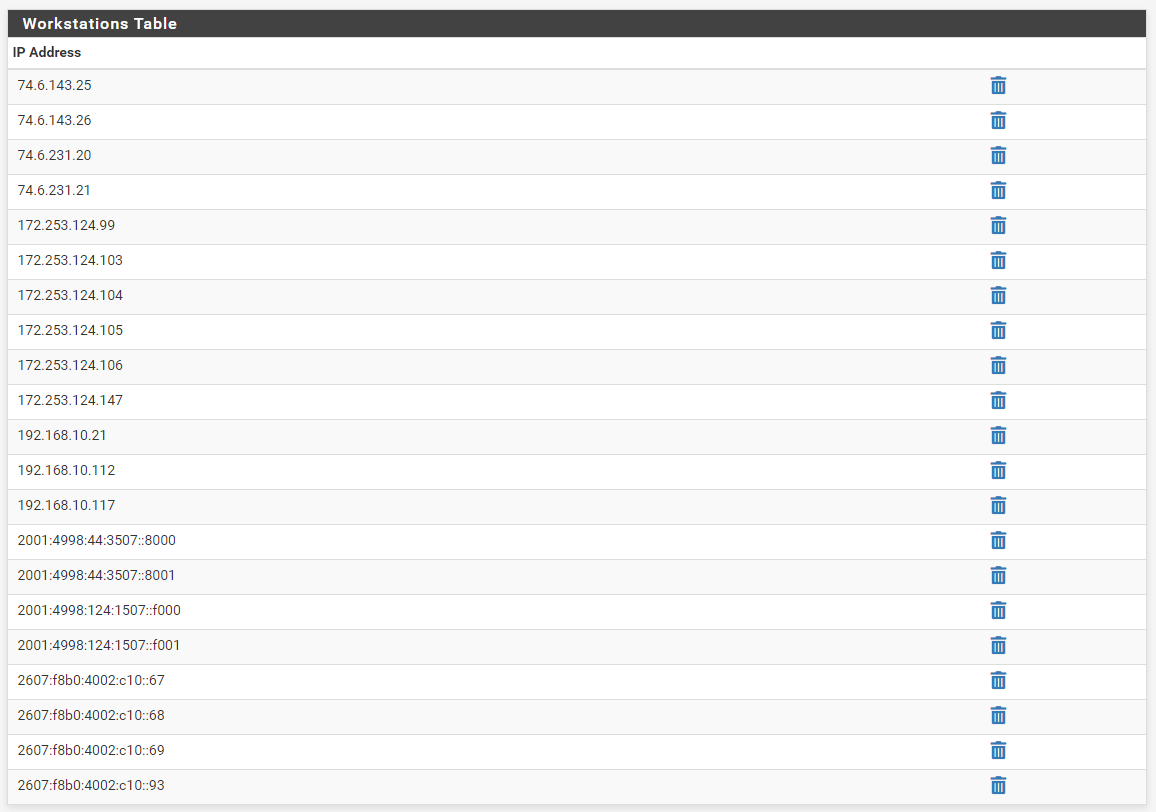
Now that the aliases have been defined, here is how to add them to a Snort custom Pass List. Below is the PASS LIST tab from a test Snort instance.
