WireGuard VPN providers that support pfsense
-
@p1erre said in WireGuard VPN providers that support pfsense:
@n8rfe Give Mullvad a try https://mullvad.net/en/servers/
Pretty easy to setup with pfsense and there is also a reddit thread https://www.reddit.com/r/PFSENSE/comments/l1uqkb/wireguard_works_with_mullvad/
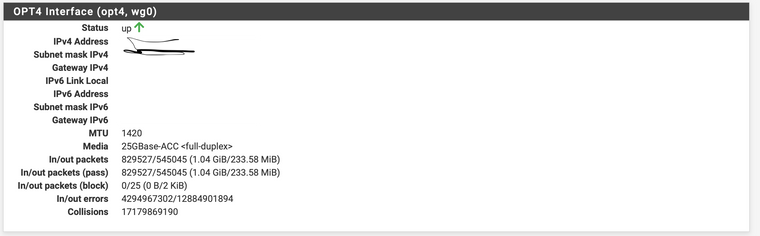
I am using a SG3100 W mullvad. can you please pass some traffic and see under interfaces of the bottom numbers ever change? ( specifically ran a 4k video to 1gb of traffic for the screen shot as you can see) see my first screen shot... the numbers are exactly the same... I wonder if this is a bug?
-
@bcruze I'm running a 5100 and see the counters increasing. No issues that I can see there. I also run the widget on the dashboard and it increments too.
-
@gabacho4 said in WireGuard VPN providers that support pfsense:
@bcruze I'm running a 5100 and see the counters increasing. No issues that I can see there. I also run the widget on the dashboard and it increments too.
I am sorry I didn't ask that clearly.
are your in/out packets and
collisions stuck at the numbers both of my screen shots show? -
@bcruze nope. I only have 6 in/out errors and 6 collisions. I seem to get that on all my wireguard interfaces so either it's a bug that I don't really care about, or literally there are some kind of collisions that occur as the connection is being made. Regardless, the service works and works very well. I'm sure Netgate will clean up any issues with the 21.02.x updates.
-
@bcruze There are a lot of Collisions and errors on your setup
here is my interface status
WG0MULLVAD Interface (opt12, wg0) Status up IPv4 Address xx.xx.xx.xx Subnet mask IPv4 255.255.255.255 Gateway IPv4 xx.xx.xx.xx IPv6 Link Local xxxxx%wg0 IPv6 Address xxxxx Subnet mask IPv6 64 Gateway IPv6 xxxxx MTU 1420 Media 25GBase-ACC <full-duplex> In/out packets 3277492/1965393 (2.16 GiB/849.86 MiB) In/out packets (pass) 3277492/1965393 (2.16 GiB/849.86 MiB) In/out packets (block) 108/11 (14 KiB/0 B) In/out errors 6/6 Collisions 6 -
@p1erre said in WireGuard VPN providers that support pfsense:
@bcruze There are a lot of Collisions and errors on your setup
here is my interface status
WG0MULLVAD Interface (opt12, wg0) Status up IPv4 Address xx.xx.xx.xx Subnet mask IPv4 255.255.255.255 Gateway IPv4 xx.xx.xx.xx IPv6 Link Local xxxxx%wg0 IPv6 Address xxxxx Subnet mask IPv6 64 Gateway IPv6 xxxxx MTU 1420 Media 25GBase-ACC <full-duplex> In/out packets 3277492/1965393 (2.16 GiB/849.86 MiB) In/out packets (pass) 3277492/1965393 (2.16 GiB/849.86 MiB) In/out packets (block) 108/11 (14 KiB/0 B) In/out errors 6/6 Collisions 6YES. but those numbers show up immediately upon the creation and connection of the session
you both confirmed the same as you can see just different numbers.
-
@p1erre said in WireGuard VPN providers that support pfsense:
Mullvad
Excellent find. Thanks for this. I am in the process of testing them.
-
@gabacho4 where do we get the public/private key from with their services?
-
@beachbum2021 said in WireGuard VPN providers that support pfsense:
@gabacho4 where do we get the public/private key from with their services?
Click the download button scroll down and click wireguard
-
I have Torguard up and running.
-
@n8rfe I've used several succesfully. The only one that's a real pain is Nord as they regard their config as secret squirrel.
Mullvad
VPN.AC
ExpressVPN -
I've been using IVPN for several years and have been happy with them. They do support Wireguard and I have transitioned my pfSense to use Wireguard exclusively with them. I've posted screenshots of how I got it configured in this post https://forum.netgate.com/topic/160378/wg-not-routing-or-sending-traffic
-
@hypnosis4u2nv said in WireGuard VPN providers that support pfsense:
I have Torguard up and running.
Any chance you could share how you got this running? I've been trying to get this in place but the peer won't connect.
-
@ertnec Go to the config generator, select tunnel type - wireguard, choose your server location and enter your VPN log in details.
Go to pfsense VPN->Wireguard->Add Tunnel. Check Enable interface, add description, and go down and Generate New Keys.
Go back and enter those keys in the Torguard config generator and hit generate config button. You should have a config printed out in the box. Copy the address under interface and plug that into address in pfsense wireguard tunnel. Listen port should be listed as 51820 so enter that in the tunnel. Click add peer on the bottom in the wireguard setup.
The peer configuration is being copied from the config that was generated and plugged into all applicable fields in the tunnel peer settings. Leave everything else blank.
Create and enable your Wireguard interface. Create a firewall rule under the wireguard interface to allow any.
Add your NAT rule for WAN.
Then add any policy based rules to the firewall.
Done.
-
@hypnosis4u2nv said in WireGuard VPN providers that support pfsense:
@ertnec Go to the config generator, select tunnel type - wireguard, choose your server location and enter your VPN log in details.
Go to pfsense VPN->Wireguard->Add Tunnel. Check Enable interface, add description, and go down and Generate New Keys.
Go back and enter those keys in the Torguard config generator and hit generate config button. You should have a config printed out in the box. Copy the address under interface and plug that into address in pfsense wireguard tunnel. Listen port should be listed as 51820 so enter that in the tunnel. Click add peer on the bottom in the wireguard setup.
The peer configuration is being copied from the config that was generated and plugged into all applicable fields in the tunnel peer settings. Leave everything else blank.
Create and enable your Wireguard interface. Create a firewall rule under the wireguard interface to allow any.
Add your NAT rule for WAN.
Then add any policy based rules to the firewall.
Done.
You know what, I'm an idiot... It was working fine, I'd just not interpreted the output of
wgcorrectly. Once I'd properly set it to the vlan which uses it (so just swapping over ovpnc1 for wg0 on the gateway interface), everything was spot on. Although what wasn't clear was that in order to get port forwarding working correctly, you need to first request/configure the range within TG itself, then generate a new config. I'd generated the config then requested the port forwards.Compared to OpenVPN, peak speeds seem far more consistent (holding steady now at around 55mbps which is the upper limit of my current connection compared to ranging from 45-55), although CPU load has increased from an average of 40% to around 55%.
-
@ertnec Glad you got it working. The only bugs I am seeing is that the traffic graph doesn't display any data and the RTT latency data is ridiculously low so probably wrong. Could be an issue if you're running a gateway group and it's choosing gateways based on latency.
-
@hypnosis4u2nv the latency is low because the gateway is set to ping itself. You’ll want to go to System -> Routing, then edit the gateway and set it to ping an alternate ip like 8.8.8.8 or whatever. Them you’ll get a real gauge of your latency.
-
windscribe also has wireguard support.
-
@hypnosis4u2nv said in WireGuard VPN providers that support pfsense:
@ertnec Glad you got it working. The only bugs I am seeing is that the traffic graph doesn't display any data and the RTT latency data is ridiculously low so probably wrong. Could be an issue if you're running a gateway group and it's choosing gateways based on latency.
Ahhh I never noticed the traffic graph reporting incorrectly for the interface where the tunnel is paired! Interesting
-
@gabacho4 Thanks! Just added it and it displays correctly! Duh!