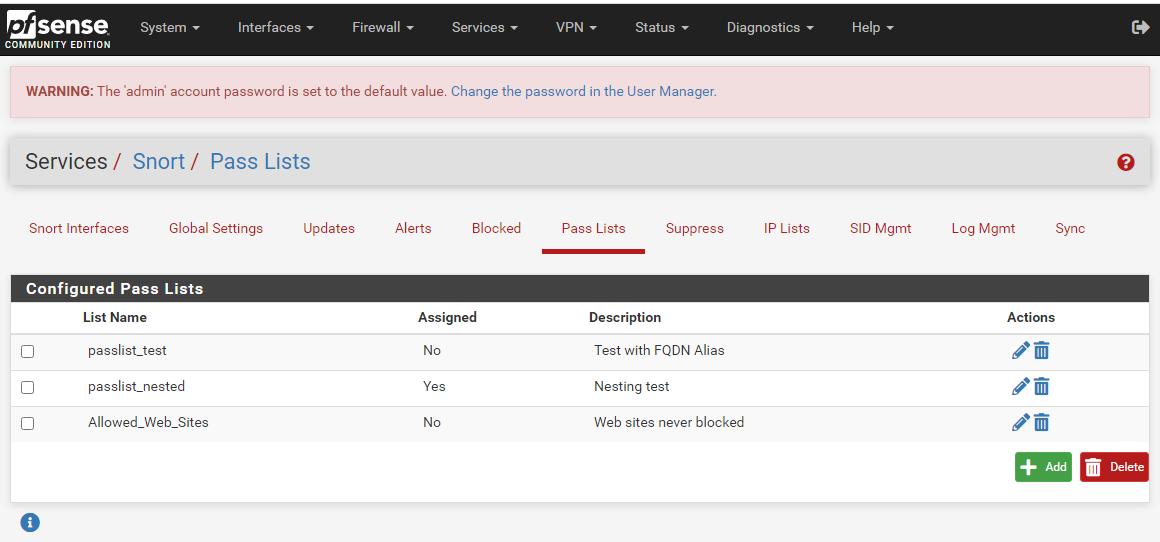
Notice in the image above that the "passlist_nested" Pass List is currently showing as assigned. That means it is selected in the Pass List drop-down selector on the INTERFACE SETTINGS page for a configured Snort instance. On this particular test firewall the Pass List is selected for the LAN interface.
Clicking the Edit icon (or double-clicking on the row) for the "passlist_nested" list opens the Pass List Edit window shown below.
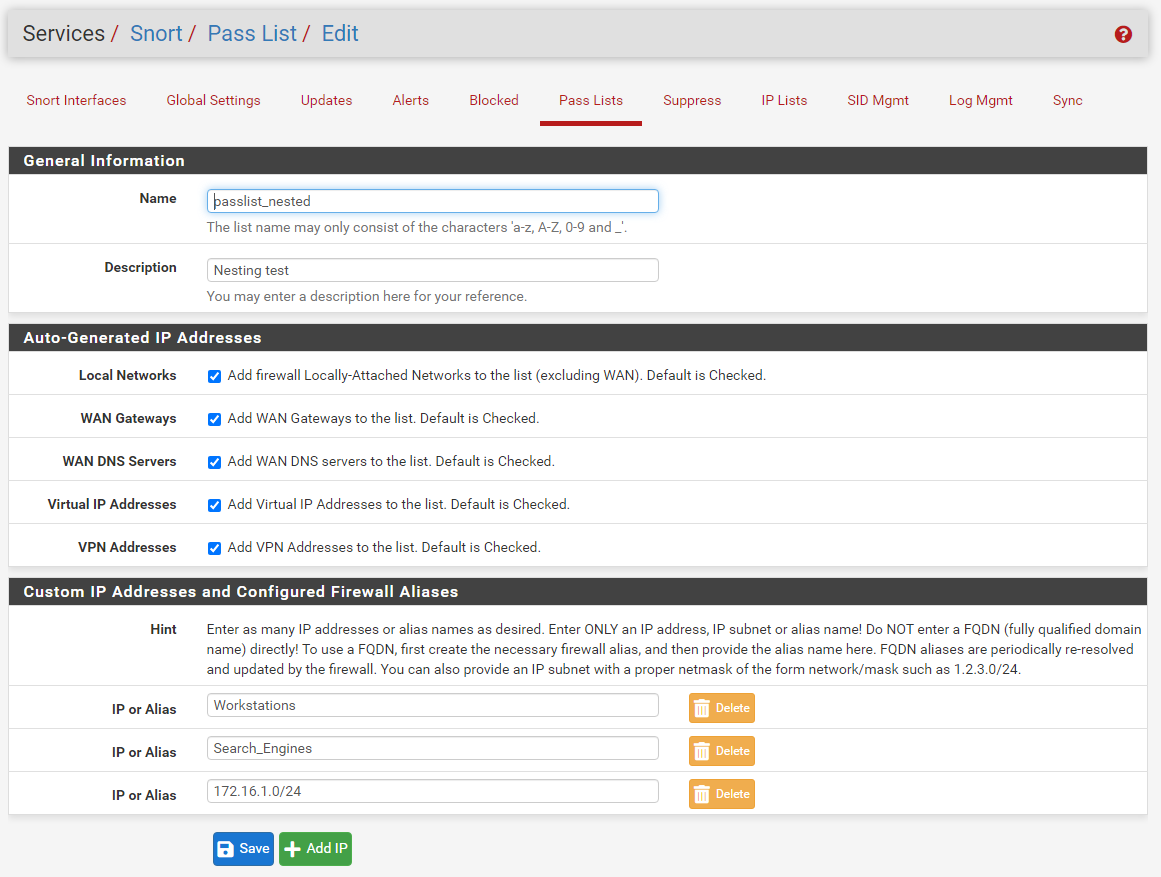
Notice in the screenshot above I've taken the default choices for the Auto-Generated IP Addresses. I have also added some additional custom entries to this Pass List. I've added two aliases - the "Workstations" alias and the "Search_Engines" alias. I also added an IP subnet (the 172.16.1.0/24 network).
To see the values actually written to the physical Pass List file used by Snort on the LAN interface, I went to INTERFACE SETTINGS for the LAN and then in the Pass List selector parameter (with "passlist_nested" selected in the drop-down), I clicked the View List button. A screen capture of that output is shown below.
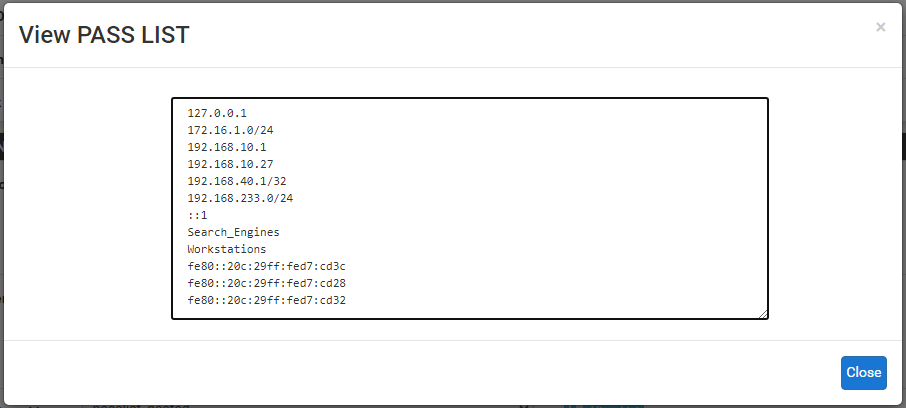
If you look, you will see that all of the IP and alias values specified by the settings on the Pass List Edit screen are there. There is the custom 172.16.1.0/24 subnet I added, along with the "Workstations" and "Search_Engines" aliases. Those two aliases are actually the names for corresponding
pftables in pfSense. During runtime, as it examines each alerting packet, Snort will compare the source and destination IP addresses of the alerting packet to the IP addresses shown in the list immediatley above. For the two aliases, Snort's custom pfSense blocking module will query thepffirewall engine via anioctl()system call to check if the packet's source and/or destination IP addresses are contained in either of the "Workstations" or "Search_Engines" tables. And every 5 minutes thefilterdnsdaemon on the firewall will update the IP addresses contained in the alias tables for "Workstations" and "Search_Engines" (and any other dynamically updated aliases). Thus the Snort Pass List will stay reasonably up-to-date with the actual IP addresses in the alias. -
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on